- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Radius live logs are not being displayed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 05:06 AM
ISE version SNS-3615-K9 version 2.7.0.356 Patch 6
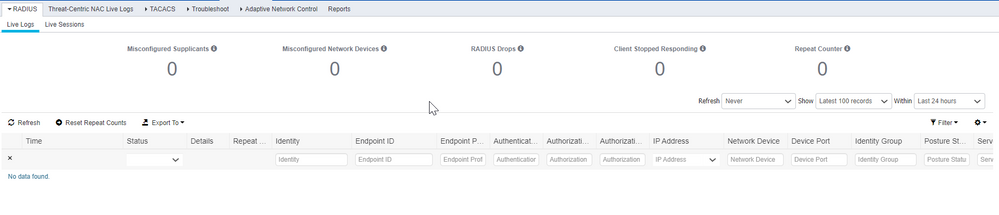
Radius Live Logs are not being displayed, We tried to restart the ISE app and rebooted the administration node several times.
We cant see logs, it's an administration impact. Any other steps I can try to solve this issue? or what else should be checked?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 06:10 AM
Is this an upgrade or a fresh install? If an upgrade, and from a release prior to 2.6, follow these steps (though regenerating the certificates could rectify the issue even if this isn't an upgrade):
1. If you upgrade to ISE 2.6 or newer and do not see any entries in the RADIUS Live Logs, navigate to Administration > System > Logging. You should see that Use ISE Messaging Service for UDP Syslogs delivery to MnT is enabled. This is a new feature that was released in ISE 2.6 and I have run in to this issue. You may need to regenerate these certificates after an upgrade.
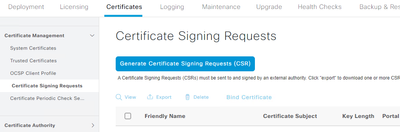
2. To fix this you need to generate new deployment-wide signed certificates. This is a simple process that can be done by navigating to Administration > System > Certificates and choosing Certificate Signing Requests from the left menu
3. Click the button for Generate Certificate Signing Requests (CSR)
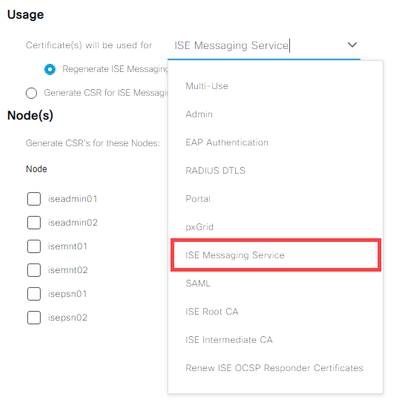
4. In the Usage field, select that the Certificate(s) will be used for ISE Messaging Service
5. Since this is an upgrade, ISE Messaging may not have been enabled previously, you need to select Generate CSR for ISE Messaging Service
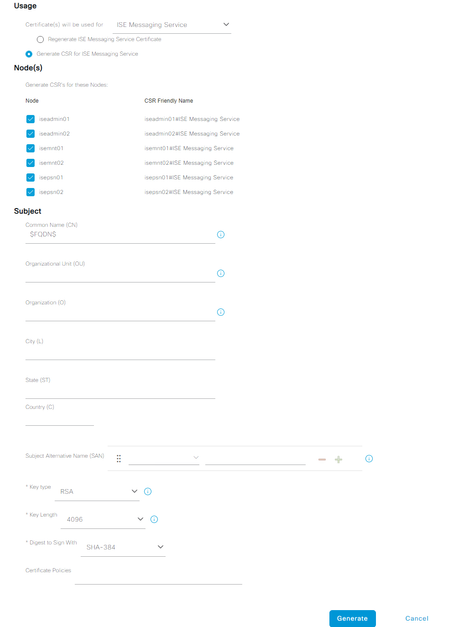
6. Select ALL the ISE Nodes and fill out the certificate fields
Of course, you should follow any guidance and troubleshooting from the Cisco Identity Services Engine Upgrade Guide, Release 2.7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:42 PM
Thank you Charlie, The issue was solved by disabling ISE Messaging Service and we have now some Radius logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 07:00 AM
Great! Now generate the Certificates and re-enable ISE Messaging Service. It's quick and easy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 06:10 AM
Is this an upgrade or a fresh install? If an upgrade, and from a release prior to 2.6, follow these steps (though regenerating the certificates could rectify the issue even if this isn't an upgrade):
1. If you upgrade to ISE 2.6 or newer and do not see any entries in the RADIUS Live Logs, navigate to Administration > System > Logging. You should see that Use ISE Messaging Service for UDP Syslogs delivery to MnT is enabled. This is a new feature that was released in ISE 2.6 and I have run in to this issue. You may need to regenerate these certificates after an upgrade.
2. To fix this you need to generate new deployment-wide signed certificates. This is a simple process that can be done by navigating to Administration > System > Certificates and choosing Certificate Signing Requests from the left menu
3. Click the button for Generate Certificate Signing Requests (CSR)
4. In the Usage field, select that the Certificate(s) will be used for ISE Messaging Service
5. Since this is an upgrade, ISE Messaging may not have been enabled previously, you need to select Generate CSR for ISE Messaging Service
6. Select ALL the ISE Nodes and fill out the certificate fields
Of course, you should follow any guidance and troubleshooting from the Cisco Identity Services Engine Upgrade Guide, Release 2.7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:42 PM
Thank you Charlie, The issue was solved by disabling ISE Messaging Service and we have now some Radius logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2022 07:00 AM
Great! Now generate the Certificates and re-enable ISE Messaging Service. It's quick and easy.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide