- Cisco Community
- Technology and Support
- Security
- Network Access Control
- TACACS Proxy with Service-Argument Attribute not working Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
TACACS Proxy with Service-Argument Attribute not working Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 05:45 AM
Hello, we are trying to utilize TACACS Proxy for the following scenario,
WLC < ----- > ISE2.6-Patch5 < ----- proxying ----- > Central ISE
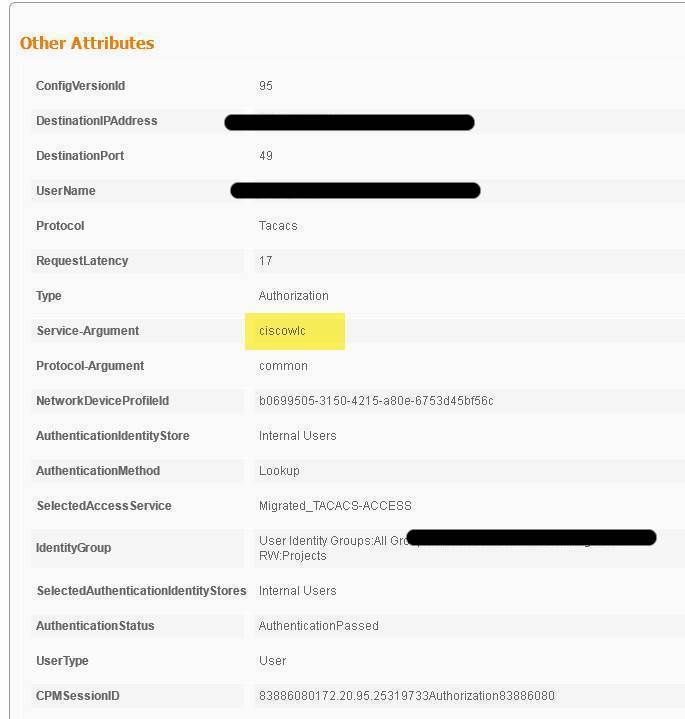
We are using the 'Service-Argument' attribute in the proxied request as below screenshot and we see this on both ISE and in packet captures. When we create a rule however it is not matched using this attribute.
The Central ISE does not match this in any of the following cases “EQUALS, CONTAINS, IN, STARTSWITH or MATCHES”.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 06:09 AM
Hi @joshhunter
To absolutely confirm that is indeed this attribute which is not letting the Central ISE match that AuthZ rule, can you please remove the condition where you are looking for this.
So, if this attribute is really the problem, you should match that particular AuthZ rule with the other two conditions in place.
Please 'RATE' and 'MARK ACCEPTED', if applicable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 06:47 AM
It needs this attribute to match on we cannot use location, device group, or IP.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 10:17 AM - edited 06-15-2020 10:20 AM
- How are you "proxying" the requests from one ISE to another?
- Which version is the 'Central ISE'?
I'd suggest you enable DEBUG for the component called 'runtime-AAA' on the central ISE and check there.
The log to check would be prrt-server.log.
Check out this article for debugs and logs: https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/212594-debugs-to-troubleshoot-on-ise.html#anc28
Please 'RATE' and 'MARK ACCEPTED', if applicable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 11:24 AM
Central ISE is running 2.7 Patch1 but tried various versions in lab environment.
TACACS PROXY using the external TACACS server pointing ISE to Central ISE.
I will give the debug ago
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 01:47 AM
Hello, I've since tried without TACACS 'Proxy' (Using External TACACS server). It still fails to match.
I tried to match using the service argument of “ciscowlc”. This didn’t match the required rule – again I tried the different options.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 08:59 AM
The debugging didn't tell me much.
I suspect it is a BUG and will log.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 09:51 AM
Alright. Please let us know the findings.
Please 'RATE' and 'MARK ACCEPTED', if applicable.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide