- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Unknown AAA Authentication attempts on catalyst switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2020 02:28 PM
Wondering if anyone here has seen something like this before.
I've got a branch office switch that seems to be making some noise in our ISE Radius logs and I'm trying to track down where these goofy auth attempts are coming from. The logs keep saying that the username field is empty.
Model: WS-C2960X-24PS-L
Version: 15.2(7)E2
I can login to this switch with no issue, as can my other admins. This is the only device at this location having this issue.
Local switch Logs I see continuously show up are:
001331: May 4 16:09:03.866 CDT: %SEC_LOGIN-4-LOGIN_FAILED: Login failed [user: ] [Source: UNKNOWN] [localport: 0] [Reason: Login Authentication Failed] at 16:09:03 CDT Mon May 4 2020
001332: May 4 16:09:03.870 CDT: AAA/AUTHEN/LOGIN (00000109): Pick method list 'default'
001333: May 4 16:09:08.127 CDT: %SEC_LOGIN-4-LOGIN_FAILED: Login failed [user: ] [Source: UNKNOWN] [localport: 0] [Reason: Login Authentication Failed] at 16:09:08 CDT Mon May 4 2020
001334: May 4 16:09:08.127 CDT: AAA/AUTHEN/LOGIN (00000109): Pick method list 'default'
001335: May 4 16:09:12.283 CDT: %SEC_LOGIN-4-LOGIN_FAILED: Login failed [user: ] [Source: UNKNOWN] [localport: 0] [Reason: Login Authentication Failed] at 16:09:12 CDT Mon May 4 2020
ISE Tacacs logs:
Device Port: tty0
Failure reason:
13030 TACACS+ authentication request missing a User name |
Remote address: async
So far I've tried:
- sifting the bugs for this model of switch and couldn't see anything.
- Upgraded the firmware to the current version it's at now
- Moved the switch from RADIUS to TACACS+ to see if that changes behavior (it didn't)
Given it's an almost brand new switch and we've chosen not to SmartNet the device, the only support option I currently have is RMA and that seems a bit drastic..
I'd love to hear any suggestions you folks might have!
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 09:30 AM
@Marvin Rhoads Thanks for the note but you beat me to my reply :)
I have found the issue to be a data cable mistakenly plugged into the console port on the switch. After this cable was moved from the console port to a data port on the switch, the logs went away!
I've turned the console access back on for troubleshooting in the future.
Thanks for all of your suggestions, they were helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2020 04:49 PM
Have you tried to reload/reboot the switch? I have ran into funky issues with some of the newer code, rebooted, and then everything was fine. It is worth a try. Also, are you sure that no one or nothing is attempting to connect to the switch and authenticate? Do you have ACLs protecting your VTY lines? Are you using a terminal server to connect to this switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2020 06:20 PM
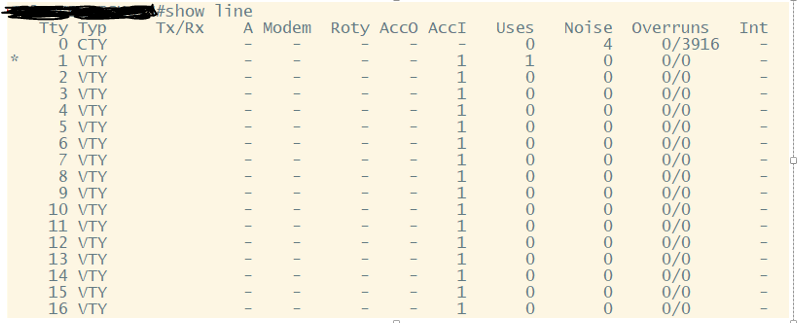
Based on the output, it looks like the noise is from tty0 line on your router. These asynchronous serial ports on the router are used for serial printers, serial modems, or dumb ASCII text terminals.
Check the output of " show line" to confirm which all lines are making noise.
If you are sure that nothing is attached on these ports, then you can configure "transport input none" and "no exec" on the tty0 line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 06:23 AM
@Colby LeMaire Appreciate the tip. I've also seen issues fixed by reboot on this model in the past. I've rebooted this morning and it appears to still be happening. To answer your questions, yes we do have an access list in place protecting the vty lines and no we are not using a terminal server.
@poongarg Here's the result from a show line. It does appear to show Overruns and Noise. I ran a clear line console 0 a few times but it doesn't seem to do anything.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 07:39 AM
@poongarg I just tried your option of doing a no exec on line 0 and that actually resolved the issue.
The odd part though, and maybe I'm just rusty on my vty/console line configurations but when I adjust line 0 config, it adjusts the console line configuration, which is OK for now, but if we ever need console access to troubleshoot we might be out of luck. Am I correct in that thought? Here's what the configuration looks like after I adjust it:
!
line con 0
exec-timeout 240 15
privilege level 15
stopbits 1
line vty 0 4
access-class 1 in vrf-also
exec-timeout 240 15
privilege level 15
logging synchronous
transport input ssh
line vty 5 15
access-class 1 in vrf-also
exec-timeout 240 15
privilege level 15
transport input ssh
!
I am double-checking with the location if there is anything physically connected to that console port. I'll report back when I get that answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 08:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 09:41 PM
It is possible it could be faulty hardware on the console port. Especially given that it cleared up when you adjusted the console port config despite there being nothing physically connected to it.
If you are in a high threat environment, there is the possibility of malicious actors physically plugging something in while no authorized staff are present. Are your physical access controls in order?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 09:30 AM
@Marvin Rhoads Thanks for the note but you beat me to my reply :)
I have found the issue to be a data cable mistakenly plugged into the console port on the switch. After this cable was moved from the console port to a data port on the switch, the logs went away!
I've turned the console access back on for troubleshooting in the future.
Thanks for all of your suggestions, they were helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2021 07:54 AM
I had a similar issue with IR829,
Try reset by tapping instead of long press the reset button.
Then try saving the config file in a notepad and upload via tftp to start-up,then upload from start-up to run config.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide