- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE with LDAP using PEAP or MSCHAPv2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:05 AM
Hi Team,
I have a customer using LDAP and RADIUS using PEAP and MSCHAPv2 protocols.
They are evaluating ISE but, using ISE with LDAP is not supported PEAP or MSCHAPv2.
The customer is asking us for a reason, what is the reason why ISE does´t support this protocols ?
Is in roadmap this ? is going ISE to support them ?
Please your help in this question.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2018 03:59 AM
Its mainly due to planning and priority.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:15 AM
I am not sure ,where you read that LDAP and these protocols are not supported ??
I am not tested this but i think it might work just you must create a New Identity Source Sequence
Where you will use AD and LDAP_AD

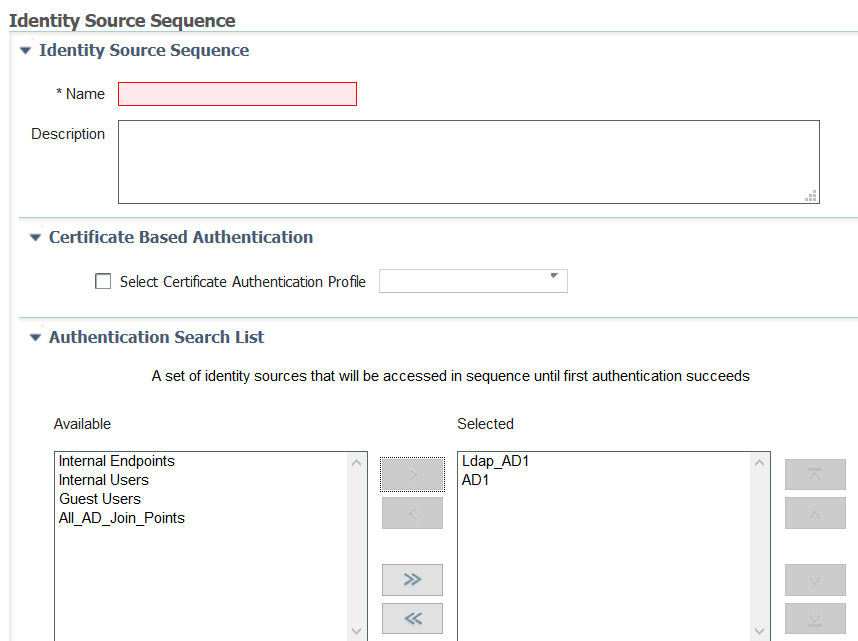
And use it in authorization policy . In authentication use protocols that you need for your deployment.
And i saw one more thing https://bst.cloudapps.cisco.com/bugsearch/bug/CSCul55352/?rfs=iqvred
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:22 AM
Sorry for confusion in the note, ISE support LDAP, but ISE will not support PEAP and MSCHAPv2 with LDAP, you can see the Table 2 "Authentication Protocols and Supported External Identity Sources" in the following link:
The customer´s question is Why and if we have any roadmap for that ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:32 AM
we do not discuss roadmaps in this forum.
please contact your Cisco representative for additional information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:34 AM
Thanks Danny, sorry for roadmap question, But, is there any reason why ISE don't´s support specific Authentication protocols such as PEAP and MSCHAPv2 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 03:26 PM
The way I understand it, it's a technical limitation of how the passwords are stored in the LDAP "database".
You can perform ASCII/PAP authentication to an LDAP directory (because the password that is sent in the auth request is simply a string comparison with the plain text password stored in the LDAP directory). But you cannot perform CHAP etc because there is neither a simple password sent by the client, nor is there a simple password stored on the external directory. E.g. in AD, the client and server perform a handshake protocol, hence the name Challenge-Handshake Authentication Protocol (I don't completely understand it - google it) and this is where the complexity comes in.
Have a read of this too
Deploying RADIUS: Protocol and Password Compatibility
If you want the real gory details (actually an excellent explanation by a somewhat militant sounding Alan de Kok (FreeRadius dev) then check this out Users - Chap auhtentication against LDAP
Having said that, Aruba Clearpass appears to support this. LDAP Authentication Source Configuration - so maybe the technical argument is an old one.
It's confusing for sure ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2018 03:59 AM
Its mainly due to planning and priority.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 02:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 02:49 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2018 02:01 AM
Thanks Arne, Danny for your answers.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

