- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Migration from ACS 5.8.1 to ISE 2.3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 04:37 AM
Hi,
I am trying to do migration from ACS 5.8.1 to ISE 2.3. It is giving an error while trying to establish a connection to ACS while exporting. Attached error message for reference. I have uploaded the self signed certs in the migration tool for ACS and ISE and have also added the hostname in the DNS. The only issue I see here is the hostname mismatch in DN of the cert and the ACS hostname.
Cert name (DN) - MUMBRCIPAAA002--reset ( I had to run the reset-managemen-tinterface-certificate command in ACS cli as the GUI stopped responding when I created a new self signed certificate)
Hostname of ACS - MUMBRCIPAAA002
If my understanding is correct and hostname is an issue, then will changing the ACS hostname from command line disrupt the ACS service?
Also, I am currently doing the migration in ISE standalone mode and once the migration is complete, I will change the ISE node to Primary PAN and then add other nodes. (1 node in PAN secondary, 3 PSN's and 2 MnT (primary and secondary).
Will it affect the migrated config?
Need inputs/Suggestions to resolve this.
Regards
Rajesh
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 10:58 AM
Enabling Trusted Certificates in the Migration Tool says,
In Cisco Secure ACS, ensure that the server certificate is in the System Administration > Configuration > Local Server Certificates > Local Certificates page. The Common Name (CN attribute in the Subject field) or DNS Name (in the Subject Alternative Name field) in the certificate is used in the ACS5 Credentials dialog box to establish the connection and export data from Cisco Secure ACS.
Yes, I expect it to restart ACS services after changing the hostname.
You may change ISE from standalone to distributed with multiple ISE nodes after migration is done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 10:58 AM
Enabling Trusted Certificates in the Migration Tool says,
In Cisco Secure ACS, ensure that the server certificate is in the System Administration > Configuration > Local Server Certificates > Local Certificates page. The Common Name (CN attribute in the Subject field) or DNS Name (in the Subject Alternative Name field) in the certificate is used in the ACS5 Credentials dialog box to establish the connection and export data from Cisco Secure ACS.
Yes, I expect it to restart ACS services after changing the hostname.
You may change ISE from standalone to distributed with multiple ISE nodes after migration is done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 11:40 PM
Hello,
Many thanks for your response.
Will changing the ACS hostname affect the current profiles, groups and configuration of ACS?
Regards
Rajesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2017 09:03 AM
If possible, it's best to take a backup, restore it to an ACS running in your lab, and use that as the source instead of your production ACS.
It seems to me that it would be easier to create another self-signed certificate to match the hostname instead of renaming the hostname.
Since ACS may run in a cluster, the profiles, groups, and policy configurations are not depending on the hostname. However, if this ACS is joined to a Microsoft Active Directory domain, then it can lose the membership and require re-join after hostname update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2017 09:07 AM
The profiles and groups do not change when you change ACS hostname.
From ACS, if you export the local certificate to a windows box it will export as *.cer file and when you open that and go to details tab you will see the CN.
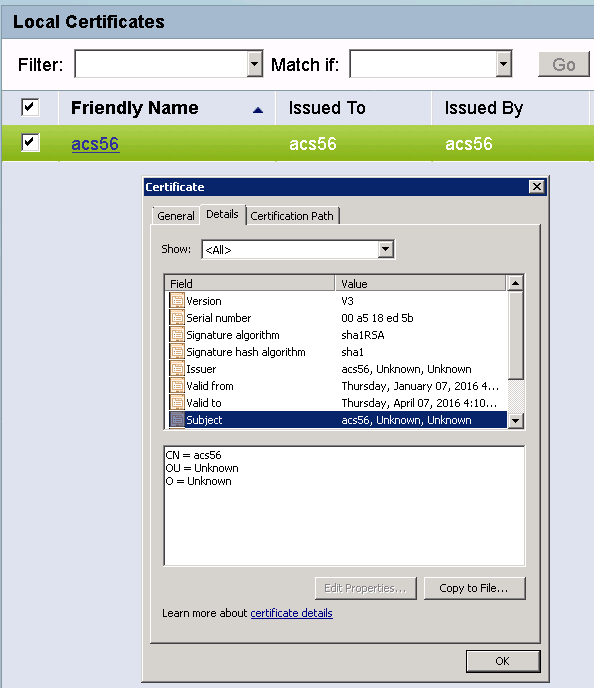
Also make sure the DNS entry of the hostname points to the right IP address. If you do not have DNS you can use /etc/hosts file for this.
-Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 08:19 AM
Hi Krishnan,
Thanks for the input. Migration is completed successfully. However while testing it, IPv4 devices - users are getting authenticated successfully but for IPv6 devices - it shows failed. I checked the logs and it shows authentication passed but fails to match any authorization policy and it goes the last policy with "deny all" shell profile. This was again verified by the hits received on the last policy. I have checked the user, usergroup, profiles, polices - all have been migrated properly. I am not sure where am I going wrong.
P.S - I gave static Ipv6 address to all the nodes after the nodes were put in distributed mode. I disabled the IPv6 dhcp server and autoconfig. Also the migration from ACS 5.8 to ISE 2.3 was done in standalaone mode and then the nodes were put in distributed mode.
Please share your inputs.
Regards
Rajesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 10:09 AM
Hi Rajesh,
Please look at the document on TACACS+ Ipv6 document that describes certain caveats(For eg: use global ipv6 and not link local on the network device) and the flow.
https://communities.cisco.com/docs/DOC-75571
Make sure you see the ipv6 address in the live logs and the authentication succeeds. Take a look at the doc above and follow through the instructions provided.
Let us know if you have an issue. You can also open up a TAC case with help from Cisco Sales.
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2017 09:14 AM
Hi Krishnan,
Many thanks for your response. I already had this document and had verified it. I did check the logs and it captures the IPv6 address and also the Authentication showed as passed, so I figured out it was failing at the authorization policy. While checking the authorization policy, I figured out that the devices were added in the sub group of the parent group and the condition selected in the authorization policy was for the parent group. So I changed that, IPv6 started working fine and I could see hits on the right authorization policy.
Many thanks for your inputs.
Regards
Rajesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2020 01:58 PM
You dont need to change the cert o hostname from device for the migrations, you can configure the file hosts in your PC and add a pointer IP to name ej: 10.10.10.10 MUMBRCIPAAA002--reset or you can change the name in the DNS Server, so your cert to do match with the hostname but your cert should has a valid expiration date, it shouldn´t be expired.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide