- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Issues in PEAP Authentication--Cisco ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 04:30 AM - edited 09-10-2018 04:42 AM
Dear Community,
We are facing issues in the below setup.
PEAP
clients--} WLC ---Cisco ISE---AD
MSCHAPv2
We have used Private CA certificates to all our local machines and its getting authenticated using validate certificate options in windows property. In this scenario, if users trying there on BYOD devices also with domain account , its getting authenticated.
Kindly help us how to get rid of that ,and our requirement is to achieve windows/AD based authentication with certificate.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 07:22 AM
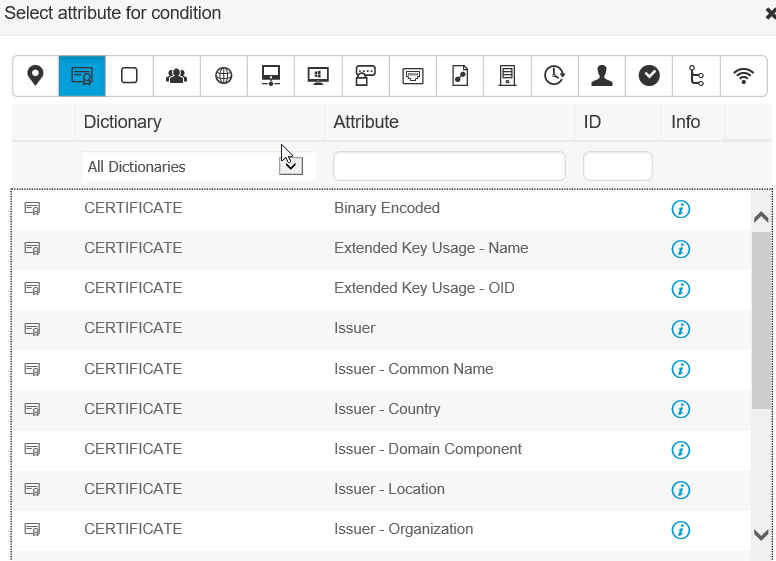
I was thinking about the issue you have and you probably are not requiring a certificate in the authentication policy. Create a library condition which matches the certificate, and then add that to the policy. Then, a certificate will be required.
Thanks,
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 04:41 AM
If you use different certificate for BYOD they will never be authenticated .
But i assume you use same certificate for BYOD too .
In mine deployment i dont have BYOD but all machines in domain are authenticated by certificate .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 04:42 AM
I forgot please see here https://community.cisco.com/t5/security-documents/cisco-ise-byod-deployment-guide/ta-p/3641867
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 04:49 AM
Ognyan,
Thank you for your comments. But please note certificates are deployed in machines only and not through BYOD.
We are using MS PEAP (MS CHAP v2) with Validate Client certificate on the laptop. I want to restrict only the clients with cert installed to connect to the SSID. What should be my ISE Authentication and Authorization policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:02 AM
Under your authentication rules only allow EAP-TLS or under authorization
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:32 AM
Authorization rule
If SSIDNAME and EAP-TLS then permit access
Otherwise if SSIDNAME and PEAP then redirect them to HTML page or deny access
It’s still not clear exactly what you’re trying to accomplish if you can’t just restrict SSID but don’t allow anyone without a certificate to use it
There are some examples in the BYOD guide mentioned before of similar rule configurations and screenshots
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:58 AM
Jason ,
Thank you for your comments. Please note this
We are not allowed to change the authentication requirement as the SSID is for global users ,and it has to connect to their laptops provided the required certificate is installed. The hindrance is if any employee uses his domain credential to his personal device, it will connect even though client doesn't have certificate.
At this moment we cannot use EAP-TLS , but only on PEAP with certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:32 AM
What shown in your doc is the client-side settings and the server certificate validation is up to the clients.
To limit what clients to authorized on, please see Slides 343 ~ 379 of Reference Presentation from Advanced ISE Services, Tips and Tricks - BRKSEC-3697
Event:2018 Orlando
Craig Hyps, Prinicipal Technical Marketing Engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:28 AM
have you tried connecting BYOD/personal devices to network using domain accounts and ignoring the security prompt in your deployment?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:01 AM
Thanks,
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:25 AM - edited 07-25-2018 05:26 AM
Hello Alex,
Thank you for your comments, please clarify how to remove specifically for mobile accounts if we are using AD based authentication.
We dont want machines without certificates to connect to the network,currently there is only security prompting happening ( if users give domain account in their mobile), where as it should work normally if using laptops with certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 06:04 AM
2. Enter the policy that you are using for authentication, click on the > sign.
3. Look at the authentication policy.
4. If there is not a username and password authentication policy, you may have a default policy setup that you need to look at.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 07:22 AM
I was thinking about the issue you have and you probably are not requiring a certificate in the authentication policy. Create a library condition which matches the certificate, and then add that to the policy. Then, a certificate will be required.
Thanks,
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 03:00 PM
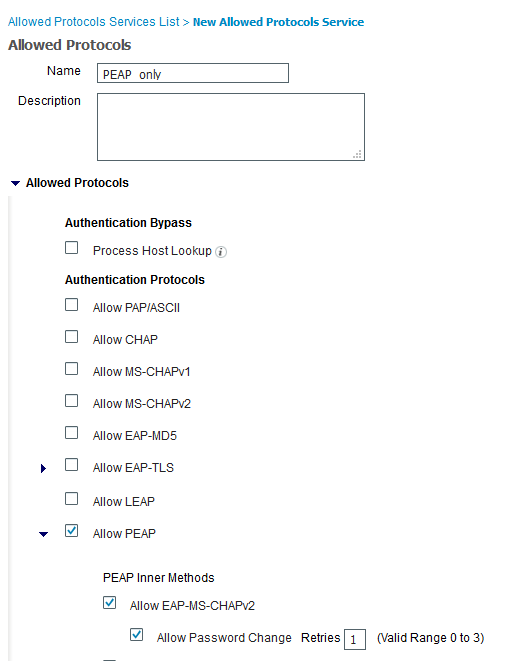
Maybe I missed something, but the way to prevent any Supplicant from succeeding in trying the EAP-TLS is method, is for ISE not to offer it in the TLS negotiation.
If a supplicant requests EAP-TLS and ISE isn't able to offer it, then the conversation ends there.
This is done via the Allowed Protocols section in Authentication. Create a new Allowed Protocols profile and then only allow EAP-PEAP.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide