- Cisco Community
- Technology and Support
- Networking
- Network Management
- Firepower <- S2S -> RRAS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower <- S2S -> RRAS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2021 06:06 PM
Hello, I need to configure an S2S VPN between Firepower and RRAS, without success. There is always an error in pre-shared ikev2 authentication.
Has anyone managed to make it work between these two products?
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 12:22 AM
what is RRAS (windows ?)? what are the errors you see on FP or RRAS side, check the basic settings and verify the configuration.
make sure it has reachability.
as per the below message some information not right, what is DH group ? if you trying more than 5, try DH 5 (i have observed some cases FP not able to sync with other vendors.
pre-shared ikev2 authentication.
post the complete log from Firepower and other logs will be useful to understand the issue here
here is troubleshoot basic guide :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 02:11 AM
exact Windows Server RRAS.
I don't have access to Firepower (another company). They passed me the setup. But I didn't find any way in RRAS to configure these options, the only option I found was to put the key in ikeav2.
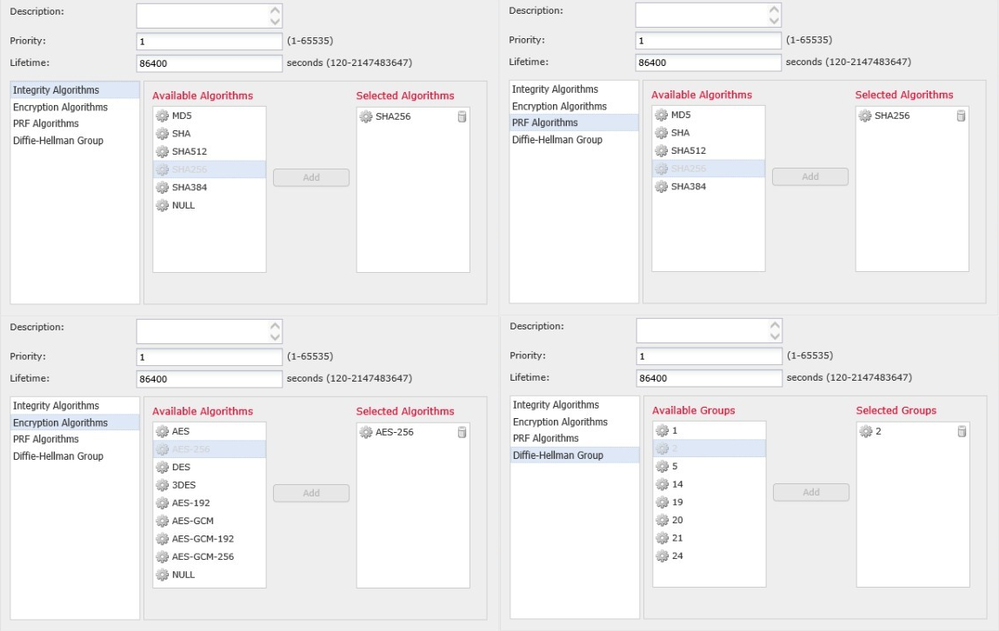
Config Firepower:
IKEV2 Parameters
IKE Encryption: AES256
IKE Authentication: SHA
Diffie-Hellman Group: Group 2
IKE Lifetime: 1440 min
IPSec Parameters
ESP Encryption: AES256
ESP Authentication: SHA
Perfect Forward Secrecy: Group 2
ESP Lifetime: 60 min
Where can I check the firepower log (ask another company)? to try to identify the problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2021 05:40 AM
Hi,
I was unable to obtain the Cisco log.
I am looking at the connection packets to understand what the problem is.
I am configuring the IKEv2 policy (Cisco)
Integrity: SHA256 Encryption: AES256 PRF: SHA256 DH: Group 2
I set up the same thing in RRAS. The policy error does not match.
Now if I set up wrong in RRAS to connect it accepts the policy but the key error.
RRAS == Cisco
Package Send:
Internet Security Association and Key Management Protocol
Initiator SPI: 3dad11ea0b9f82f3
Responder SPI: 0000000000000000
Next payload: Security Association (33)
Version: 2.0
Exchange type: IKE_SA_INIT (34)
Flags: 0x08 (Initiator, No higher version, Request)
Message ID: 0x00000000
Length: 408
Payload: Security Association (33)
Next payload: Key Exchange (34)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 48
Payload: Proposal (2) # 1
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 44
Proposal number: 1
Protocol ID: IKE (1)
SPI Size: 0
Proposal transforms: 4
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 12
Transform Type: Encryption Algorithm (ENCR) (1)
Reserved: 00
Transform ID (ENCR): ENCR_AES_CBC (12)
Transform Attribute (t=14,l=2): Key Length: 256
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Integrity Algorithm (INTEG) (3)
Reserved: 00
Transform ID (INTEG): AUTH_HMAC_SHA2_256_128 (12)
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Pseudo-random Function (PRF) (2)
Reserved: 00
Transform ID (PRF): PRF_HMAC_SHA2_256 (5)
Payload: Transform (3)
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 8
Transform Type: Diffie-Hellman Group (D-H) (4)
Reserved: 00
Transform ID (D-H): Alternate 1024-bit MODP group (2)
Payload: Key Exchange (34)
Next payload: Nonce (40)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 136
DH Group #: Alternate 1024-bit MODP group (2)
Reserved: 0000
Key Exchange Data: c015fdf5b2e944557c2810608059d37a6d2fda7767d5916ca6463e5216c609d67a1487c6…
Payload: Nonce (40)
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 52
Nonce DATA: 629f3bf55ede76068a9234b6b399aa30ebc5b9298521e21ce2e76dc2b501a0458679c93c…
Payload: Notify (41) - NAT_DETECTION_SOURCE_IP
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: RESERVED (0)
SPI Size: 0
Notify Message Type: NAT_DETECTION_SOURCE_IP (16388)
Notification DATA: f59242f65144cf85a23a908af75607dfe0c08744
Payload: Notify (41) - NAT_DETECTION_DESTINATION_IP
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: RESERVED (0)
SPI Size: 0
Notify Message Type: NAT_DETECTION_DESTINATION_IP (16389)
Notification DATA: 72d3f783abeac8773500cc20684141f5f1d32023
Payload: Vendor ID (43) : MS NT5 ISAKMPOAKLEY
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 24
Vendor ID: 1e2b516905991c7d7c96fcbfb587e46100000009
Vendor ID: MS NT5 ISAKMPOAKLEY
MS NT5 ISAKMPOAKLEY: Unknown (9)
Payload: Vendor ID (43) : MS-Negotiation Discovery Capable
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 20
Vendor ID: fb1de3cdf341b7ea16b7e5be0855f120
Vendor ID: MS-Negotiation Discovery Capable
Payload: Vendor ID (43) : Microsoft Vid-Initial-Contact
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 20
Vendor ID: 26244d38eddb61b3172a36e3d0cfb819
Vendor ID: Microsoft Vid-Initial-Contact
Payload: Vendor ID (43) : Unknown Vendor ID
Next payload: NONE / No Next Payload (0)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 24
Vendor ID: 01528bbbc00696121849ab9a1c5b2a5100000002
Vendor ID: Unknown Vendor IDPackage Received:
Internet Security Association and Key Management Protocol
Initiator SPI: 3dad11ea0b9f82f3
Responder SPI: d5efcb9fa54d702e
Next payload: Notify (41)
Version: 2.0
Exchange type: IKE_SA_INIT (34)
Flags: 0x20 (Responder, No higher version, Response)
Message ID: 0x00000000
Length: 36
Payload: Notify (41) - NO_PROPOSAL_CHOSEN
Next payload: NONE / No Next Payload (0)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 8
Protocol ID: IKE (1)
SPI Size: 0
Notify Message Type: NO_PROPOSAL_CHOSEN (14)
Notification DATA: <MISSING>Error: Policy match error
RRAS <> Cisco
Package Send:
Internet Security Association and Key Management Protocol
Initiator SPI: 8a188de635d2e19f
Responder SPI: 0000000000000000
Next payload: Security Association (33)
Version: 2.0
Exchange type: IKE_SA_INIT (34)
Flags: 0x08 (Initiator, No higher version, Request)
Message ID: 0x00000000
Length: 408
Payload: Security Association (33)
Next payload: Key Exchange (34)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 48
Payload: Proposal (2) # 1
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 44
Proposal number: 1
Protocol ID: IKE (1)
SPI Size: 0
Proposal transforms: 4
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 12
Transform Type: Encryption Algorithm (ENCR) (1)
Reserved: 00
Transform ID (ENCR): ENCR_AES_CBC (12)
Transform Attribute (t=14,l=2): Key Length: 256
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Integrity Algorithm (INTEG) (3)
Reserved: 00
Transform ID (INTEG): AUTH_HMAC_SHA1_96 (2)
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Pseudo-random Function (PRF) (2)
Reserved: 00
Transform ID (PRF): PRF_HMAC_SHA1 (2)
Payload: Transform (3)
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 8
Transform Type: Diffie-Hellman Group (D-H) (4)
Reserved: 00
Transform ID (D-H): Alternate 1024-bit MODP group (2)
Payload: Key Exchange (34)
Next payload: Nonce (40)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 136
DH Group #: Alternate 1024-bit MODP group (2)
Reserved: 0000
Key Exchange Data: 0b9185180331192f6538fbae3156132ceab8f8fa524163d0874a50289a884efa703ebd29…
Payload: Nonce (40)
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 52
Nonce DATA: 9d0201faa47e58bfc282bf1be0ac3bc308bf53b6c25c83a9b3c56bbd1602decb96185b31…
Payload: Notify (41) - NAT_DETECTION_SOURCE_IP
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: RESERVED (0)
SPI Size: 0
Notify Message Type: NAT_DETECTION_SOURCE_IP (16388)
Notification DATA: e52d8a127f4989c09862bf281e78c6f499fcb58f
Payload: Notify (41) - NAT_DETECTION_DESTINATION_IP
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: RESERVED (0)
SPI Size: 0
Notify Message Type: NAT_DETECTION_DESTINATION_IP (16389)
Notification DATA: 61ed76631036db1bb4ee1dff8853806a21ad8826
Payload: Vendor ID (43) : MS NT5 ISAKMPOAKLEY
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 24
Vendor ID: 1e2b516905991c7d7c96fcbfb587e46100000009
Vendor ID: MS NT5 ISAKMPOAKLEY
MS NT5 ISAKMPOAKLEY: Unknown (9)
Payload: Vendor ID (43) : MS-Negotiation Discovery Capable
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 20
Vendor ID: fb1de3cdf341b7ea16b7e5be0855f120
Vendor ID: MS-Negotiation Discovery Capable
Payload: Vendor ID (43) : Microsoft Vid-Initial-Contact
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 20
Vendor ID: 26244d38eddb61b3172a36e3d0cfb819
Vendor ID: Microsoft Vid-Initial-Contact
Payload: Vendor ID (43) : Unknown Vendor ID
Next payload: NONE / No Next Payload (0)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 24
Vendor ID: 01528bbbc00696121849ab9a1c5b2a5100000002
Vendor ID: Unknown Vendor IDPackage Received:
Internet Security Association and Key Management Protocol
Initiator SPI: 8a188de635d2e19f
Responder SPI: aa21e1fc8564fa4d
Next payload: Security Association (33)
Version: 2.0
Exchange type: IKE_SA_INIT (34)
Flags: 0x20 (Responder, No higher version, Response)
Message ID: 0x00000000
Length: 531
Payload: Security Association (33)
Next payload: Key Exchange (34)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 48
Payload: Proposal (2) # 1
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 44
Proposal number: 1
Protocol ID: IKE (1)
SPI Size: 0
Proposal transforms: 4
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 12
Transform Type: Encryption Algorithm (ENCR) (1)
Reserved: 00
Transform ID (ENCR): ENCR_AES_CBC (12)
Transform Attribute (t=14,l=2): Key Length: 256
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Pseudo-random Function (PRF) (2)
Reserved: 00
Transform ID (PRF): PRF_HMAC_SHA1 (2)
Payload: Transform (3)
Next payload: Transform (3)
Reserved: 00
Payload length: 8
Transform Type: Integrity Algorithm (INTEG) (3)
Reserved: 00
Transform ID (INTEG): AUTH_HMAC_SHA1_96 (2)
Payload: Transform (3)
Next payload: NONE / No Next Payload (0)
Reserved: 00
Payload length: 8
Transform Type: Diffie-Hellman Group (D-H) (4)
Reserved: 00
Transform ID (D-H): Alternate 1024-bit MODP group (2)
Payload: Key Exchange (34)
Next payload: Nonce (40)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 136
DH Group #: Alternate 1024-bit MODP group (2)
Reserved: 0000
Key Exchange Data: 360234bb86862e89a184b28803dcbf137d88b436822ff309595b678d07fbf202e5ad1da3…
Payload: Nonce (40)
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 68
Nonce DATA: 338c8ce7979efc05808d7e2229a80b88f0427640a6a95d440119cb5aa023db807b85cf23…
Payload: Vendor ID (43) : Cisco Delete Reason Supported
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 23
Vendor ID: 434953434f2d44454c4554452d524541534f4e
Vendor ID: Cisco Delete Reason Supported
Payload: Vendor ID (43) : Cisco Copyright
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 59
Vendor ID: 434953434f28434f505952494748542926436f7079726967687420286329203230303920…
Vendor ID: Cisco Copyright
Payload: Notify (41) - NAT_DETECTION_SOURCE_IP
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: IKE (1)
SPI Size: 0
Notify Message Type: NAT_DETECTION_SOURCE_IP (16388)
Notification DATA: 563666e67b4bf5cb6ee8a38d8e2166ff88e16d46
Payload: Notify (41) - NAT_DETECTION_DESTINATION_IP
Next payload: Certificate Request (38)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 28
Protocol ID: IKE (1)
SPI Size: 0
Notify Message Type: NAT_DETECTION_DESTINATION_IP (16389)
Notification DATA: de5ed17d2a686b5a9548d7ef83e3f9726d566af1
Payload: Certificate Request (38)
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 85
Certificate Type: X.509 Certificate - Signature (4)
Certificate Authority Data: a62a352d187cdb15dea2d4b8d5ac27915da743d3
Certificate Authority Data: 7982cbe285eadebf6480f52fce697d743226a3d6
Certificate Authority Data: 51bc4f771708cfe509dde9eaa5548e91c0677853
Certificate Authority Data: 3e06f14b7fd875e16228e1fe25a11974f5b51d23
Payload: Notify (41) - IKEV2_FRAGMENTATION_SUPPORTED
Next payload: Vendor ID (43)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 8
Protocol ID: RESERVED (0)
SPI Size: 0
Notify Message Type: IKEV2_FRAGMENTATION_SUPPORTED (16430)
Notification DATA: <MISSING>
Payload: Vendor ID (43) : Cisco Fragmentation
Next payload: NONE / No Next Payload (0)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 20
Vendor ID: 4048b7d56ebce88525e7de7f00d6c2d3
Vendor ID: Cisco FragmentationPackage Send 2:
Internet Security Association and Key Management Protocol
Initiator SPI: 8a188de635d2e19f
Responder SPI: aa21e1fc8564fa4d
Next payload: Encrypted and Authenticated (46)
Version: 2.0
Exchange type: IKE_AUTH (35)
Flags: 0x08 (Initiator, No higher version, Request)
Message ID: 0x00000001
Length: 316
Payload: Encrypted and Authenticated (46)
Next payload: Identification - Initiator (35)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 288
Initialization Vector: 1ff7a0a5
Encrypted DataPackage Received 2:
Internet Security Association and Key Management Protocol
Initiator SPI: 8a188de635d2e19f
Responder SPI: aa21e1fc8564fa4d
Next payload: Encrypted and Authenticated (46)
Version: 2.0
Exchange type: IKE_AUTH (35)
Flags: 0x20 (Responder, No higher version, Response)
Message ID: 0x00000001
Length: 76
Payload: Encrypted and Authenticated (46)
Next payload: Notify (41)
0... .... = Critical Bit: Not critical
.000 0000 = Reserved: 0x00
Payload length: 48
Initialization Vector: e86cfb41
Encrypted DataError: IKE authentication credentials are unacceptable
Any idea what's going on?
It doesn't make any sense.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide