- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Using Duo with ISE for multi-factor authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2016 07:55 AM
Assume we configure ISE as the Primary and Duo as the secondary auth, which would function more like an OTP server than a Proxy. The questions I have are 1) would ISE be able to pass radius attributes to the client with Duo as the secondary and 2) does this method dilute Duo’s functionality (where ISE does not have the capability to substitute)?
In this image from Duo, ISE would be the Primary Authentication via RADIUS:
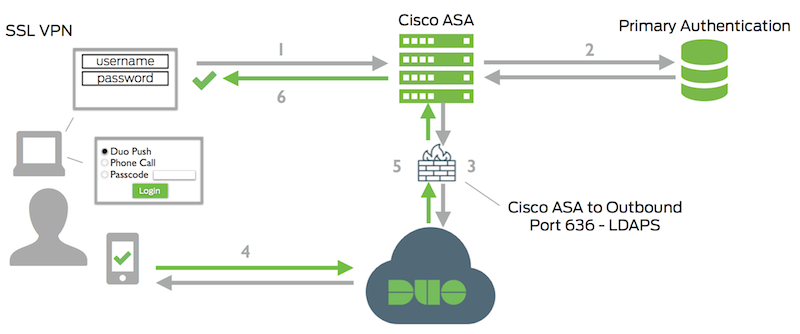
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2016 07:20 PM
At present, only ASA can perform such multi authentications. I believe you need to configure ASA to first auth against Due and then to authentication and authorization against ISE.
PS: Nice diagram. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2016 07:20 PM
At present, only ASA can perform such multi authentications. I believe you need to configure ASA to first auth against Due and then to authentication and authorization against ISE.
PS: Nice diagram. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2017 09:41 AM
Hi Hsing,
Hope you're doing well. Is this still the case with ISE 2.2, where multi-authentications are not supported? I created a RADIUS Token to point to Duo's Authentication Proxy (an on-prem appliance that proxies AAA requests to Duo's cloud). I'm trying to set up the authentication policy so primary authentication is handled by ISE, but have ISE also trigger a secondary auth to Duo. The requirement is to only configure primary authentication and authorization on the ASA and NOT configure secondary authentication on the ASA; the requirement is to have ISE or ACS trigger this secondary auth to Duo. Is this possible?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2017 02:55 PM
ISE 2.2 is still doing single auth except for EAP chaining or CWA chaining. I would suggest to bring your use case to our ISE product management team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 05:25 AM
This is a bit old, but I am struggling with this setup currently. The original configuration was ASA -> ISE -> DUO proxy. DUO proxies being setup as Radius tokens. We have suffered from many issues with this configuration, timings mainly.
So Duo has said redesign. SO now its ASA -> DUO Proxies -> ISE
The Issue I am having now is with what seems to be CoA being passed through the DUO servers from ASA to ISE and ISE to ASA when needing my anyconnect clients to get dACLs. Anyone else running into similar issues?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 05:26 PM - edited 12-14-2018 06:00 AM
I'm seeing the same thing.
When it's ASA -- Duo Proxy -- ISE, I'm not able to push a dACL to my VPN session. I do see reference to the ACL name in the Duo Proxy debug logs:
2018-12-13T14:11:05-0500 [RadiusClient (UDP)] '<redacted>\x01@ACS:CiscoSecure-Defined-ACL=#ACSACL#-IP-BLOCK-RFC1918-5b16ae0f\x1a\x15\x00\x007c\x06\x0fBLOCK-RFC1918'
The public IP address of my device connecting via VPN is listed under 'Access Device' info in the Duo dashboard. I believe this is what's used for any policy enforced by Duo.
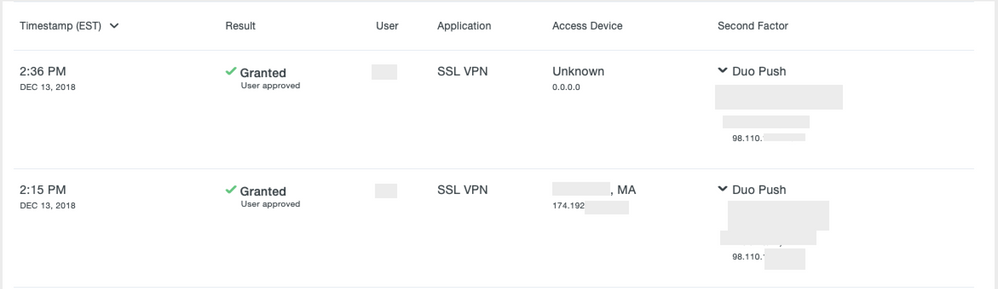
If I change my configuration to use Duo Proxy as a token server, my dACL gets applied successfully, but I lose the IP address being reported to the Duo dashboard, which poses a problem for folks trying to apply policies from Duo.
Is there a way to get the public IP of the device on the Duo dashboard and a dACL applied to the VPN session?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 05:37 AM
What do you mean by use duo proxy as token server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 06:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 06:27 AM
So the ASA does radius to ISE, then ISE policy set says if this then use radius token duo.
Timing issues are horrific. I think the issue is that ASA can't pass CoA through DUO proxy and vice versa.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide