- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: No redirect on Wired guest portal, ISE v2.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 11:14 PM
I'm trying to setup a wired guest portal on ISE v2.4 patch 2.
I have managed to configure the portal for wireless with WLC 8.7, works perfect.
But when I do the same for wired I don't get redirected to the login page. I have followed the guides "Deploying Cisco ISE for Guest Networks" on this site.
I can see that the dACL gets applied on the port and I get the right vLAN and the client gets the right IP. I can from the client do dns request against ISE.
As soon as I start the webbrowser I can se it load for a second, almost redirecting me to the loginportal but then tries to loads the default startsite anyway.
If I go to ISE or the switch and pick out the URL-redirect string for my session and copy pasted it in to my browers I get to the loginpage.
But I don't get autoredirected when starting my webbrowser.
Any thougts how to get the client to redirect to the loginpage?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 04:21 AM
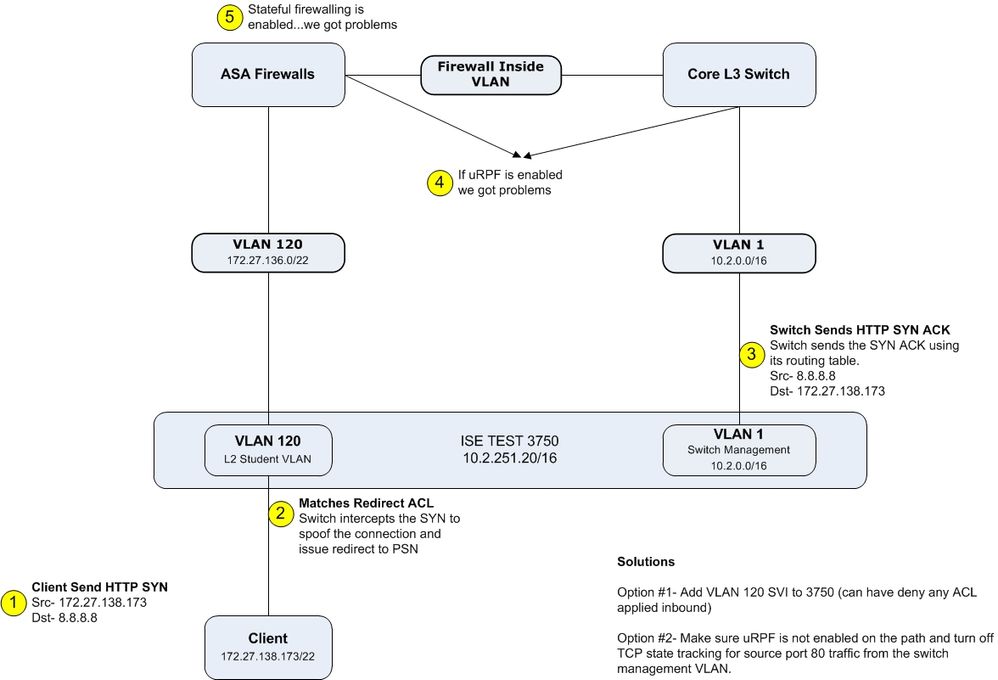
Okay everything looks right so far. Here is the last ditch effort that if true you will say “You have got to be kidding”. Is the management interface of your switch behind a security device or ACL controlled in some fashion or are you doing uRPF checking anywhere?
Here is what you may be running into using a diagram I put together years ago to illustrate the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2018 03:32 AM
So after alot of wireshark and other troubleshooting I've almost pulled all of my hair, now almost bald, I found that there was a ACL that stopped the traffic in one direction. So Paul, I have to give it to you - “You have got to be kidding”.
Since we got 3 diffrent VLAN
1 Switches
2 ISE
3 Clients
The route ACL between the switch and client nets where stopped by an missing ACL-post. Since it is the switch that does the final URL-redirect to the client and not ISE. ISE creates the URL-redrection and the swtich applies it to the client.
Funny fact, this isn'the first time this happens either, this time it only took us 2 weeks to find that the ACL stopped us, eariler it was alot longer time...
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 07:06 AM
Do you have the HTTP/HTTPS enabled on the switch? If you do a show auth session or show access-session details on the port you said you see the redirect applied. What does your redirect ACL on the switch look like?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 07:15 AM
The redirect and HTTP/HTTPS should look something like this:
ip access-list extended PORTAL-REDIRECT
deny udp any any eq domain
deny ip any <ISE PSNs>
permit ip any any
!
ip http server
ip http secure-server
!
ip http secure-active-session-modules none
ip http active-session-modules none
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 11:41 PM - edited 09-04-2018 11:58 PM
Hi Paul
First of all thanks for taking your time to look at my problem.
My access list looks like this.
And from what I have learned this access list determines what traffic will be redirected to the URL
ip access-list extended ACL_WEBAUTH_REDIRECT
deny udp any eq bootpc any eq bootps
deny udp any any eq domain
deny ip any <ISE PSNs>
permit tcp any any eq www
permit tcp any any eq 443
permit tcp any any eq 8443
!
It is the same result if I add permit ip any any at the end of the accesslist.
*****************************************
The HTTP/HTTPS server is configed.
ip http server
ip http secure-server
!
ip http secure-active-session-modules none
ip http active-session-modules none
*****************************************
switch#sh authentication sessions int g1/0/13 details
Interface: GigabitEthernet1/0/13
IIF-ID: 0x154C9113
MAC Address: <Client-MAC-address>
IPv6 Address: Unknown
IPv4 Address: Unknown
User-Name: <Client-MAC-address>
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Common Session ID: AC16DA2F0000009FA8549BC3
Acct Session ID: 0x00000042
Handle: 0x72000048
Current Policy: POLICY_Gi1/0/13
Local Policies:
Idle timeout: 65536 sec
Server Policies:
Vlan Group: Vlan: 2
SGT Value: 6
URL Redirect ACL: ACL_WEBAUTH_REDIRECT
URL Redirect: https:// <ISE-server> :8443/portal/gateway?sessionId=AC16DA2F0000009FA8549BC3&portal=1309b100-a773-11e8-9246-76e9b347a8be&action=cwa&token=d68591e196a0a163ce7da1cf7aa85812
ACS ACL: xACSACLx-IP-HG-ISE-ONLY-5b894617
Method status list:
Method State
mab Authc Success
*****************************************
Regardless of what webbrowser I use the result is the same. The Webbrowsers only tries to show the default startsite, and fails. Same results on both Windows and Linux clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 04:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 11:25 PM
Yes, the dACL I apply is the "HG-ISE-ONLY" you see in my latest post. The dACL looks like this:
permit udp any eq bootpc any eq bootps
permit udp any any eq domain
permit tcp any host <ISE> eq 80
permit tcp any host <ISE> eq 443
permit tcp any host <ISE> eq 8443
permit tcp any host <ISE> eq 8905
even tried adding the following
permit ip any host <ISE>
permit ip any any
Same results.
As I said in earlier post, I can do a DNS-dig-request from the client and I get answer from our DNS-server wher i get pointed to ISE. I get the right VLAN and IP-address. And if I take out the redirect-URL from ISE or the switch and copy paste it in to the browser I get to the portalpage, but I never get redirected to the portal. Same thing with every client we have tried with, Windows/Linux, no redirect.
When I set it up I followed this guide, and I followed Ciscos advice and did a seprate dACL for everything else
Deploying ISE for Wired Network Access
URL Redirection ACL
This ACL defines which traffic is redirected to ISE during CWA, BYOD, and Posture scenarios. Any traffic that is permitted per ACL is redirected (192.168.1.10 in the example below). Implicit deny prevents other traffic types from being redirected. We recommended that you specify only HTTP (and HTTPS) here to be permitted since this traffic gets pushed to the switch CPU. If additional access control is needed in conjunction with the redirect ACL, then werecommend using dACLs along with the redirect ACL.
To rule out the switch, we tried it on diffrent switches as well, 3560v2 and 3650.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 04:21 AM
Okay everything looks right so far. Here is the last ditch effort that if true you will say “You have got to be kidding”. Is the management interface of your switch behind a security device or ACL controlled in some fashion or are you doing uRPF checking anywhere?
Here is what you may be running into using a diagram I put together years ago to illustrate the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2018 03:32 AM
So after alot of wireshark and other troubleshooting I've almost pulled all of my hair, now almost bald, I found that there was a ACL that stopped the traffic in one direction. So Paul, I have to give it to you - “You have got to be kidding”.
Since we got 3 diffrent VLAN
1 Switches
2 ISE
3 Clients
The route ACL between the switch and client nets where stopped by an missing ACL-post. Since it is the switch that does the final URL-redirect to the client and not ISE. ISE creates the URL-redrection and the swtich applies it to the client.
Funny fact, this isn'the first time this happens either, this time it only took us 2 weeks to find that the ACL stopped us, eariler it was alot longer time...
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2018 06:29 AM
Yeah, you would think the switch could just do a MAC address flip and send the data back out the port instead of actually routing it through the network back to the client. When I first saw this years ago I couldn't believe that was how the process was implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2019 12:01 PM
Hi Paul,
Wondering if (1) this the ONLY solution and (2) if it's still applicable on the below scenario:
2960x Switch with only Management VLAN IP and no other SVI --> Trunk port to Cisco Router (which has the VLAN / Routed interfaces)
As a test, I created a VLAN SVI on the 2960x switch and noticed the redirect immediately started during start-up but, i can no longer sign-in to the workstation with other AD user accounts - Error "Domain isn't available" as per enclosed screenshot.
Is there any other ways to deploy the "Posture Module Install" ? GPO or using PDQ deploy (https://www.pdq.com/pdq-deploy/)
Thanks,
Rao
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide