- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Unable to RDP to Windows Desktop after dot1x enabled.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2021 04:07 AM
Hi,
I have Cisco ISE 2.7 Patch 2 and I've just enabled dot1x on Windows desktops.
I have a policy set for Windows desktops to check for username and machine name in Active Directory.
I can see on Cisco ISE that the machine has authenticated successfully. I have a dACL and this ACL for now is allowing all traffic while I am troubleshooting this issue. I do not have AnyConnect on the desktops.
Since enabling dot1x on the desktops, I cannot RDP from anywhere on the network to the Windows machine.
Any ideas on the next steps to troubleshoot this?
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2021 07:34 AM
Hi,
Thanks for all the responses.
It looks like there were a few issues:
- The windows machines were recently patched
- Palo Alto FWs were blocking me from RDP from one subnet to another (as I was on site)
- I got access to the physical device and logged in, once I did this, the users were able to RDP, FWs not blocking it from the VPN to the subnet where the desktops are.
I am just concerned now that I will need to be at the machine and login to them all as I put dot1x onto them.
Do I need licenses for AnyConnect NAM?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2021 04:42 AM
try to Wireshark your Desktop and check RDP packet ... to double check if it is something related to your Desktop or not.
Hope this helps !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2021 10:37 AM - edited 04-01-2021 02:16 PM
What are you using authen method?
For my experience:
I had deployed 802.1x with PEAP-MSCHAPv2 and I found the RDP problem, root cause is Windows doesn't support dot1x Machine or User authent with RDP service.
If user make RDP connection to machine and logon to windows the EAP message (handshake) doesn't send to Network device, in this case authentication session still be machine and remote user were in limited connection state.
I overcome this problem by install software that can proceeds as the 802.1x supplicant such as Anyconnect NAM module, used NAM module insteat of Windows native supplicant (wired AutoConfig service).
For my solution:
Created NAM profile with anyconnect profile editor then install NAM module with NAM profile that created and disable network authen on network connection.
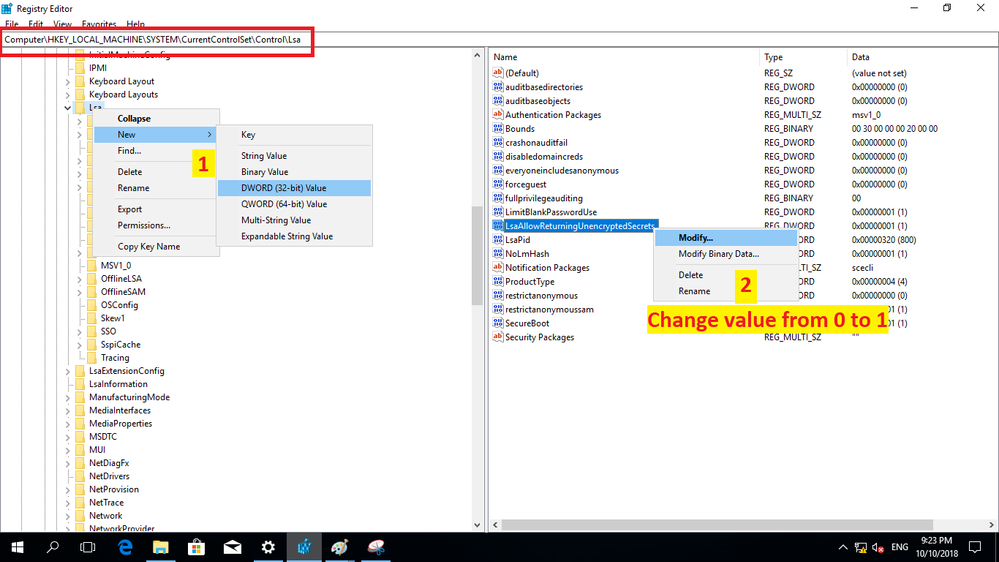
For Windows 10 you need to edit registry as below figure.
Before begin this task please consider the security affect on you machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2021 07:34 AM
Hi,
Thanks for all the responses.
It looks like there were a few issues:
- The windows machines were recently patched
- Palo Alto FWs were blocking me from RDP from one subnet to another (as I was on site)
- I got access to the physical device and logged in, once I did this, the users were able to RDP, FWs not blocking it from the VPN to the subnet where the desktops are.
I am just concerned now that I will need to be at the machine and login to them all as I put dot1x onto them.
Do I need licenses for AnyConnect NAM?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2021 12:42 PM
Microsoft does not consider an RDP login to be a real login worthy of 802.1X authentication so if that is something you are expecting you will be disappointed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2024 10:37 PM
Hi Thomas, how we can fix the issue...we are using NAC and we are facing the issue with RDP login authentication. please share solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2023 03:22 AM
use eap chaining and certificate-based authentication from machine certs.issued by your internal PKI.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide