- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: ASA - packet tracer - cant go outside (icmp, http)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 09:19 AM
Hello team,
I'am new on network topic, and facing an issue on my current packet tracer lab.
I have 3 INTERNAL vlans behind a router :
| VLAN-X > 7 | 192.168.1.0 | /26 |
| VLAN-Y > 15 | 192.168.1.64 | /26 |
| VLAN-Z > 22 | 192.168.1.128 | /26 |
I have an ASA 5506 firewall connected to 3 NICs connected to 3 networks :
INTERNAL (linked to my router with OSPF configured) :
| ASA NTWRK | 192.168.1.192 | /26 |
DMZ:
| DMZ | 192.168.2.0 | /24 |
PUBLIC (Internet
| ISP NTWRK | 64.100.100.0 | /24 |
I configured my PAT like follwing on ASA :
conf term
object network VLAN-X
subnet 192.168.1.0 255.255.255.192
nat (INTERNAL,PUBLIC) dynamic interface
end
conf term
object network VLAN-Y
subnet 192.168.1.64 255.255.255.192
nat (INTERNAL,PUBLIC) dynamic interface
end
conf term
object network VLAN-Z
subnet 192.168.1.128 255.255.255.192
nat (INTERNAL,PUBLIC) dynamic interface
end
For DMZ i am able to ping outside and to browse DMZ webserver from OUTSIDE also thanks to that rule :
configure terminal
object network Outside_To_Inside_WebServer
host 192.168.2.10
nat (DMZ,PUBLIC) static 88.40.12.2
exit
conf terminal
access-list Outside_To_Inside_WebServer permit icmp any host 88.40.12.2
access-list Outside_To_Inside_WebServer permit tcp any host 192.168.2.10 eq www
access-group Outside_To_Inside_WebServer in interface PUBLIC
end
My issue is that from my router i am to ping outside, but from any VLAN i cant !
I cant find where this is comming from. Please help me.
Thank you
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2022 01:19 PM
Hi Georg ! Thank you for your help
Finally with my teacher we figured out where the issue was comming from !
1 - Route missing on the ISP router that has been added to point to ASA
2 - Inspect ICMP that is a bit bugged so we have to delete and recreate the entire policy :
#Inspect ICMP on ASA :
configure terminal
NO policy-map global_policy
exit
configure terminal
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect tftp
inspect icmp
exit
write memory3 - Dont forger to reapply it once rebuilt
#Apply the fresh policy to be taken into account for ICMP rule :
no service-policy global_policy global
service-policy global_policy globalThis fixed my issue !
Thank you all for your time , really appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 09:26 AM
object network VLAN--
subnet any
nat (INTERNAL,PUBLIC) dynamic interface
since the subnet connect to router is different than object dynamic PAT
use any instead
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 10:29 AM - edited 09-26-2022 10:46 AM
Hi, i tried but it's not working on packet tracer 8.1.1 , I have to specify a subnet, thinks its mandatory..
I can ping outside from my router :
R1#ping 64.100.100.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 64.100.100.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/0 ms
R1#
But from my internal VLAN it's KO, even if i can ping the INTERNAL Interface of my ASA!
Why my router can go outside whereas from my internal VLAN ping isn't working ? Something wrong with my router or my ASA ?
I'am lost
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 10:48 AM
OK,
let start from client
each client have GW point to Router Interface
Router have default route toward ASA IN interface
ASA have static or route (via OSPF ) toward Router for each VLAN connect to router
can you confirm above ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 11:25 AM
Hi, thank you for your time sir !
I used that network subnetted VLSM with /26 mask : 192.168.1.0
1- each client have GW point to Router Interface :
Yes, each client has it's proper gateway related to its vlan (ip addresses are delivered through DHCP from the router itself)
VLAN X : G0//0.7 - 192.168.1.1
VLAN Y : G0/0.15 - 192.168.1.65
VLAN Z : G0/0.22 - 192.168.1.129
Router have default route toward ASA IN interface :
My router route confighuration :
R1#show ip route
Gateway of last resort is 192.168.1.194 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.10.2.0/24 is directly connected, Loopback0
L 10.10.2.2/32 is directly connected, Loopback0
88.0.0.0/30 is subnetted, 1 subnets
O 88.40.12.0/30 [110/2] via 192.168.1.194, 03:44:26, GigabitEthernet0/1
192.168.1.0/24 is variably subnetted, 8 subnets, 2 masks
C 192.168.1.0/26 is directly connected, GigabitEthernet0/0.7
L 192.168.1.1/32 is directly connected, GigabitEthernet0/0.7
C 192.168.1.64/26 is directly connected, GigabitEthernet0/0.15
L 192.168.1.65/32 is directly connected, GigabitEthernet0/0.15
C 192.168.1.128/26 is directly connected, GigabitEthernet0/0.22
L 192.168.1.129/32 is directly connected, GigabitEthernet0/0.22
C 192.168.1.192/26 is directly connected, GigabitEthernet0/1
L 192.168.1.193/32 is directly connected, GigabitEthernet0/1
O 192.168.2.0/24 [110/2] via 192.168.1.194, 03:44:26, GigabitEthernet0/1
O*E2 0.0.0.0/0 [110/1] via 192.168.1.194, 03:44:26, GigabitEthernet0/1
R1#
ASA have static or route (via OSPF ) toward Router for each VLAN connect to route :
My ASA routes :
Gateway of last resort is 88.40.12.1 to network 0.0.0.0
10.0.0.0/32 is subnetted, 1 subnets
O IA 10.10.2.2 255.255.255.255 [110/2] via 192.168.1.193, INTERNAL, 01:43:04, GigabitEthernet1/1
88.0.0.0/30 is subnetted, 2 subnets
C 88.0.0.0 255.255.255.252 is directly connected, PUBLIC, GigabitEthernet1/3
C 88.40.12.0 255.255.255.252 is directly connected, PUBLIC, GigabitEthernet1/3
192.168.1.0/26 is subnetted, 4 subnets
C 192.168.1.0 255.255.255.192 is directly connected, INTERNAL, GigabitEthernet1/1
O 192.168.1.64 255.255.255.192 [110/2] via 192.168.1.193, INTERNAL, 03:43:04, GigabitEthernet1/1
O 192.168.1.128 255.255.255.192 [110/2] via 192.168.1.193, INTERNAL, 03:43:04, GigabitEthernet1/1
C 192.168.1.192 255.255.255.192 is directly connected, INTERNAL, GigabitEthernet1/1
C 192.168.2.0 255.255.255.0 is directly connected, DMZ, GigabitEthernet1/2
S* 0.0.0.0/0 [1/0] via 88.40.12.1
ASA#
My ASA Nat configuration where i can see only DMZ :
ASA#show nat
Auto NAT Policies (Section 2)
1 (INTERNAL) to (PUBLIC) source dynamic LAN interface
translate_hits = 0, untranslate_hits = 0
2 (DMZ) to (PUBLIC) source static Outside_To_Inside_WebServer 88.40.12.2
translate_hits = 0, untranslate_hits = 0
ASA#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2022 12:40 PM
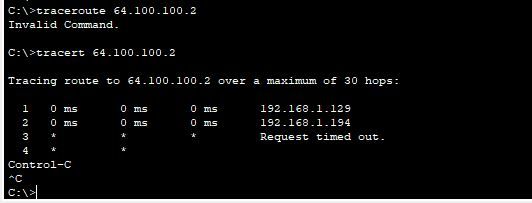
OK, can you try traceroute from PC, see where the traffic stop
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2022 03:16 AM
you must specify NAT.
that ok
add new object with
subnet 0.0.0.0 0.0.0.0 <<- to include all subnet not direct connect to ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
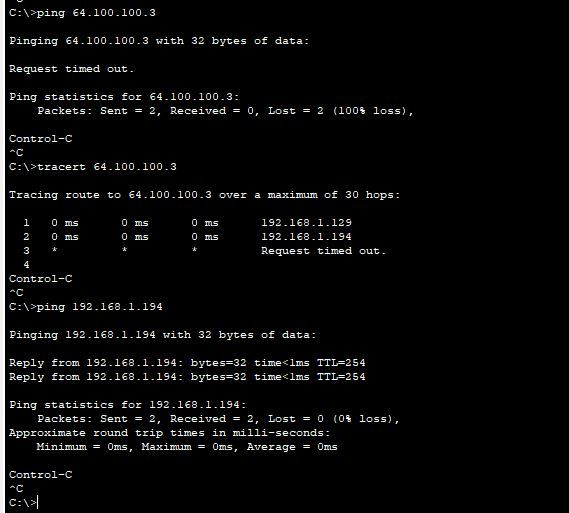
09-26-2022 01:46 PM
Hi sir,
Traceroute stops at the inside interface on my ASA,
But from my Router its working to ping outside,
R1#ping 64.100.100.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 64.100.100.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/0 ms
R1#ping 64.100.100.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 64.100.100.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
R1#- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2022 07:54 AM
Hello,
post your zipped Packet Tracer project (.pkt) file. The ASA in Packet Tracer has quite a few quirks...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2022 01:19 PM
Hi Georg ! Thank you for your help
Finally with my teacher we figured out where the issue was comming from !
1 - Route missing on the ISP router that has been added to point to ASA
2 - Inspect ICMP that is a bit bugged so we have to delete and recreate the entire policy :
#Inspect ICMP on ASA :
configure terminal
NO policy-map global_policy
exit
configure terminal
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect tftp
inspect icmp
exit
write memory3 - Dont forger to reapply it once rebuilt
#Apply the fresh policy to be taken into account for ICMP rule :
no service-policy global_policy global
service-policy global_policy globalThis fixed my issue !
Thank you all for your time , really appreciated.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide