- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE-PIC Automatic Agent - IseExec remote copy failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2017 11:00 AM - edited 02-21-2020 10:40 AM
Hello Team,
ISE 2.3 + Windows 2012 (with all patches).
Manual PIC agent deployment works fine. But not automatic (i have few DC's on which i have not deployed manually, wanted to use automatic deployment).
When trying to deploy agent i got:
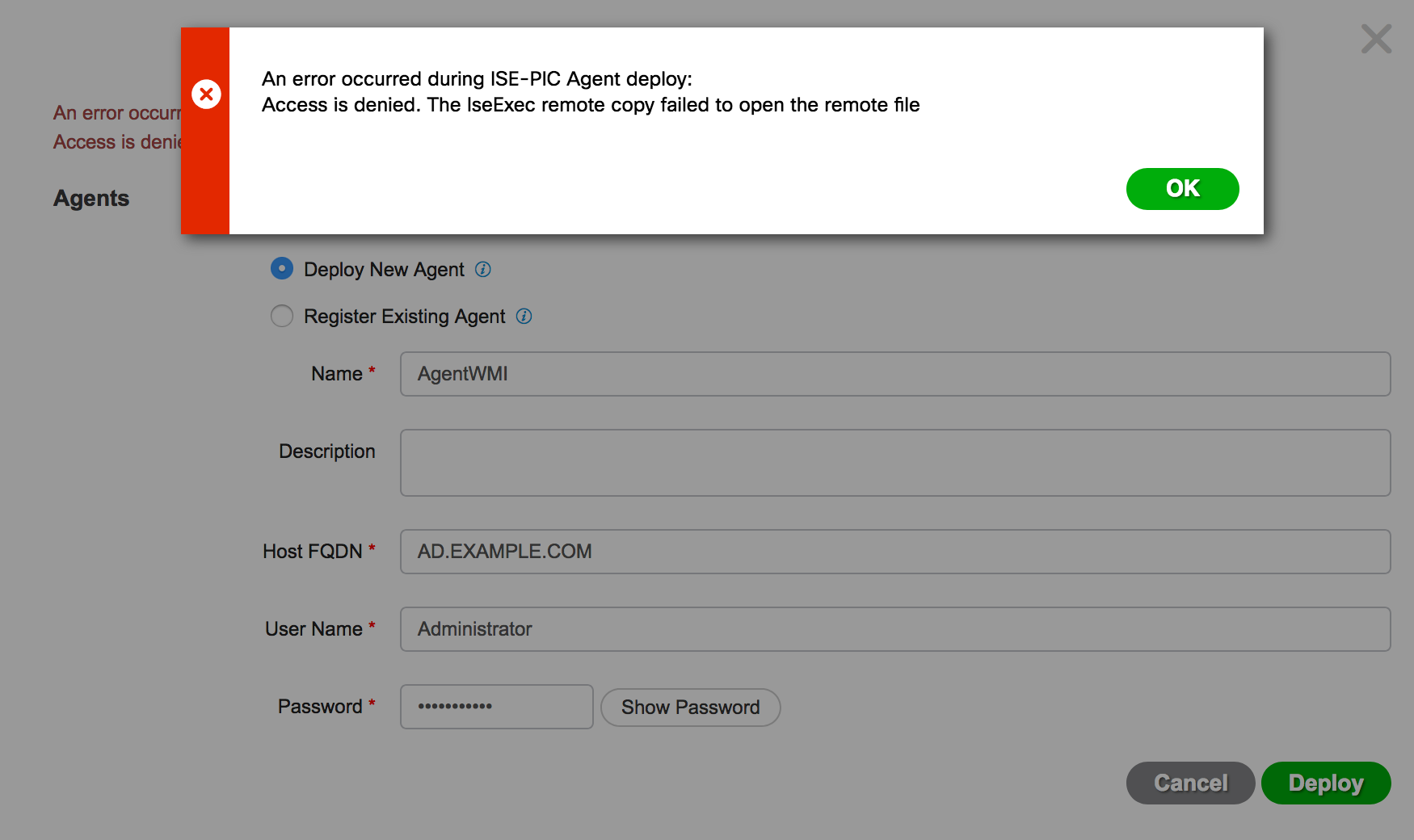
I am using Administrator account will full permissions. I am not sure what protocol is being used for the deployment, RDP is working fine (non secure-domain version).
What am i missing ?
I have followed:
But there is no explanation how the agent is deployed. I do assume not via WMI, because if i would have WMI working i could use option "Config WMI", but that one is returning me:
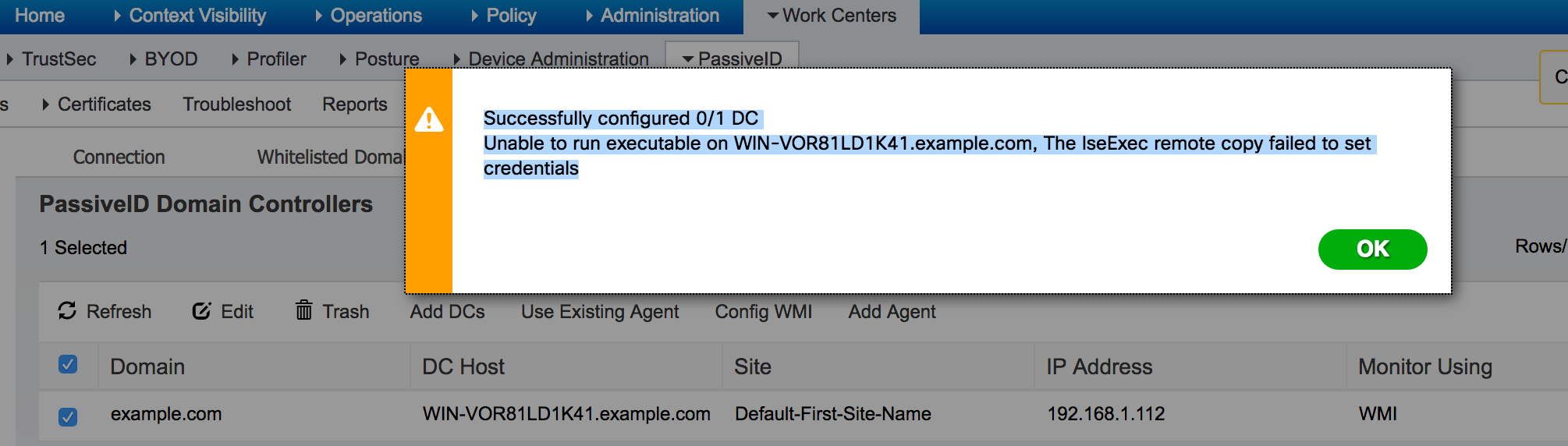
This error as per:
should not happen if i use Administrator credentials (i have used those for both AD join and WMI/Agent deployment).
Sorry for not providing logs/debugs - i hope the have a quick win here, if not will provide more data/spend more time on this.
Thanks,
Michal
Solved! Go to Solution.
- Labels:
-
Passive Identity
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2017 07:38 AM
PassiveID uses ISEexec (based on PSexec) to remotely copy the agent installer and run it. For that to be successful, you need to make sure the account you are using has domain admin priviledges and nothing less. Also, make sure those credentials are saved in the PassiveID configuration. Since you are using ISE and not ISE-PIC, you have the option to save the credentials during join time to the domain. ISE-PIC does this for you automatically while ISE does not. If you have the above correct and are still running into the same error, please open a TAC case to further troubleshoot.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2017 11:29 AM
Can you put this under the pic Community?
https://communities.cisco.com/docs/DOC-72047<https://communities.cisco.com/docs/DOC-72047?mobileredirect=true>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2017 11:38 AM
Hi Jason, done ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2017 07:38 AM
PassiveID uses ISEexec (based on PSexec) to remotely copy the agent installer and run it. For that to be successful, you need to make sure the account you are using has domain admin priviledges and nothing less. Also, make sure those credentials are saved in the PassiveID configuration. Since you are using ISE and not ISE-PIC, you have the option to save the credentials during join time to the domain. ISE-PIC does this for you automatically while ISE does not. If you have the above correct and are still running into the same error, please open a TAC case to further troubleshoot.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2017 12:17 PM
Thanks Tim, it looks like i had all of this correct. Need to gather all logs and open TAC case then. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2017 03:53 PM
I'm having the same error here with a customer. We're using the Domain Admin account and receive the same error. At a debugging level, we see:
12/12/2017 14:36:34,WARNING,139712584996608,[LwKrb5GetTgtImpl ../../lwadvapi/threaded/krbtgt.c:329] KRB5 Error code: -1765328378 (Message: Client not found in Kerberos database),lwadvapi/threaded/lwkrb5.c:892
No idea how to correct this, followed all the guides and enabled debugging for the relevant logs but it all seems to indicate that the user we're using doesn't exist, which isn't possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2017 11:32 PM
Yep Esiquio, multiple others do have similar issue, sorry but did not have yet time to troubleshoot (and open a TAC case). If you will have a chance to solve it please update this thread. Thanks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2017 02:18 PM
Submitted a TAC case yesterday, waiting for a response. I'll definitely update this post once I find out the exact source of whats going on. We've troubleshot the issue pretty extensively so far, going as far as manually running the executable that was sent to the ADMIN$ on the Domain Controller, and getting a general error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2017 12:38 PM
Please submit a TAC case as Tim suggested for further troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2020 08:59 AM - edited 05-07-2020 08:14 AM
Adding my experience with a similar problem and frustration with vague responses from ISE. I'm adding this here as it's one of the top results when you search for my ISE error.
Environment:
2012 r2 and 2016 DC's
ISE v2.6.0.156 patch 3
Errors:
"Failed to run executable on <2016 DC FQDN>, Error: unknown root cause, iseExec execution failed."
At first I was able to 'Configure' and 'Test' the 2012R2 DC's but the WMI deployment would fail with the same error as the 2016's.
On the 2012r2 DC's i saw IDs 7045 and 7036 in Event Viewer that the iseExec service installed, started then stopped OK. But ISE would fail with the above error.
I opened a TAC case, was told to run through more manual pre-reqs from earlier versions of ISE. Before i did that, i tried one last thing.
All I did was reset the password in AD for the service account I had created for this task with no special characters .
So, say the pw was: Example$P@55Word^Here
I changed it to: ExamplePa55WordHere
and everything started working. Hope this helps someone.
*EDIT: Apparently this stemmed from having a $ in the password and outlined in this bug https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs14297
This has be resolved as of 2.6.0.156-Patch5, though i haven't personally tested it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

