- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISW CWA & PROFILING
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2021 05:01 AM
Hi Guys,
Just reading about ISE profiling I got a little bit confused , I can imagine a case where CWA is configured on ISE along with Profiling (whatever probes enabled).
I know that CWA consist of two phases and phase 1 main goal is to redirect the user to the CWA portal but phase 1 is done using MAB that is the MAB transaction should fail to continue to Authorization and Issue the redirect.
My question is what if the Guest Mobile device or laptop got profiled? it would be presented in the endpoint database and MAB should not fails then how would this work?
Thanks
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 04:14 PM
It all depends on your
1) Authorization Rules
2) Endpoint Profile configurations
Typically you have Policy Authorization Rules that match on endpoint profiles:
If there is a match, ISE will assign the Authorization Result and not continue to through the policy where it would eventually match on your CWA rule very near the bottom if not the final Default.
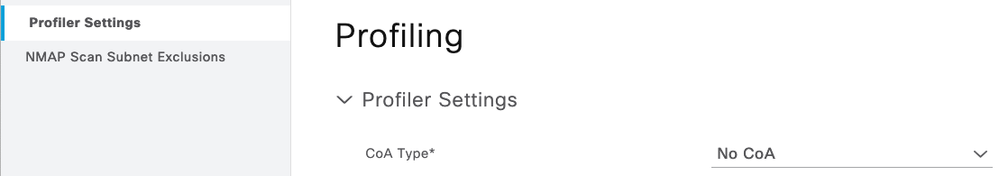
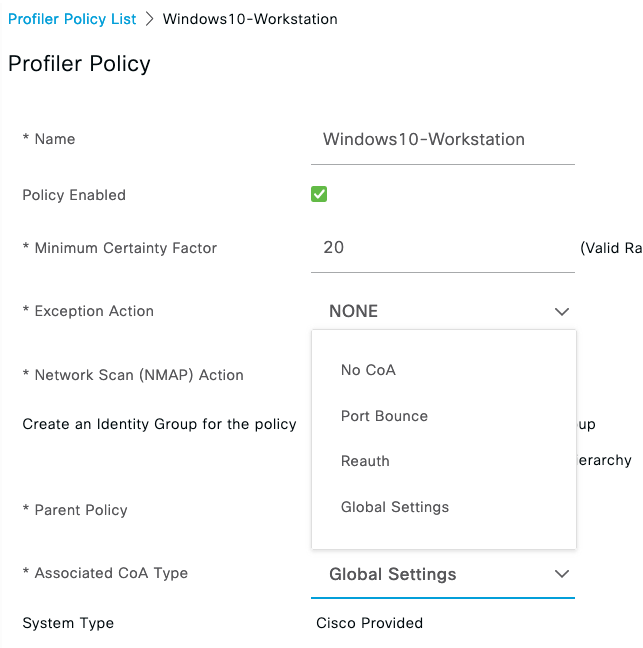
The endpoint profile may change based on new information after the initial assignment from HTTP, NMAP, etc. When this happens, you may perform a RADIUS Change of Authorization (COA). The default Global setting is to do nothing.
You have the ability to control and override this behavior per endpoint profile:
You probably do not care about some random guest using Windows 10 Workstation... so don't change it.
But if it is profiled as a printer or other specialized IOT device, you may want to dynamically perform a COA and re-authorize it properly.
Which COA you choose to perform would also depend on the endpoint type and how you have your access VLANs configured and what your network device is capable of supporting.
It is typically a bad idea to change the VLAN of non-workstations because they will not know to re-DHCP. For this reason if you do a COA you may want to do a COA with Port Bounce. It can be very endpoint-specific.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2021 04:14 PM
It all depends on your
1) Authorization Rules
2) Endpoint Profile configurations
Typically you have Policy Authorization Rules that match on endpoint profiles:
If there is a match, ISE will assign the Authorization Result and not continue to through the policy where it would eventually match on your CWA rule very near the bottom if not the final Default.
The endpoint profile may change based on new information after the initial assignment from HTTP, NMAP, etc. When this happens, you may perform a RADIUS Change of Authorization (COA). The default Global setting is to do nothing.
You have the ability to control and override this behavior per endpoint profile:
You probably do not care about some random guest using Windows 10 Workstation... so don't change it.
But if it is profiled as a printer or other specialized IOT device, you may want to dynamically perform a COA and re-authorize it properly.
Which COA you choose to perform would also depend on the endpoint type and how you have your access VLANs configured and what your network device is capable of supporting.
It is typically a bad idea to change the VLAN of non-workstations because they will not know to re-DHCP. For this reason if you do a COA you may want to do a COA with Port Bounce. It can be very endpoint-specific.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2021 02:24 AM
Hi thomas,
I really appreciate this useful explanation, very clear.
Thank you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide