- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Sponsor Groups using LDAP instead of AD Groups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 11:17 PM
Hello
customer asking whether it's possible to use LDAP as Sponsor Group Member check? We used AD Security Group to begin with, but they asked whether we could use LDAP and reference a completely different AD domain instead.
The LDAP connection would be to an AD domain. The reason they don't want to use AD Join Points is because of the firewall rules that they would have to build is crazy complex apparently. LDAP is simpler. I know ... it's weird.
cheers
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2018 10:25 AM
Also, just to be clear are they putting all their ISE nodes behind firewalls and don't want to AD join them? If they are only doing the guest PSNs then you could still AD join the other PSNs and do traditional AD sponsorship assignments. I do this often in large deployments.
I will stick two dedicated guest VMs out in the DMZ that aren't domain joined to run the guest portal process. The sponsor portal is accessed via the other PSNs that are inside the network and joined to AD. The guest PSNs are still part of the deployment just not joined to AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 11:47 PM
Arne, with your LDAP settings, need to change 'Group Name Attribute' setting to dn instead of cn and re-pull the groups as dn format to make it work. If you look at the memberOf attribute for 'admin-biera' user, the group shows up as dn, so you need to match the format.
In regards to memberOf attribute showing only one value is cosmetic. ISE just returns first value for multi-value attribute such as memberOf for that GUI. But, ISE will pull all memberOf values during runtime.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2018 09:52 AM
Yes, it works the same way as AD integration. Once you establish LDAP with AD on ISE you can pull list of groups you want to use for mapping to sponsor groups.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2018 10:22 AM
Also, just like you can do with AD you can use LDAP attributes to map to sponsor groups if you don't want to use group membership.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 04:38 AM
Are you saying that using LDAP, you can map AD groups, similar to a join-point?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2018 10:25 AM
Also, just to be clear are they putting all their ISE nodes behind firewalls and don't want to AD join them? If they are only doing the guest PSNs then you could still AD join the other PSNs and do traditional AD sponsorship assignments. I do this often in large deployments.
I will stick two dedicated guest VMs out in the DMZ that aren't domain joined to run the guest portal process. The sponsor portal is accessed via the other PSNs that are inside the network and joined to AD. The guest PSNs are still part of the deployment just not joined to AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 04:28 AM
thanks for the positive news.
In this case the customer argued that LDAP is simpler because they don't need all the goodness that AD brings (and all the firewall rules!) - they just need good 'ol fashioned authentication. And I guess that's why it's called Lightweight Directory Access Protocol ;-) - I am starting to think that in most customer deployments an AD Join is like using a jack hammer to drive a little nail into the wall.
I had a quick play in my lab today and it works really well. One little tip for anyone who is a newbie to LDAP and needs some help with things like Subject Search Base and Group Search Base (you can't make this config up if you tried ...) - there is a great tool called AD Explorer from the SysInternals guy - I wanted to plug this app since it made it so much easier to configure LDAP in ISE. I ran the AD Explorer against my Windows Server 2012 R2 and it's super easy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 08:31 PM - edited 09-12-2018 08:37 PM
Hello
An update on this topic. I am using ISE 2.4 patch 3 and Windows 2012 R2 as my LDAP source. I am having trouble getting the LDAP membership mapping working. Authentication seems fine though, because if I combine LDAP auth, with AD Join Point Group checking, then I can login to Portal. But I don't want that. I want LDAP auth, and LDAP Group checking.
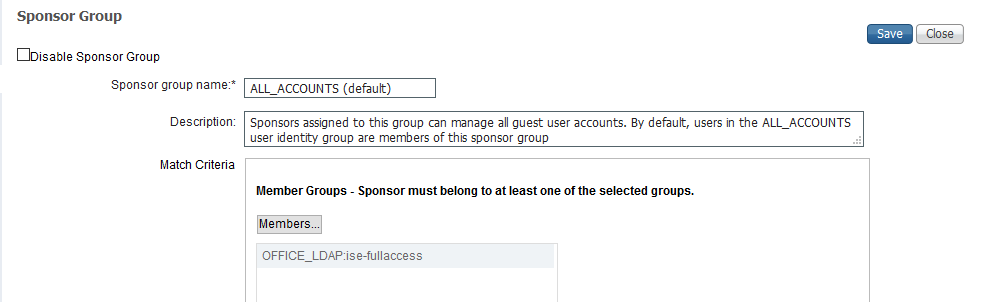
I am unable to validate the group membership using LDAP, despite the fact that I have managed to import the Group I wanted to use, and I also applied it to the Sponsor Group. ISE Failure reason: NO_SPONSOR_GROUP_MEMBERSHIP
What am I doing wrong?
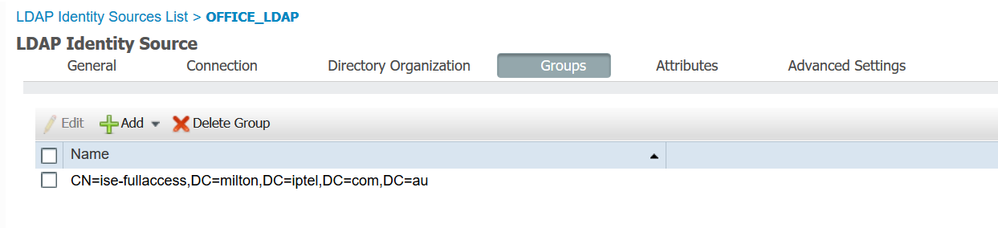
I mapped the LDAP Group to my Sponsor Group.
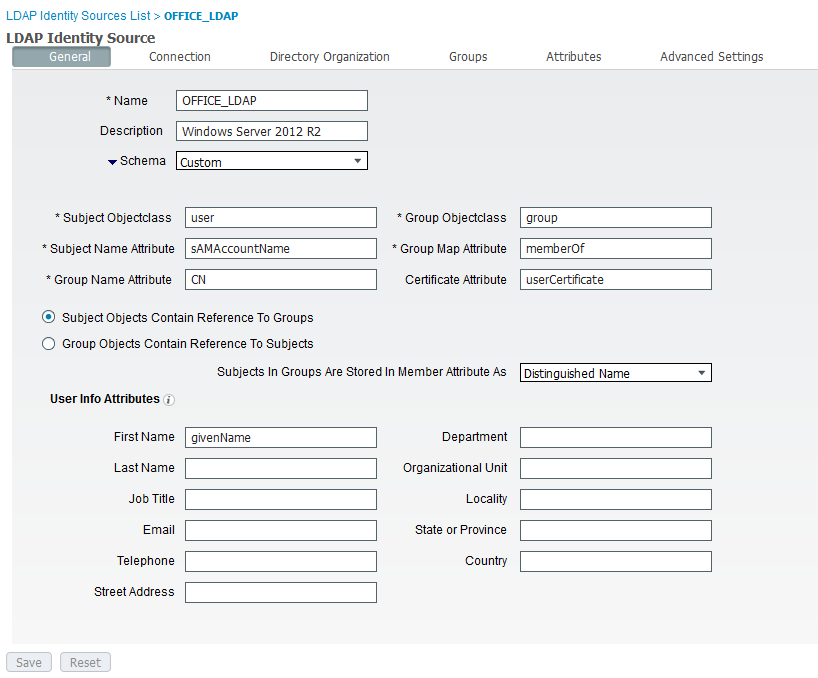
Here is the schema mapping - it's the trickiest part as far as I am concerned - a lot of trial and error to get this woking due to the different names that ISE/Windows/LDAP_Standard use - I hope I got it right
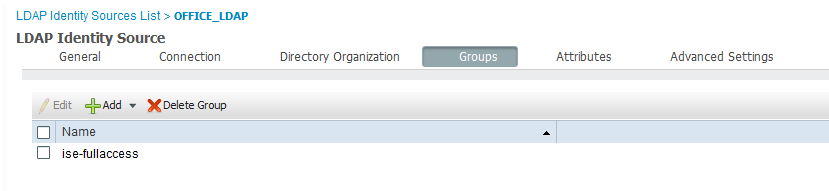
I am able to browse all the AD Groups on the AD Server - I selected the one I am a member of for my test.
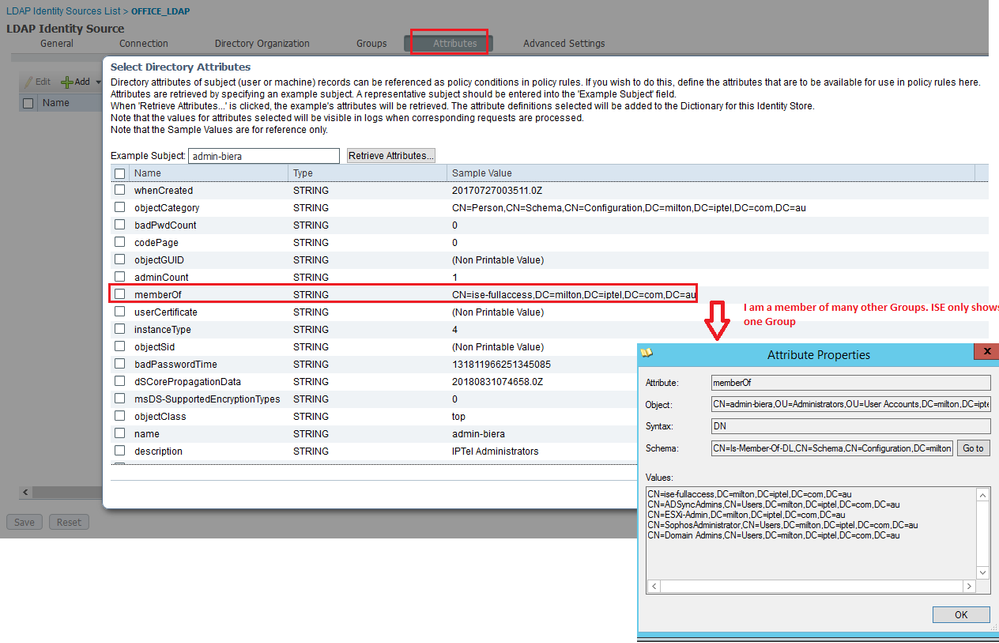
When I search for my username I find it - that tells me that the schema mappings must be correct, or not? But here I already see that ISE says that I am only a member of one Group. Is that cosmetic or a bug?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 11:47 PM
Arne, with your LDAP settings, need to change 'Group Name Attribute' setting to dn instead of cn and re-pull the groups as dn format to make it work. If you look at the memberOf attribute for 'admin-biera' user, the group shows up as dn, so you need to match the format.
In regards to memberOf attribute showing only one value is cosmetic. ISE just returns first value for multi-value attribute such as memberOf for that GUI. But, ISE will pull all memberOf values during runtime.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 04:07 AM
THANK YOU! It works now (in my lab anyway). I had it set this way in my customer and we could not find the group they asked me to locate. So I change it from DN to CN and then the Group appeared. I will check again.
I was able to import the Group in my lab - looks a bit different now, but at least the Sponsor login works :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2018 06:56 AM
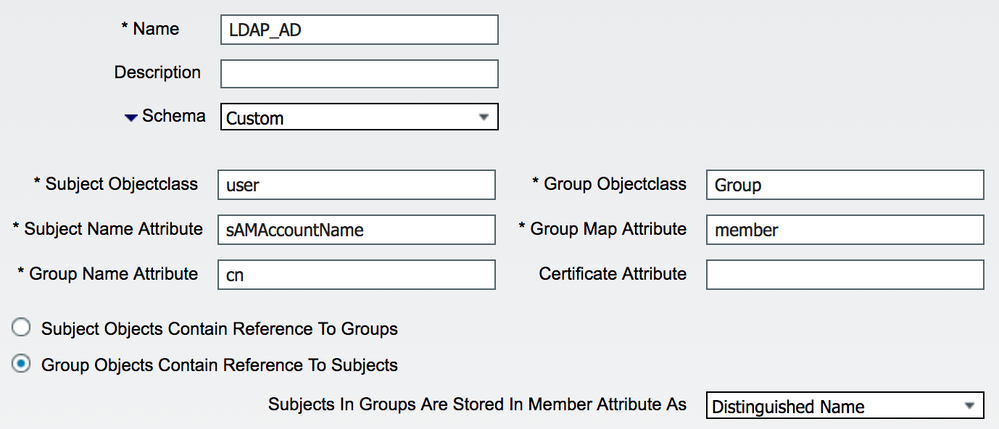
If you want to use cn for the group name, try the settings below instead. AD stores group mappings both ways so referencing users from group should work as well. One caveat with doing LDAP lookup of AD is that ISE will not be able to lookup membership of primary group. For instance, all domain users are part of 'Domain Users' group, but even though you can map 'Domain Users' to sponsor group, ISE will not be able to match using LDAP. This is due to how AD treats primary groups differently and can be avoided by using other groups or native AD integration.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide