- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Using IP address/subnet as an authorization rule in an ISE policy set?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 10:07 AM - edited 02-21-2020 11:03 AM
Scenario:
I have a MAB policy set where I permit various endpoints with some different profiler policies/logical profiles I’ve defined. Then the last rule is a default deny access.
We have a subnet which we allow guests to connect on, and we want them to get permitted regardless of what device they bring. So I want to add a rule just before the last rule which would permit any device coming from that subnet – I don’t care what profiler policy it matched. The problem is I can’t figure out a way to get this to work.
What I’ve tried/considered:
- Create an “Endstation Network Condition” matching my subnet and use this in the policy rule. This unfortunately doesn’t work when I use a subnet but I noticed that it works if I use MAC addresses, presumably because the Radius Caller Station ID is a MAC address.
- Create a condition to match on Radius Framed-IP-Address. This would almost work but the only options ISE gives you are Equals and Not Equals. I’m trying to match a /14 so listing every single IP address out isn’t possible.
- Creating a profiler policy with a single check (IP address starts with) and giving it a really high certainty factor to outweigh all other profiler policies. This technically would work but then I’d lose the easy visibility of whether something is a Macbook/Windows Workstation/etc. because the endpoint profile would be getting overridden with this new one. That won’t work for us.
- Give those guest ports an interface description like “Guest” and then in ISE use the SNMP probe to see this description and make that into a condition? I haven’t been able to get ISE to pull the interface description though, it just says ifDescr is for example “GigabitEthernet0/1”.
Any ideas on how to accomplish this are appreciated.
Thanks!
Shaan
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 07:42 AM
I suggest 'VLAN ID in NAS-ID attribute' option instead of 'mab eap'. Both are limited to MAB, but first option doesn't alter identity and simpler to implement.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 11:17 AM - edited 09-15-2020 09:50 AM
Hello, We can have the domain base policy. Thing your organization i using the certain domain, apart from domain falls under different rule ( Guest will we in different domain or work group ). Create a /20 segment restricted VN and you can have the specific access allowed for the created segment. Create a rule with non domain laptops falls to this rule and the non domain laptops falls under non-compliant as well. Access restriction for posture non-compliant machines – we need to create an SGT (say Posture_NC) and define the policy in DNA to restrict the access to ISE. Posture NC machines also we will use the VN which is configured in a different VN with restricted access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 08:51 AM
i see you posted to our internal PM community. Why can't you just assign an SGT to utilize? Or if guest flow or guest endpoint give a different authorization profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 09:14 AM
Parent policy: Domain Host Check -- AD-Host-Exists
Child policy: Macbook Check -- whatever attribute you decide to match
Then you will know if a host is profiled as Macbook Check that it is a) not a member of the domain b)a guest workstation identified as a MAC
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2019 06:45 AM
Mike,
Interesting idea. In this case it wouldn't work for me though because we also have a bunch of other devices (security cameras, printers, etc.) that are allowed onto the network using profiling and they aren't joined to the domain. Cisco TAC and AS also looked into this and they said this specific flow can't be done today. I think a feature request is in the works though.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2019 06:54 PM
Option 4 would be the best. Currently the IOS cannot send interface description, but can send data VLAN ID/Name that the interface is configured with 'switchport access vlan XXX' command. The other option is to use 'mab eap' on the specific guest interfaces where ISE can differentiate based on MAB request protocol. I have documented few options here: https://community.cisco.com/t5/security-documents/advanced-ise-tips-to-make-your-deployment-easier/ta-p/3850189#toc-hId--1934452079
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 07:34 AM
Thanks so much for this info. It would be great if IOS could send the interface description. And VLAN ID/Name is useful too, although unfortunately most of our switches are on 16.x but before 16.12 where this was fixed. I will try out the "mab eap" idea and report back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 07:42 AM
I suggest 'VLAN ID in NAS-ID attribute' option instead of 'mab eap'. Both are limited to MAB, but first option doesn't alter identity and simpler to implement.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 08:53 AM
I've been testing this out and I am able to get it working. One caveat I have noticed is that if the MAC address is already in ISE, I have to delete the endpoint first for the new NAS-Identifier attribute to show up in ISE (and thus hit the correct authorization rule).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 09:13 PM
The caveat seems due to how the rules are ordered in the authorization policy of your policy set. If you would like such to pre-exempt all others, we could move it to Local/Global Exceptions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 08:27 AM
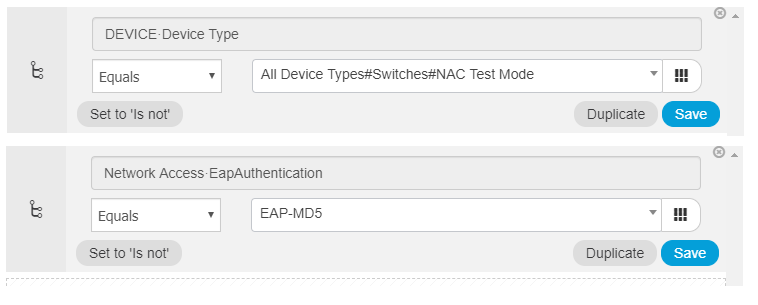
I tried the 'mab eap' method but am running into an issue. I configured 'mab eap' on the switchport, and in ISE I configured the policy condition to simply match the switch the request is coming from, and then an authorization rule for eap authentication = eam-md5. However on the switch, when the endpoint connects, it looks like this:
Switch#
May 6 10:24:19.540: %DOT1X-5-FAIL: Authentication failed for client (949a.a927.9cb2) on Interface Gi0/10 AuditSessionID 0A909A4800003EC8EA4D4CC9
May 6 10:24:19.558: %MAB-5-FAIL: Authentication failed for client (949a.a927.9cb2) on Interface Gi0/10 AuditSessionID 0A909A4800003EC8EA4D4CC9
Switch#sh auth sess
Interface MAC Address Method Domain Status Fg Session ID
Gi0/10 949a.a927.9cb2 N/A UNKNOWN Unauth 0A909A4800003EC8EA4D4CC9
Here's what I have in ISE:
Can you tell me what I might be doing wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 09:18 PM
As you have a working solution, I would suggest you not to continue with this other idea of using EAP MAB.
Otherwise, please involve TAC and AS to troubleshoot. It's hard for us to tell what the issue might be without looking at the full policy sets and the auth reports.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide