- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Not only portal cert but also admin cert are used during native supplicant provisioning process
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Not only portal cert but also admin cert are used during native supplicant provisioning process
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2018 09:01 AM
Hi Team,
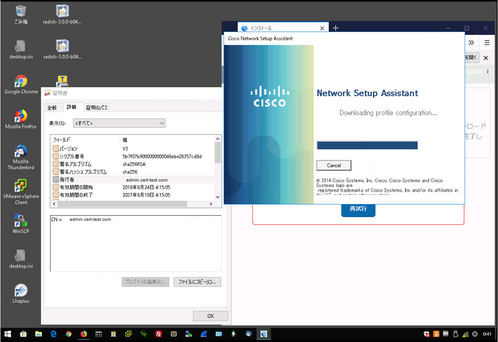
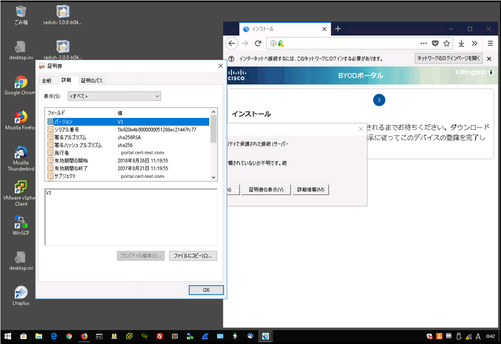
I tested simple windows NSP process, and found the portal uses admin cert first then use portal cert like that.
1) The portal page shows admin cert first. (self-signed admin cert "admin.cert-test.com" is provided)
2) Then the portal page shows portal cert. (self-signed portal cert "portal.cert-test.com" is provided.)
However, now the customer doesn't want to expose the content of admin cert to employees.
Is it expected behavior? And Is there a way to configure ISE certificates so that only portal certificate is used during NSP process?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 06:52 AM
What you described is the same issue as your other post -- Group tag doesn't work for portal FQDN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2018 05:52 PM
The issue of Group tag doesn't work for portal FQDN is triggered by accessing FQDN shortcut like https://mydevices01.cert-test.com from web browsers. Now I understand it's expected behavior.
But for the BYOD provisioning, similar shortcut FQDN cannot be definied because the URL is dynamically generated for each client session. And the admin certificate access is not from web browsers but from network setup application.
Now you say it's same issue as mydevices portal. But why does the application requires "<ise_fqdn>:443"? I guess It can simply access "<ise_fqdn>:8443" directly...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide