- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE PSN Node groups and F5 load balancing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 04:09 AM
Hello,
We have an ISE distributed deployment of 8 nodes, distributed as shown below,
| DC-1 | SNS-3695-K9 | Primary Admin Node |
| DC-1 | SNS-3695-K9 | Primary Monitoring Node |
| DC-1 | SNS-3655-K9 | Policy Service Node |
| DC-1 | SNS-3655-K9 | Policy Service Node |
| DC-2 | SNS-3695-K9 | Secondary Admin Node |
| DC-2 | SNS-3695-K9 | Secondary Monitoring Node |
| DC-2 | SNS-3655-K9 | Policy Service Node |
| DC-2 | SNS-3655-K9 | Policy Service Node |
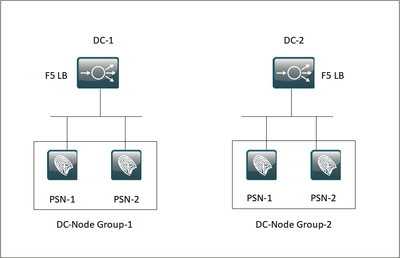
- In DC-1 the Policy Service Nodes are put into DC-Node-Group-1
- In DC-2 the Policy Service Nodes are put into DC-Node-Group-2
For high availability, we have currently put the Policy service nodes behind F5 LB, as shown below,
Customer is suggesting to keep the 4 x PSN behind LB in DC-1 and same 4 x PSN behind LB in DC-2 as per below design.
- Are there any challenges from ISE perspective, when there are PSN node groups configured?
- Will this setup be beneficial from service high availability and session replication perspective?
- Any other caveats that I am missing?
Any help in this regard is much appreciated.
Regards,
Girish
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 11:34 AM
While you can build an architecture like your second image, I would not recommend doing it that way. You do not gain much in the way of HA by load balancing two F5 pools to the same four nodes vs two F5 pools to two nodes each. This just requires more configuration and complexity on the F5 side and creates further challenges when troubleshooting any issues that arise. It's also possible that the DC networking would be much more complicated to get it to work since the F5 is typically deployed inline when load balancing ISE/RADIUS where the F5 acts as a default gateway for the ISE nodes.
The first image is the recommended method for load balancing ISE. It is the simplest and most common method of deployment. It also provided you predicable authentication flow when troubleshooting since you know a request directed at the VIP in DC1 is being handled by ISE PSN nodes in the same DC1. You can perform maintenance without the NADs/endpoints being aware, and you can sustain a DC failure via primary/secondary RADIUS server config on the NADs.
In either scenario you have to configure the F5 the same way, the endpoint authentication sessions have to persist to the same ISE node, responses have to be directed from that specific ISE node back to the NAD. This guide is getting a bit long in the teeth now but the information and design is all still accurate.
https://community.cisco.com/t5/security-knowledge-base/how-to-cisco-amp-f5-deployment-guide-ise-load-balancing-using/ta-p/3631159
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2023 11:34 AM
While you can build an architecture like your second image, I would not recommend doing it that way. You do not gain much in the way of HA by load balancing two F5 pools to the same four nodes vs two F5 pools to two nodes each. This just requires more configuration and complexity on the F5 side and creates further challenges when troubleshooting any issues that arise. It's also possible that the DC networking would be much more complicated to get it to work since the F5 is typically deployed inline when load balancing ISE/RADIUS where the F5 acts as a default gateway for the ISE nodes.
The first image is the recommended method for load balancing ISE. It is the simplest and most common method of deployment. It also provided you predicable authentication flow when troubleshooting since you know a request directed at the VIP in DC1 is being handled by ISE PSN nodes in the same DC1. You can perform maintenance without the NADs/endpoints being aware, and you can sustain a DC failure via primary/secondary RADIUS server config on the NADs.
In either scenario you have to configure the F5 the same way, the endpoint authentication sessions have to persist to the same ISE node, responses have to be directed from that specific ISE node back to the NAD. This guide is getting a bit long in the teeth now but the information and design is all still accurate.
https://community.cisco.com/t5/security-knowledge-base/how-to-cisco-amp-f5-deployment-guide-ise-load-balancing-using/ta-p/3631159
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide