- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE providing both Access-Accept and Access-Reject to ASA for VPN Client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2019 08:23 AM
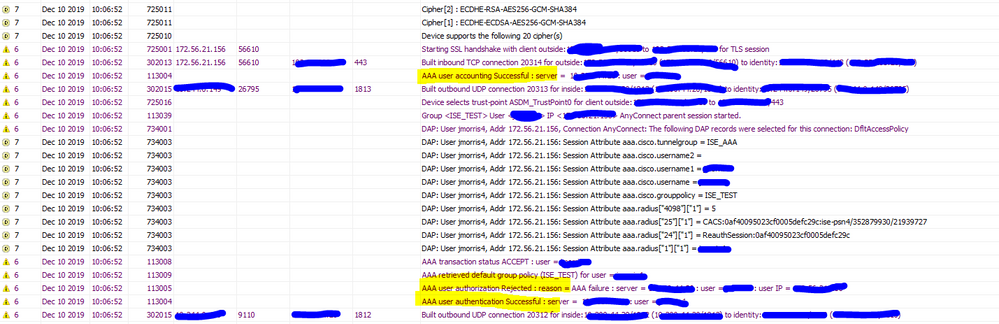
I am currently testing ASA VPN connectivity using ISE as AAA. I'm getting mixed results. If you see in the image below, I am getting a successful authentication/authorization. But then it sends an authentication failure back to the ASA which and the ASA sees an authorization reject. But I still get access to the VPN.
Steps
| 11001 | Received RADIUS Access-Request | |
| 11017 | RADIUS created a new session | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15048 | Queried PIP - DEVICE.Device Type | |
| 15004 | Matched rule - VPN_Authentication | |
| 15041 | Evaluating Identity Policy | |
| 15006 | Matched Default Rule | |
| 22072 | Selected identity source sequence - VPN_Users | |
| 15013 | Selected Identity Source - stjude.sjcrh.local | |
| 24430 | Authenticating user against Active Directory - stjude.sjcrh.local | |
| 24325 | Resolving identity - username | |
| 24313 | Search for matching accounts at join point - stjude.sjcrh.local | |
| 24319 | Single matching account found in forest - adroot.sjcrh.local | |
| 24367 | Skipping unusable domain - ALARIS.LOCAL,Domain trust is one-way | |
| 24367 | Skipping unusable domain - STJU_TN.cernerasp.com,Domain trust is one-way | |
| 24367 | Skipping unusable domain - pacs.stjude,Domain trust is one-way | |
| 24367 | Skipping unusable domain - cernoly.com,Domain trust is one-way | |
| 24367 | Skipping unusable domain - campusnet.local,Domain trust is one-way | |
| 24367 | Skipping unusable domain - sjtn.hosted,Domain trust is one-way | |
| 24367 | Skipping unusable domain - sjtn.healthcatalyst.net,Domain trust is one-way | |
| 24367 | Skipping unusable domain - BIOS.sjcrh.local,Domain trust is one-way | |
| 24323 | Identity resolution detected single matching account | |
| 24344 | RPC Logon request failed - STATUS_WRONG_PASSWORD,ERROR_INVALID_PASSWORD,username@stjude.sjcrh.local | |
| 24408 | User authentication against Active Directory failed since user has entered the wrong password - stjude.sjcrh.local | |
| 22057 | The advanced option that is configured for a failed authentication request is used | |
| 22061 | The 'Reject' advanced option is configured in case of a failed authentication request | |
| 11003 | Returned RADIUS Access-Reject |
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2019 02:11 AM
Hi
You have both authentication-server-group and authorization-server-group under your tunnel-group configuration.
From cisco documentation below:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/access_aaa.html
The default method for authentication and authorization uses the user login credentials.
•Authentication
–Enabled by authentication server group setting
–Uses the username and password as credentials
•Authorization
–Enabled by authorization server group setting
–Uses the username as a credential
Maybe the authorization-server-group is sending your username (minus password) to ISE for authorization.
My current setup for Anyconnect using ASA/ISE just has authentication-server-group configured under the tunnel-group and both authentication/authorization works for vpn clients.
hth
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2019 05:30 AM
Please share the Tunnel-Group (or Connection Profile) configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2019 07:38 AM
tunnel-group ISE_AAA type remote-access
tunnel-group ISE_AAA general-attributes
authentication-server-group ISE_RADIUS
authorization-server-group ISE_RADIUS
accounting-server-group ISE_RADIUS
default-group-policy ISE_TEST
dhcp-server subnet-selection 10.200.x.x
dhcp-server subnet-selection 10.244.x.x
tunnel-group ISE_AAA webvpn-attributes
group-url https://testingurl enable
tunnel-group webvpn type remote-access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2019 09:42 AM
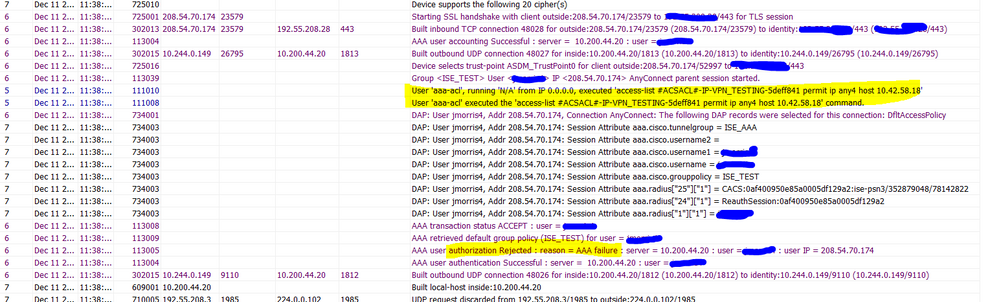
It's just weird. I feel like I am successfully being authorized because I added a DACL for testing and it gets applied successfully. But I see in the ASA logs that authorization was rejected and I see the two log entries in the ISE live logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2019 02:11 AM
Hi
You have both authentication-server-group and authorization-server-group under your tunnel-group configuration.
From cisco documentation below:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/access_aaa.html
The default method for authentication and authorization uses the user login credentials.
•Authentication
–Enabled by authentication server group setting
–Uses the username and password as credentials
•Authorization
–Enabled by authorization server group setting
–Uses the username as a credential
Maybe the authorization-server-group is sending your username (minus password) to ISE for authorization.
My current setup for Anyconnect using ASA/ISE just has authentication-server-group configured under the tunnel-group and both authentication/authorization works for vpn clients.
hth
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2019 05:41 AM
Thanks, that is interesting. Although counter-intuitive. I did remove the authorization command and tried again, and I no longer get the additional ISE failure. I now get three successful logs in ISE with the following steps...
Session Events
| 2019-12-12 07:36:59.61 | Dynamic Authorization succeeded |
| 2019-12-12 07:36:51.07 | RADIUS Accounting watchdog update |
| 2019-12-12 07:36:49.583 | RADIUS Accounting start request |
| 2019-12-12 07:36:49.575 | DACL Download Succeeded |
| 2019-12-12 07:36:49.574 | Authentication succeeded
|
The ASA does not report a failed (or successful) authorization, but it also does use the DACL I have applied in my ISE authorization policy, so I guess authorization is working.
Thanks, I will continue to test.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide