- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Why or what is need of Cisco ISE automatically scan NMAP in thhe Network & Saves log ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 11:56 PM - edited 02-21-2020 11:09 AM
Why Cisco ISE NMAP scan of the Network & saves log ?
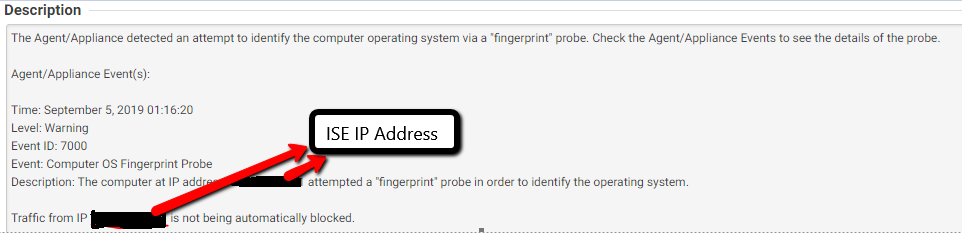
My security team find alert in to their system for one IP that scan the Server. PFB Alert.
After I`ve checked the ISE logs & I found below NMAP log & its saves the output to Nmap.log file.
# Nmap 7.00 scan initiated Thu Sep 5 01:16:21 2019 as: /usr/bin/nmap -v -sU -p
U:161,162 -Pn --disable-arp-ping -oN /opt/CSCOcpm/logs/nmap.log --append-output
-oX - (File Server IP)
--
Nmap scan report for (File Server IP)
ISE NMAP scans mostly all the IP of network. From output We can say that NMAP scans UDP 161, 162 port which is SNMP ports.
My question is Why ISE scans via NMAP automatically or what is need for scan NMAP?
PLS Help !!!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 01:06 AM
Hi,
ISE uses NMAP in order to profile the devices that authenticate to ISE to determine make/model, OS version etc. The NMAP probe could be disabled, but you do get a lot of useful information from it. I'd suggest whitelisting the ISE IP addresses and let them run the NMAP Probes.
Here is the ISE profiling guide with more information.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 01:06 AM
Hi,
ISE uses NMAP in order to profile the devices that authenticate to ISE to determine make/model, OS version etc. The NMAP probe could be disabled, but you do get a lot of useful information from it. I'd suggest whitelisting the ISE IP addresses and let them run the NMAP Probes.
Here is the ISE profiling guide with more information.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 01:25 AM
will match the device against a parent profile (for example Cisco Access
Point) using enabled probes such as radius, cdp, etc. Most of parent
profiles have NMAP enabled to perform NMAP scan against the device on 1st
match to detect its specific model such as Cisco Aironet 3802
You can enable dot1x on client endpoints instead of servers to avoid
similar cases.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide