- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE ver 1.1.2.145 advanced license consumption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE ver 1.1.2.145 advanced license consumption
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 02:25 PM - edited 03-10-2019 07:52 PM
Hello,
I am puzzled with this scenario when it comes to advanced licensing, any insight is greatly appreciated:
I have an XP machine that I am using to access network though ISE authentication and authorization. My authentication is EAP-TLS with machine authentication to simulate company asset. Everytime the XP station connects, ISE consumes a Base license and an Advanced license. Why?? I am note using the profiled group, posture assessment, nor even onboarding in my Authz policy.
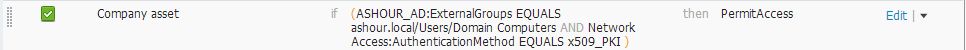
Here is the authorization rule:
Here is the licensing page:
base advanced
1/20 | 1/20 |
Here is the only active session from active session report:
xp-test.ashour.local
00:22:FB:1A:59:C2
10.30.30.117
dot1x
EAP-TLS
NotApplicable
N/A
WindowsXP-Workstation
Running
ise
And here is the live authentication:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2012 06:01 PM
Please provide a screenshot of your authorization policies.
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 09:09 AM
Tarik,
Thank you for responding. Here is screenshot of the authz rules, My device is hitting the third one from top per my previous note:


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 09:12 AM
Please send me a screenshot of your endpoint. Is ot statically assigned to the endpoint group IOS devices?
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 09:22 AM
No, it is not part of the iOS devices which is a static group. It it part of the profiled workstation group. The rule I am hitting is the one above the iOS devices rule. The name of the rule is company assets.
Here are some screenshots of the endpoint attributes:




- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2012 07:30 PM
Hi,
Please make sure that the profiling is disabled for this node, it seems as if the radius probe and the user agent is learned via the http probe.
It also seems as if you are hitting this bug I understand the description doesn't line up but you may want to have TAC clarifiy if this isnt experience on authenticating networks:
Tarik Admani
*Please rate helpful posts*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2013 09:11 AM
Please disable the profile and posturing features in ISE and see the result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2014 11:07 AM
What if you need to use profiling for a subset of the endpoints and the rest use the base license only? Say I have 100 advanced and 500 base licenses? Even when I statically put devices in a static group, it still takes advanced licenses...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2014 02:44 AM
Just profiling the devices would not consume the license, it would consumed when you assigne authorization policies using the profiling data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2014 08:45 AM
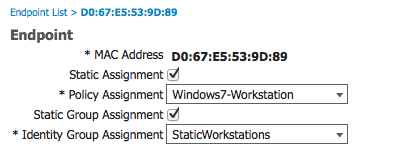
That is what I understand. I am trying to understand why static rule attached here consumes an advanced license as the endpoints are statically added to iOS asset identity group. no profile info is used to authorize. I am still seeing this behavior with 1.2 deployment too. can you help me understand why is this the case? Not if I statically assign it to unknown profile it does not consume advanced license which i do not consider a feasible solution.
Thank you,
Fadi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2014 11:25 AM
Your rule for company assets checks for posture compliance (nac) "Session:Posture Compliance EQUALS Compliant", this is an advanced feature, and requires a license for each device that matches your "Company Assets" rule.
Jan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
