- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Match EAP-TLS as Authentication Condition
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2018 09:32 AM
Hello,
I am trying to create an authentication rule to match EAP-TLS authentication requests but the system (ISE 2.2 Patch 7) doesn't allow me. As you can see on the attached screenshots, I receive a warning when I create the Authentication Compound Condition and I am not able to use it in the Authentication policy.
If I add the condition manually (Add/Attribute Value) on the authentication rule, I don't receive any warning (also screenshot attached).
I would like to know:
- Why I cannot use a Library Compound Condition but I can add the condition using Add/Attribute Value in the authentication rule?
- If I do it using Add/Attribute Value in the authentication rule, will this configuration work?
Thanks and regards,
Víctor.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 07:08 AM
Victor, looks to be ISE UI bug. If you can use it as manually (Or AKA 'in-line') condition within the authentication rule then it is certainly supported.
By the way, if it is just one condition, you could try it with simple condition instead of compound condition if you still want to use library instead of in-line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2018 11:15 AM
Why do you want to call out EAP-TLS specifically in the authentication phase? Just build an Identity Source Sequence that encompasses both your Active Directory domain and your Certificate Authentication Profile (CAP) and you can cover both PEAP and EAP-TLS use cases in your authentication phase. Use the default authentication rule and assign the ISS. The only reason to call out specifics in the authentication phase is if you have different CAPs. With modern certs using SAN fields for almost everything you rarely if ever need a CAP other than pointing at the SAN field for identity information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 12:24 AM
Hi Paul,
Many thanks for your answer. Using an ISS was also my first approach but it is a requirement of the project to split each authentication protocol in an authentication rule.
As per ISE configuration we should be able to do it as it is allowed to use these attributes as condition in a authentication rule. However, it is quite strange that if we create a Compound Condition with the same condition, it cannot be used in the authentication rule (I know it can be used in a sub-rule but it doesn't fit the case I want to cover). That's why I am wondering if it is a supported configuration that will actually work or it shouldn't be allowed by ISE interface to use EAPAuthentication or EAPTunnel attributes in the first condition of an authentication rule.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 06:02 AM
I can't remember what condition works in that version of code to split it out at authentication phase. In 2.3+ you can use Network Access:EAP Authentication like you are trying to use.
Honestly, the requirement makes no sense. Part of our job as ISE installers is to educate the customer on how ISE works and steer them to the correct setup. Saying they want to split out EAP-TLS/PEAP in the authentication phase means they don't understand how the ISS works and are making the authentication configuration more complex and less efficient with no security benefit. You will still need to do protocol checks in the authorization phase if you are going to allow more than EAP-TLS.
The basic fundamental of ISE that I emphasis with all my customers is the authentication phase only job is to answer the question "Are the credentials provided correct?". Any AD account (and local accounts of if you allow them) and any valid certificate from CAs you trust for client authentication should pass the authentication phase. All the magic of ISE happens in the authorization phase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 07:08 AM
Victor, looks to be ISE UI bug. If you can use it as manually (Or AKA 'in-line') condition within the authentication rule then it is certainly supported.
By the way, if it is just one condition, you could try it with simple condition instead of compound condition if you still want to use library instead of in-line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 08:35 AM
Many thanks howon!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2018 05:28 AM
Hello Hosuk,
This authentication rule has been configured but it never get matched - even when it should.
Once again please – is this really supposed to work? Is this supported by design?
Many Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2018 12:10 PM - edited 09-20-2018 12:14 PM
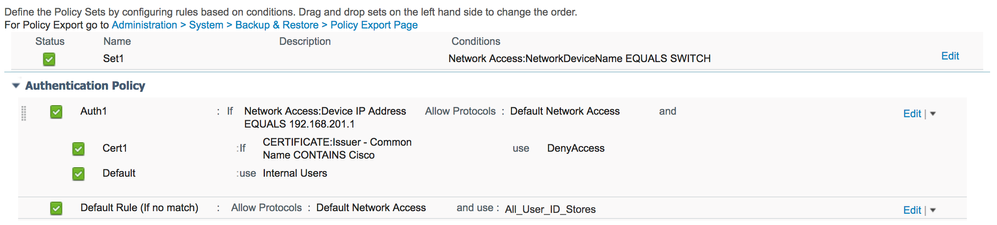
I have validated the following setup works with both 2.4p3 and 2.2p10. The setup is a bit convoluted with 2.2 since you have to make a rule with dummy condition that will be true all the time (called ‘Auth1’ in my example below).
ISE 2.4p3:
ISE 2.2p10:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 05:29 AM
Hi,
I am trying to build a policy that can differnciate between EAP-TLS and PEAP as we migrate from one to another. I am trying to achieve this by configuring and authentication policy that matches based on the same configuration as victguti has in his second image. ( if NetworkAccess>EapAuthentication>Equals>EAP-TLS). However, under network access, EAPAuthentication does not appear as an option and if I create a condition manually to match it, it appears in the list but is greyed out and cant be selected. Any Ideas at all?
Many Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 05:41 AM
1) Create a certificate authentication profile (CAP) to specify where in the certificate you want ISE to collect the identity from, usually the SAN field.
2) Create an identity source sequence, we usually call it Cert_Active_Directory, that ties together the CAP and your AD source.
3) Apply the identity source sequence to the default authentication rule in your policy set.
Then all your work happens in the authorization phase. You specify PEAP or EAP-TLS in your authorization rules to match the different conditions you want to allow.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide