- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Live Logs for TrustSec?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 08:02 AM
Is there a feature like RADIUS Live Logs for TrustSec?
I want to be able to see if someone is hitting a SGACL rule for troubleshooting and auditing.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 08:21 AM - edited 05-29-2019 09:25 AM
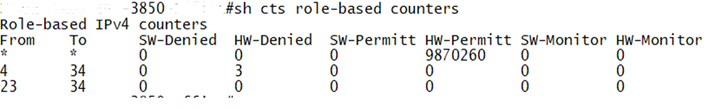
These statistics are not reported to ISE. You are only able to view hits on the SGACL where the enforcement takes place. On a 3850 for example, you can run show cisco trustSec role-based counters ipv4 to see hits incrementing, but it is not split by IP, just SGT to SGT.
You can export deny and drop events via netflow to something like stealthwatch. I have not done this before, so i'm not certain what the reporting looks like on the collector.
This is one area that I think is a challenge with TrustSec, you decentralize your enforcement away from firewalls that log in great detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2019 02:06 AM
Yes, there is/was a report in ISE reporting on SGACL drops but the ONLY platform that exported drop information is/was the Cat6500. This is not something that has been expanded to other platforms and has not been maintained; that feature is not of use to you as it stands.
Your friend here is the 'log' keyword at the end of the SGACE's, for example, 'deny ip log'. This will generate syslog messages for hits which can be reported on via the likes of SIEM tools like Splunk for example.
And as was stated, Stealthwatch can receive Netflow records with SGT/DGT information and can report on flows in the network and hence, enforcement operation deduced.
There are programs in place to provide further tools for enhancing visibility, stay tuned...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 08:21 AM - edited 05-29-2019 09:25 AM
These statistics are not reported to ISE. You are only able to view hits on the SGACL where the enforcement takes place. On a 3850 for example, you can run show cisco trustSec role-based counters ipv4 to see hits incrementing, but it is not split by IP, just SGT to SGT.
You can export deny and drop events via netflow to something like stealthwatch. I have not done this before, so i'm not certain what the reporting looks like on the collector.
This is one area that I think is a challenge with TrustSec, you decentralize your enforcement away from firewalls that log in great detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 11:32 AM
Thanks,
I did see a report in ISE that was for SGACL Drops and it reinforced what you said that netflow would have to be enabled on the switch to report these events to ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2019 02:06 AM
Yes, there is/was a report in ISE reporting on SGACL drops but the ONLY platform that exported drop information is/was the Cat6500. This is not something that has been expanded to other platforms and has not been maintained; that feature is not of use to you as it stands.
Your friend here is the 'log' keyword at the end of the SGACE's, for example, 'deny ip log'. This will generate syslog messages for hits which can be reported on via the likes of SIEM tools like Splunk for example.
And as was stated, Stealthwatch can receive Netflow records with SGT/DGT information and can report on flows in the network and hence, enforcement operation deduced.
There are programs in place to provide further tools for enhancing visibility, stay tuned...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2020 02:38 AM
@Damien Miller wrote:These statistics are not reported to ISE. You are only able to view hits on the SGACL where the enforcement takes place. On a 3850 for example, you can run show cisco trustSec role-based counters ipv4 to see hits incrementing, but it is not split by IP, just SGT to SGT.
Hello @Damien Miller if not too busy, can you please confirm if you have seen this working on 3850. There is contradicting information from Cisco
TrustSec 3850 Specific Troubleshooting Information > Counters on the 3850 and 3650
The role-based counters command is broken on the 3850 and 3650, no data is ever displayed. This is fixed in release 16.6.1.
This is logged as DDTS CSCuu32958 (3850 "show cts role-based counters" not implemented platform limitation).
3850 "show cts role-based counters" not implemented platform limitation CSCuu32958
3850 does not display any trustsec counters for dataplane.
When executing:
"show cts role-based counters"
We see no counters (while having multiple policies displayed by "sh cts role-based permissons").
That command is necessary for troubleshooting.
That is a platform limitation for both 3650 and 3850. Feature will not be implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2020 08:59 AM
I have confirmed that "show cts role-based counters" works as expected on a 3850 running both 16.6.7 and 16.9.5.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide