- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE TACACS with Smart Card integration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 06:17 AM
My customer have a ISE 2.2 deployment and have a test switch, what they are trying to do as you know is the continuous requests for TACACS+ access to the network from the various support and development teams.
They currently use smart cards in the PC’s as opposed to the need to type in AD credentials on a per authentication basis.
The unique identifier they have in AD which is consistent is the EMPLOYEE ID
The networks team have the ability to query AD but don’t own or control the infrastructure
They would like to know how to configure the policy set such that it cross references the "smartcard details" and the "employee ID" to authenticate the end user into a tacacs user group. Is that possible?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 05:22 PM
Here is a community site that discusses all about 2FA, it includes the document from pragmasys for device administration.
https://communities.cisco.com/docs/DOC-71528
Though the document uses internal user for authorization, this could work with AD as well but needs to be tested.
There is a Cisco AV pair that needs to be created in the shell profile for ISE to get the CN, UPN from PKI for comparison. It is all in the doc.
Look under device administration. There is a dcloud training link as well.
-Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 11:21 AM
Researching this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2017 05:22 PM
Here is a community site that discusses all about 2FA, it includes the document from pragmasys for device administration.
https://communities.cisco.com/docs/DOC-71528
Though the document uses internal user for authorization, this could work with AD as well but needs to be tested.
There is a Cisco AV pair that needs to be created in the shell profile for ISE to get the CN, UPN from PKI for comparison. It is all in the doc.
Look under device administration. There is a dcloud training link as well.
-Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2017 08:36 AM
Also look at this link, Pragma 2-factor SSH for Cisco & Federal Agencies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2017 01:20 AM
I had a follow-up call with the customer just now and here is the screen shot of what they’re trying to do.
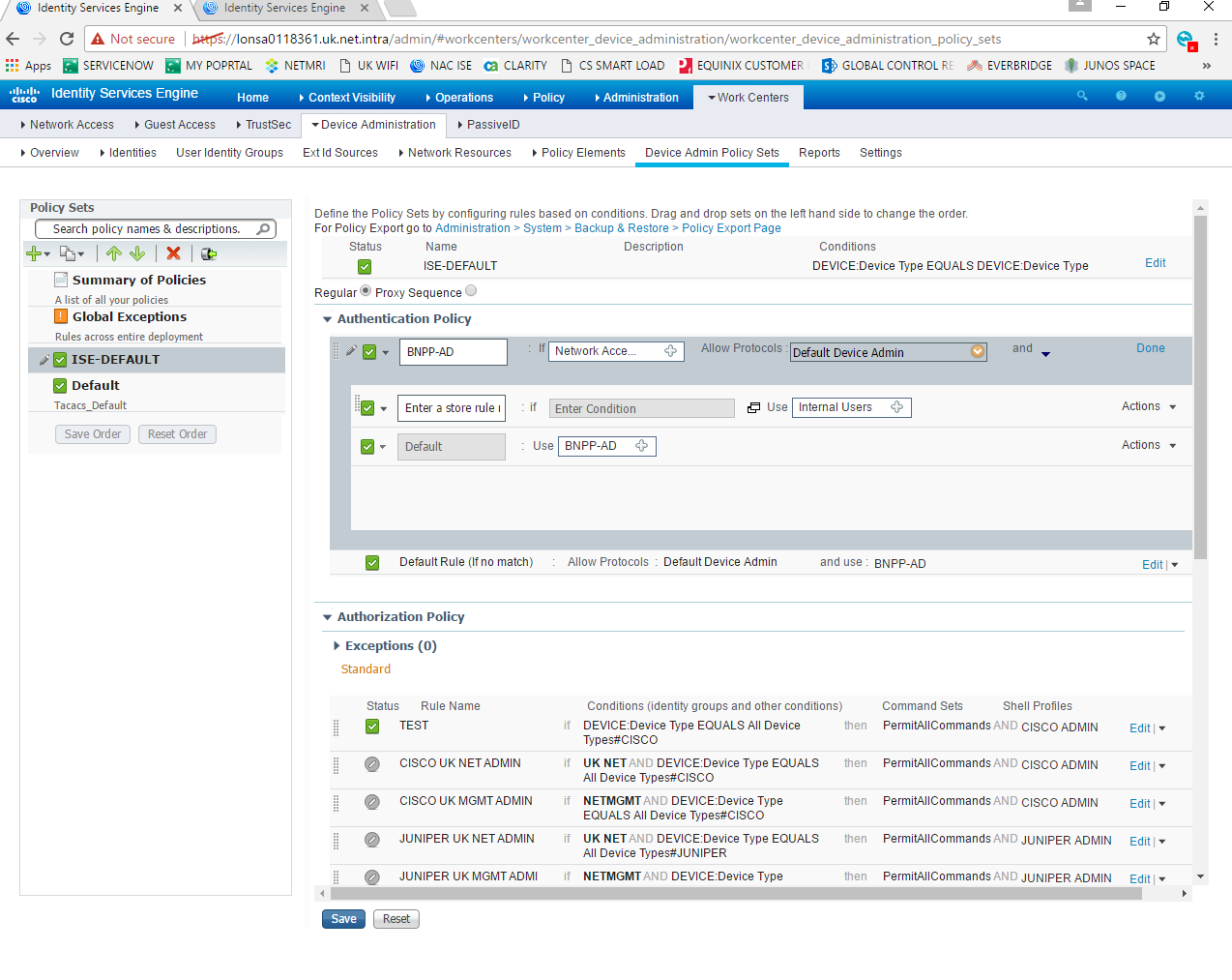
Under the Authentication policy they want to add an attribute pulled out from the AD that has a unique attribute “employee ID”.
Firstly, is it possible to pull in that unique attribute and add that in the authentication policy? I’m sure we could but just not able to find how.
As I had specified in my query above that these users use smart card logins in the PC as a first step and then they get to interrogate AD when they get required privileges.
I understand from your response to the above that " You cannot gather AD group before it is authenticated, so authentication does not support these. Only authorization supports this"
Just to be clear on your response, we can achieve this use-case and it is just that the required AD attribute can be used in the authorization policy but not in the authentication policy as the user needs to be authenticated first before those AD attributes can be used to have shell access, correct?
So, the authorization policy as under could have an AND condition like “employee id=xxx” then permitAllCommands?
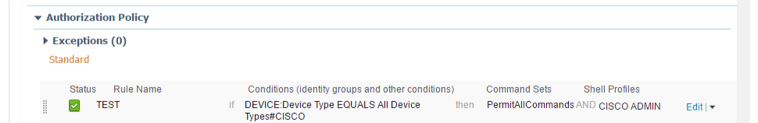
Can you confirm please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2017 01:56 PM
Thank you for posting the follow-up conversation in community site.
Authentication of user using Smart card is done using authentication policy.
If you want to authorize them based on AD attribute, then you need to do it in authorization policy mapping to a Shell profile/command sets.
-Krishnan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

