- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Posturing w/ FlexVPN Certificate-Based Client Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Posturing w/ FlexVPN Certificate-Based Client Authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 07:48 AM
Has anyone configured this before? I am trying to create a similar user experience when users connect to the VPN as they do when connecting to the wired/wireless network. I am doing EAP-Chaining w/ Posturing for the wired/wireless - when a user logs into windows they (and the device) automatically authenticate to the network, and posture check is performed before being allowed full network access. I would like to have this same experience when users take their corporate laptops home, and connect to the VPN.
Because EAP-FAST is not supported on VPN, I am using certificates for client authentication along with enabling auto-connect in the anyconnect profile. Which this is working however I am running into issues when trying to add posturing into the mix; however I am not sure fixing these would still allow this to work.
The first issue is getting the posture module to detect/connect to ISE - i don't believe my platform supports redirect-acl (3925). If I manually connect to the client provisioning portal I can attempt to login, but for some reason authentication is failing.
The second is issue is specific to FlexVPN, and how it performs authorization - I am currently using a generic username to send the authorization request to ISE for the additional session attributes (pool, banner, dns, ect). I have tried using a name-mangler to extract the specific username from the certificate, but for some reason it extracts a 'null' value even though I can clearly see the email in the IKE ID.
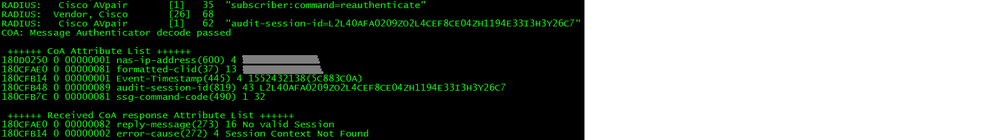
My concern is that the router isn't maintaining or associating the session-id it uses for the flexVPN authorization with the user's connection. Even if I could get the posture module to communicating with ISE I am afraid the the CoA for the user would not work. Something else that is making me lean to this theory is that if I attempt a manual CoA from ISE for my generic user's session I get a Nack "No valid Session, Session Context No Found" back from the router.
Anyone tried this and got it working, or have any thoughts?
-Thanks
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 08:57 AM
I've never used posture with FlexVPN but I've used FlexVPN a lot. Please post your IKEv2 configuration, a screenshot of your certificate with the value you want to extract and a screenshot of the ISE configuration and I'll have a look at the second issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 10:53 AM
Thanks for the response - what specific ISE config would you like to see?
FlexVPN configuration
aaa group server radius LAB-ISE01-RADIUS
server-private x.x.x.x key xxxxxx
ip vrf forwarding MGMT
!
aaa authorization network FLEXVPN-AUTHOR group LAB-ISE01-RADIUS
aaa accounting network FLEXVPN-ACCOUNTING start-stop group LAB-ISE01-RADIUS
!
aaa server radius dynamic-author
client x.x.x.x vrf MGMT server-key xxxxxx
client y.y.y.y vrf MGMT server-key yyyyyy
!
crypto pki certificate map LAB-FLEXVPN-CERTMAP 10
issuer-name co <domain>
!
crypto ipsec profile LAB-FLEX-IPSEC-PROFILE
set ikev2-profile LAB-FLEX-PROFILE
!
crypto ikev2 name-mangler LAB-AC-USER-MANGLER
email username
crypto ikev2 profile LAB-FLEX-PROFILE
match fvrf LAB-OUTSIDE
match certificate LAB-FLEXVPN-CERTMAP
identity local dn
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint LAB_Wildcard sign
pki trustpoint LAB-CA verify
dpd 30 2 on-demand
aaa authorization group cert list FLEXVPN-AUTHOR name-mangler LAB-AC-USER-MANGLER
aaa accounting cert FLEXVPN-ACCOUNTING
virtual-template 16
!
no crypto ikev2 http-url cert
!
interface Virtual-Template16 type tunnel
ip vrf forwarding LAB-INSIDE
ip unnumbered Port-channel1.416
ip mtu 1460
ip tcp adjust-mss 1360
tunnel mode ipsec ipv4
tunnel vrf LAB-OUTSIDE
tunnel protection ipsec profile LAB-FLEX-IPSEC-PROFILE
!
Certificate attribute to use for authorization
In the debug on the router I see the following error:
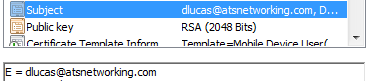
IKEv2-INTERNAL:Name-mangler 'LAB-AC-USER-MANGLER' returning mangled-name 'null' for name-type 3, name-len 135, name_string e=dlucas@atsnetworking.com,cn=<omited the rest>
IKEv2-ERROR:AAA group author request failed
-Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 11:36 AM - edited 03-12-2019 11:47 AM
Ok, so you are extracting "dlucas@atsnetworking.com" from the certificate which is sent to ISE.
Are you authenticating and authorizing? I usually do both, in which case a local ISE would need to be created called "dlucas@atsnetworking.com" with a password of "cisco" unless you specify a custom password under the aaa authorization command.
What configuration in ISE do you have for AuthC and AuthZ?
Also when using your email address for group authorization that isn't going to be scalable for users other than yourself. You should use a value that is common to all certificate issued by your CA, possibly create a new certificate template for the VPN and define a value in the organisation unit, change the name-mangler accordingly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 11:47 AM - edited 03-12-2019 11:49 AM
well, I am attempting to extract that to use for authorization lol - I am getting an error which is preventing the router from sending the auth request to ISE.
My thinking was to extract the email from the certificate and in my authentication policy I would set the 'If Auth Fails' to 'Continue' (because the password won't match like you mentioned, and the authentication is handled by the router via certificate verification), and then perform my authorization based on the user (which contains my posture authorization policies).
-Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 11:55 AM
Check out this example, it's not a remote access VPN but it does demonstrate successfully to extract a username (from OU) using the name-mangler and authorize using ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 12:46 PM
Thanks - yea I can get the name-mangler to extract the CN, but this doesn't contain what I need - I need the email listed, which is clearly present in the certificate - it's like the router isn't looking for the 'e=' field
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 03:24 PM
Instead of "email username" which if it worked would extract "dlucas", you can use "dn common-name" and achieve the same thing, assuming your AD username is "dlucas"
As I indicated earlier if you are doing group authorization all users would need to return the same extracted value, so you would be better of extracting a more generic value from another attribute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 03:53 PM
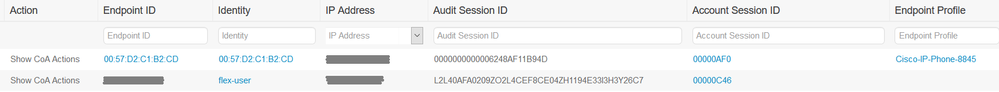
Say I have 10 users all connected to VPN - if I use a generic username (either statically entered or extracted from certificate) ISE would see all 10 of these authentications for the same username - which aside from potentially causing headaches troubleshooting, how would this affect ISE radius sessions? I guess the calling-station-id would be unique for each, which would create a unique session-id?
I guess if this is true that rules out my theory why CoA isn't working...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 04:28 PM
If I switch back to a static username instead of trying to extract one from the certificate this is what my live radius session looks like in ISE:
If I click CoA Actions -> Reauthenticate from here I get the following error on the router:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide