- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Juniper EX Network Device Profile with CoA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2020 09:30 PM - edited 08-04-2020 10:02 PM
I recently worked with a customer that is deploying Juniper EX switches with their existing ISE 2.6 cluster for NAC. We found that the currently available Network Device Profile for Juniper EX switches did not provide the ability to perform CoA actions against an active session.
After working with the customer and their Juniper resources, we confirmed that the Juniper switches being deployed do support the Cisco AV-Pair for 'subscriber:command=reauthenticate' to provide for basic CoA Reauth. Based on the customer testing, I have updated the XML file and attached it here for others to use. Please note that the Juniper switches do not support the additional Cisco AVP attributes for 'rerun' and 'last' so all three Re-authenticate attributes (Base, Rerun, Last) use only the single AV-Pair. As such, all three CoA actions have the same result.
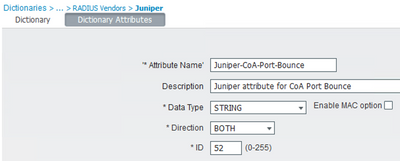
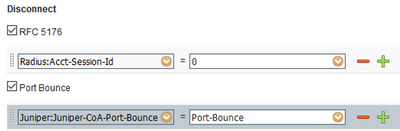
The Juniper resource also confirmed that the Juniper switches being deployed support CoA Port-Bounce based on this document. ISE does not have a default Dictionary for this AVP, so it requires manually adding the attribute and updating the Network Device Profile to use it (I could not include this in the attached XML as the import fails with a 'validation error' without the Dictionary being added first).
Add the Dictionary:
Update the Juniper Network Device Profile:
This was validated by the customer using the following components:
ISE 2.6 patch 6
Hardware EX4300-48P
Junos:18.4R2-S2
The NAC-related configuration provided by the Juniper resources was:
set access radius-server <ip> dynamic-request-port 3799 set access radius-server <ip> secret <secret> set access profile 8021x-auth accounting-order radius set access profile 8021x-auth authentication-order radius set access profile 8021x-auth radius authentication-server <ip> set access profile 8021x-auth radius accounting-server <ip> set access profile 8021x-auth radius options nas-port-type ethernet ethernet set access profile 8021x-auth radius-server <ip> port 1812 set access profile 8021x-auth radius-server <ip> dynamic-request-port 3799 set access profile 8021x-auth radius-server <ip> secret <secret> set access profile 8021x-auth radius-server <ip> source-address <src-ip> set access profile 8021x-auth accounting order radius set access profile 8021x-auth accounting accounting-stop-on-failure set access profile 8021x-auth accounting accounting-stop-on-access-deny set access profile 8021x-auth accounting coa-immediate-update set access profile 8021x-auth accounting update-interval 30 ! set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA from source-prefix-list MGMT_PREFIX set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA from source-prefix-list NSM_PREFIX set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA from protocol udp set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA from destination-port 3799 set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA then policer radius-policer set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA then count radius_coa set firewall family inet filter v4_PROTECT_RE_FILTER term PERMIT_RADIUS_CoA then accept
I hope this helps others looking at a similar deployment.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 10:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 10:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2022 02:27 AM
Thank you Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2023 03:46 PM
Using Cisco AAA (Cisco prime Access registrar 9.2) and Juniper BNG, PoD is working find. With CoA 99% of times getting the error code 503: Session context not found. I have similar NAC configurations as yours. What could be wrong? Appreciate your response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2023 01:49 AM
Hi,
I believe, that attribute name of item 52 is "Juniper-AV-Pair". Value Port-Bounce seems to be OK.
Jozef
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide