- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Tacas+ limit specific commands under one command layer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 06:16 AM
Hi Experts,
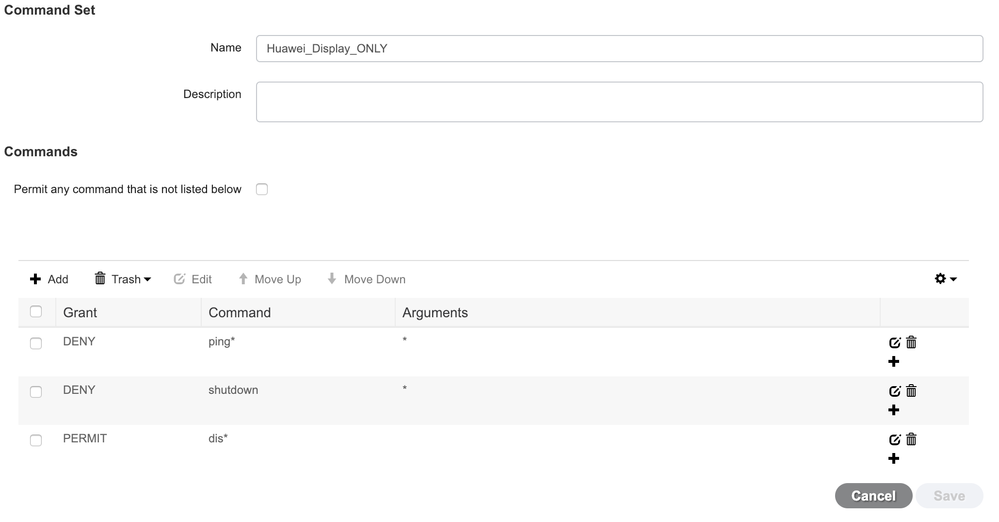
Our customer would like to use ISE (TACACS) to control the CLI command authorization.
However, they are using HUAWEI data center switch, and they want to limit “shutdown” command under ospf process, but allow this command under interface configuration, for example:
Interface 10GE1/1/1
shutdown ## Legal command
ospf 1
shutdown ## Illegal command, disallowed.
Can ISE satisfy this requirement?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:42 AM
While a command is a command so you can't tell where the shutdown is being issued you can definitely control access to the modes. Simply don't allow the user into OSPF or more to the point only allow them into "interface gig*".
Also just for clarification you don't need to put "*" in the arguments. If you don't put anything in there it assumes all arguments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 06:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 10:14 PM
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 07:42 AM
While a command is a command so you can't tell where the shutdown is being issued you can definitely control access to the modes. Simply don't allow the user into OSPF or more to the point only allow them into "interface gig*".
Also just for clarification you don't need to put "*" in the arguments. If you don't put anything in there it assumes all arguments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 03:25 PM
Hello, I read your post and I'm dealing with something similar with ISE and ACS TACACS+ Command Sets. I need to restrict Tier1 and Tier2 Admins from specific interfaces. Prior to now I use deny int* g*1/1/1, deny int* g*1/1/2 etc.. being specific to each interface; however, that no longer works. I created a few regex e.g. g?*^([1-4]\/[1-4]\/[1-4])& and it works in regex101.com however it's unrecognized in ACS or ISE command sets. All Cisco documentation points to this being a properly formatted regex.
1. Is there a difference between how ISE handles regex in Command Sets?
2. Is there a definitive document on regex for Cisco devices?
ej
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 10:45 PM
? is not quantifiable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 10:55 PM
Should "?" be replace with "." to denote a single character?
So the regex reads starting with g any other valid character and in the second position and any number of characters after that?
I was reading the using g* would only look for a continuous repeat of the letter g.
ej
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 11:08 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2019 07:10 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 06:14 PM
Very late update here but I did find the solution I was looking for to put in the command set on ISE.
| deny interface gigabitethernet [1-4]/1/[1-4] |
| permit interface gigabitethernet [1-4]/0/[1-4] |
I danced around this config with all manner of regex format
ej
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide