- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Problems with MAB and dynamic VLANs when changing from 3750 to 3850
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2020 12:04 PM
Hello everyone,
I have an urgent problem with the change of a network devices and kindly ask for support. We have many access stacks (WS-3750-24TS - firmware 12.2 (55) SE), these have been running unchanged since 2011 and are currently to be exchanged for WS-C3850-24T firmware 16.6.7. 802.1X (PEAP, TLS, etc) authentication is not used in the network, ONLY MAB! The clients are dynamically assigned to VLANs using Mac Authentication Bypass. The Radius server is a Microsoft NPS still on Windows 2008 server. Today we brought a 3850 into the running network and tested the authentication whole day without success. The configuration should simply be taken over from the old switches 1:1 (except commands with changed syntax). There appears to be a problem with the communication between the switch and the NPS so that MAB does not appear to be taking place properly and the VLAN is not dynamically assigned.
Here is the old AAA / RADIUS / Port Config of a 3750:
aaa new-model ! aaa authentication login default enable aaa authentication dot1x default group radius aaa authorization network default group radius ! aaa session-id common ! dot1x system-auth-control dot1x guest-vlan supplicant ! interface FastEthernetx/x/x switchport access vlan 100 switchport mode access authentication control-direction in authentication event no-response action authorize vlan 100 authentication port-control auto authentication periodic mab dot1x pae authenticator dot1x timeout quiet-period 5 dot1x timeout tx-period 5 spanning-tree portfast ! radius-server host x.x.x.1 auth-port 1812 acct-port 1813 key 1234 radius-server host x.x.x.2 auth-port 1812 acct-port 1813 key 1234
Here is the AAA / RADIUS / Port Config of a new 3850:
aaa new-model ! ! aaa authentication login default local aaa authentication dot1x default group radius aaa authorization exec default local aaa authorization network default group radius ! aaa session-id common ! dot1x system-auth-control dot1x guest-vlan supplicant ! interface GigabitEthernetx/x/x switchport access vlan 100 switchport mode access authentication control-direction in authentication event no-response action authorize vlan 100 authentication port-control auto authentication periodic mab dot1x pae authenticator dot1x timeout quiet-period 5 dot1x timeout tx-period 5 spanning-tree portfast ! radius server radius1 address ipv4 x.x.x.1 auth-port 1812 acct-port 1813 key 1234 ! radius server radius2 address ipv4 x.x.x.2 auth-port 1812 acct-port 1813 key 1234
*** Different variants of the RADIUS server configuration were tested ... aaa group etc. ***
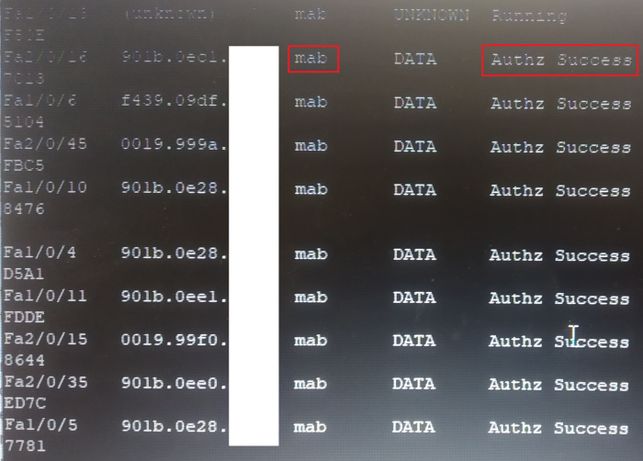
Authentication works wonderfully with the old 3750 switches, Authz Success and is also recognized as MAB:
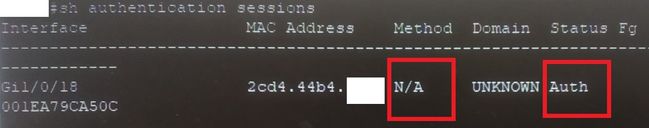
This does not work with the new 3850 switches! Method stands for N / A and status stands for "Auth".
The actual result of the authentication is that the PC comes into the VLAN 100 (authentication event no-response action authorize vlan 100) and receives an IP address there, i.e. it is not in its actually assigned VLAN. However, according to the NPS Log, the MAC address stored in the AD is assigned in the correct network policy and thus in the correct VLAN.
The NPS server shows both authentications as completely identical, except that of course the switch name and the switch IP are different!
I would be very happy to receive support because I don't know what to do next. What has changed about the new 3850 that authentication no longer works?
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 11:56 PM
Hi,
we analyzed the packages with Wireshark. When authenticating with the new and the old switch, the NPS returns the same accept packet. However, the new switch cannot evaluate the package. So we tested various settings on the Radius server and it works after several hours of testing with the following combination. IBNS 2.0 on the switch and a special setting for the RADIUS attributes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2020 07:27 AM
Do you have the VLAN's configured on the 3850 that the NPS server is trying to assign? Are you assigning via VLAN number or name? If the switch does not have the VLAN configured or if the name doesn't match what is sent from the Radius server, then the switch will fail the attempt since it is unable to apply the policy. That is one thing to check.
Are you seeing the request hit the NPS server from the 3850? And is it successful?
You could also try to turn on debugs on the 3850 to see what is actually happening. Debug radius to see if the requests are going out and if the responses are coming back. Verify that the 3850 is receiving an access-accept with the correct A/V pairs. If you see the access-accept and the A/V pairs are correct, then you can debug epm to see why the switch is unable to apply the policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 11:56 PM
Hi,
we analyzed the packages with Wireshark. When authenticating with the new and the old switch, the NPS returns the same accept packet. However, the new switch cannot evaluate the package. So we tested various settings on the Radius server and it works after several hours of testing with the following combination. IBNS 2.0 on the switch and a special setting for the RADIUS attributes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 09:50 AM
What was the command you used to make it authenticate with NPS. We are also trying to deploy switches with IBNS 2.0 with NPS and are struggling making process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2020 03:45 AM
Hi, there was no special command that made it running. You can only test with the attributes on the NPS site to find a solution. Which server version are you running?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 09:36 AM
Using Server 2019
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2020 11:34 PM
Hello jon101,
we have now replaced the server 2008 with a 2019. Suddenly, authentication no longer works with the 3850 switches. Summarized:
3750 + 2008 = ok
3850 + 2008 = ok
3750 + 2019 = ok
3850 + 2019 = not ok
Did you get this to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2020 08:33 AM
Here is the c9300 config TAC and I got working. We didn't use MAB. I did have to play around with the Windows 10 NIC configuration. The standard stuff in NPS was correct. Let me know if you have questions and I'll do my best to help.
aaa new-model
!
!
aaa group server radius NPS_SERVERS
server name DC1
server name DC2
!
aaa authentication login default group NPS_SERVERS local
aaa authentication enable default none
aaa authentication dot1x default group NPS_SERVERS
aaa authorization network default group NPS_SERVERS
aaa accounting update newinfo periodic 2880
aaa accounting identity default start-stop group NPS_SERVERS
!
!
!
aaa server radius dynamic-author
client 10.0.5.105 server-key 7 xxxx
client 10.0.5.110 server-key 7 xxxx
!
aaa session-id common
!
service-template webauth-global-inactive
inactivity-timer 3600
service-template DEFAULT_LINKSEC_POLICY_MUST_SECURE
linksec policy must-secure
service-template DEFAULT_LINKSEC_POLICY_SHOULD_SECURE
linksec policy should-secure
service-template DEFAULT_CRITICAL_VOICE_TEMPLATE
voice vlan
!
dot1x system-auth-control
!
class-map type control subscriber match-all DOT1X
match method dot1x
!
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
!
class-map type control subscriber match-all DOT1X_NO_RESP
match method dot1x
match result-type method dot1x agent-not-found
!
!
policy-map system-cpp-policy
!
!
interface GigabitEthernet1/0/5
switchport mode access
device-tracking
access-session host-mode single-host
access-session port-control auto
access-session control-direction both
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
spanning-tree bpduguard enable
service-policy type control subscriber TestAAA1
!
!
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
radius-server dead-criteria time 10 tries 3
radius-server vsa send cisco-nas-port
!
radius server DC1
address ipv4 10.0.5.10 auth-port 1812 acct-port 1813
key 7 xxxx
!
radius server DC2
address ipv4 10.0.5.11 auth-port 1812 acct-port 1813
key 7 xxxx
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2020 11:41 AM
Thank you for the quick help.
What du you mean by "The standard stuff in NPS"? Did you use the "wizard"? Are there configured any attributes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2020 08:50 AM
I used the wizard. To review:
1. Make sure your radius client is setup
2. The wizard should of created the "connection request policy" which the defaults worked for me.
3. For network Policy, the wizard does most everything. To review: Udner Conditions make sure you have your windows group and in that windows group you have a the user account assigned. NAS port type is Ethernet. Then I also use "Client friendly name to specify the Radius client. For example, in my radius clients my client is called Cisco c9300. So my Client friendly name is "Cisco*".
4. Under constants we use EAP(PEAP), which then click edit and make sure MSCHAP is selected along with your certificate. I have a digicert cert, but there are guides for using Windows certificate auth.
5. Framed-Protocol = PPP
Service-Type = Framed
Tunnel-Medium-Type = 802
Tunnel-Pvt-Group-ID = 23 (Or whatever vlan # you want)
Tunnel-Type = Virtual LANs(VLAN)
I do hope this makes sense. Please let me know if you have questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2020 02:31 AM
Hello jon101,
the problem was the firewall setting on the new NPS server. Now it's working. Thank you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide