- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: WIndows 10 adding "host/" to the username during eap-tls and or peap
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 10:19 AM
Standalone Windows 10 laptop using native supplicant and ISE 2.2. Setting up machine type eap-tls authentication for windows. How can you get rid of the "host/" that is prepended to the identity when trying to authenticate with ISE? Where is that "Host/" coming from (not on the CN cert nor as hostname).
Second issue - why would client reject ISE's local cert when on the client the "verify the server's identity by validating cert' is NOT selected.
Thanks for input!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2020 08:03 PM
The prefix of host/ comes from the fact that machine authentication is being done. The AD joined machine is authenticating because the machine booted up, or user logged out. If you don't want to do machine auth, then change the supplicant to do user auth only. But then the machine won't be auth'd if no user is logged in.
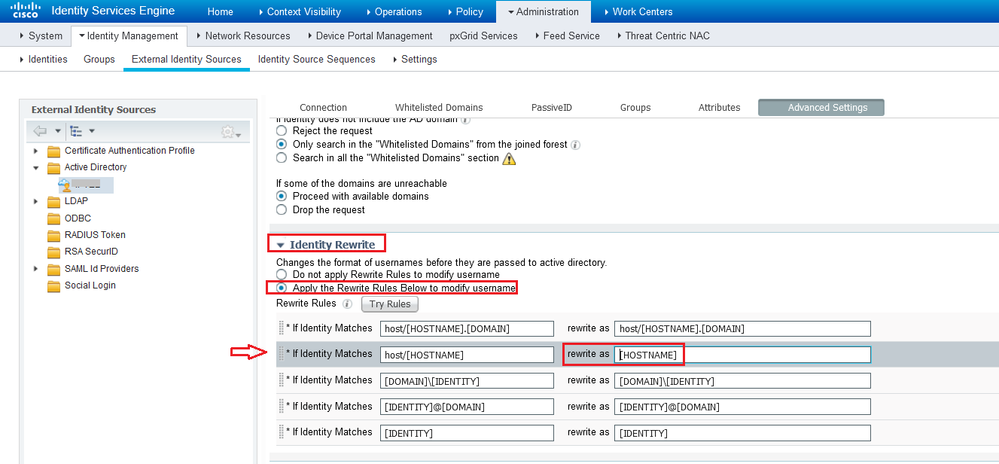
If you want to strip the "host/" prefix before sending the request to AD, then you can perform this manipulation in the ISE External identities menu option:
Second issue: The client would reject it if the ISE EAP certificate has expired or is invalid (wrong EKU for example). You'd need to give more details about the ISE EAP certificate that you are using.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2020 08:03 PM
The prefix of host/ comes from the fact that machine authentication is being done. The AD joined machine is authenticating because the machine booted up, or user logged out. If you don't want to do machine auth, then change the supplicant to do user auth only. But then the machine won't be auth'd if no user is logged in.
If you want to strip the "host/" prefix before sending the request to AD, then you can perform this manipulation in the ISE External identities menu option:
Second issue: The client would reject it if the ISE EAP certificate has expired or is invalid (wrong EKU for example). You'd need to give more details about the ISE EAP certificate that you are using.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2023 07:51 AM
Hi
We enabled both machine AND user authentication on the supplicant but the ISE is authenticating only the Machine name.
When I go to Context visibility > endpoints to see logs, I see only the machine name on the attributes for the authenticated machine (it is like the the supplicant only sends one name : either the machine or username).
We want to keep both user and machine name authentication so we can use both on the authorization rules (username + machine names that have an antivirus installed).
Is there a way to do that without forcing only the supplicant to send usernames ?
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2023 09:58 AM
You would be better served to ask this as a new question since it has little to do with the original ask.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2023 01:47 AM
Hi Louey,
You can perform Machine+User authentication using EAP-Chaining on the Windows Native Supplicant. This can be achieved using the TEAP protocol.
Sharing the doc for reference : https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216510-eap-chaining-with-teap.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2023 05:34 PM
the problem with EAP-Chaining it will causes problems to new users trying to login for the first time into their machines especially those working remotely and have their laptops imaged and send to their home addresses. they won't be able to login unless you break the eap-chain or uninstall anyconnect and redeploy it again after user login.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide