- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: Issues bridging networks via seperate VLANs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Issues bridging networks via seperate VLANs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2019 09:11 AM
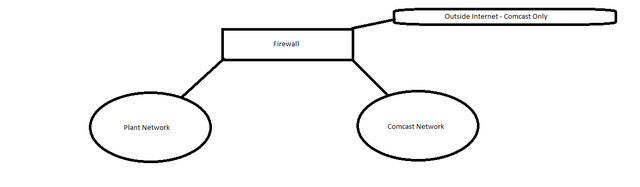
First project out of school is to install new WIFI across the plant. The WAPs need to broadcast 2 SSIDs, one for Plant (static IPs) and one for Comcast (DHCP, handled by firewall). Plant SSID currently works and has full connectivity to plant network. WAPs are currently plugged in to Plant switches.
My issue to start: Both networks are separated by Firewall, both networks are on their respective vlan 1. I moved comcast to vlan 15, configured all the switches in comcast network to access the new vlan.
2nd SSID is now being broadcasted, but DHCP for this SSID isn't working. I'm thinking it's a firewall issue. See mock network diagram below. I can post switch configs if needed
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2019 02:42 AM
As I understand currently both vlan 1 and vlan 15 are sent from the AP over the plant network to the firewall
VLAN 1 receives DHCP address from firewall. vlan 15 does not receive DHCP address.
first look at the interface of the firewall.
this needs to be sowewhat of a vlan-trunk to handle both vlan 1 and vlan15
of course the uplink from the switch (and all interswitch links in between) needs to be a vlan-trunk to pass both vlans
if the firewall is an Cisco ASA it needs to have a subinterface for vlan1 and 15 (dot1x) if other brand it needs something similar.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2019 05:05 PM
Its a checkpoint firewall. I quickly looked through the GUI and couldn't find a way to check to make sure the interface was set to trunk. When I get to work tomorrow, I'll try to GUI in to it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2019 09:33 AM
You have told us a few things about your environment but not enough for us to be able to understand the issue or to make good suggestions. Please provide clarification about these things:
- is it your intention that the new vlan 15 would use the existing DHCP scope from the firewall or would the new vlan have a new DHCP scope on the firewall?
- you tell us that you configured the switches in the Comcast side to access the new vlan. So far so good. But you do not tell us whether the switch port on the switch that connects to the firewall is an access port in the original vlan 1 or in the new vlan 15 or is a trunk port. If a trunk port is it carrying both vlan 1 and vlan 15? If a trunk port then which vlan is the native vlan?
- is the switch on the Comcast side a layer 2 switch (just does layer 2 forwarding) or is it a layer 3 switch (capable of doing layer 3 forwarding)?
- does the switch on the Comcast side have a vlan interface for vlan 1? Does the switch have a vlan interface for vlan 15?
- you do not tell us what, if anything, you changed on the firewall. Is the interface on the firewall connecting to the Comcast switch a normal Ethernet interface (processing untagged frames) or is it now a trunk port? If a trunk port then which vlan is the native vlan (untagged frames)?
Perhaps posting the config of the switch connecting to the firewall on the Comcast side with clear indication of which switch port connects to the firewall and which switch port(s) connect to WAP(s) might shed light on this.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2019 05:08 PM
- is it your intention that the new vlan 15 would use the existing DHCP scope from the firewall or would the new vlan have a new DHCP scope on the firewall?
I would like for it to be the same DHCP scope
- you tell us that you configured the switches in the Comcast side to access the new vlan. So far so good. But you do not tell us whether the switch port on the switch that connects to the firewall is an access port in the original vlan 1 or in the new vlan 15 or is a trunk port. If a trunk port is it carrying both vlan 1 and vlan 15? If a trunk port then which vlan is the native vlan?
It's set to access at the moment, but I am assuming that I would like for it to be trunked. Does changing the native vlan around make a difference?
- is the switch on the Comcast side a layer 2 switch (just does layer 2 forwarding) or is it a layer 3 switch (capable of doing layer 3 forwarding)?
It is a layer 3 switch, but is not using any forwarding, just functioning as layer 2
- does the switch on the Comcast side have a vlan interface for vlan 1? Does the switch have a vlan interface for vlan 15?
yes and yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2019 09:49 AM
Thank you for the additional information. Here are my follow up questions:
- using the same DHCP scope should not be a problem. What you need to do to accomplish that depends on the answers to some of the other questions. There are a few things that would be helpful to know: is the DHCP scope configured on the firewall or is there a separate EHCP server? Does the switch use helper address to forward DHCP requests to the server or does it work because the server and the clients are in the same vlan/same subnet?
- you tell us that the switch port connecting to the firewall is configured as an access port. Is that access port in vlan 1 or is it in vlan 15? Having the switch port as an access port is more simple. Changing it to a trunk port gives you more flexibility but also introduces more complexity into the configuration. Perhaps you need to think a bit more about this. These questions might help: What was the reason that you created vlan 15? Do you have plans to actively use both vlan 15 and vlan 1? If so what would you do in each of the vlans?
With an access port there is no native vlan. With a trunk port there is a native vlan. With a trunk some Ethernet frames are transmitted with tags and some are transmitted without tags (frames in the native vlan do not have tags). So when you configure an interface as a trunk it is important that all devices connected on that trunk agree about which vlan is the native vlan.
- it is good to know that the switch is layer 3 capable. Then the question becomes whether layer 3 processing is activated. The fact that the switch has vlan interfaces for both vlan 1 and vlan 15 suggests that layer 3 processing may be activated. The output of show ip protocol and of show ip route from the switch might shed some light on this. Also the output of show run | include rout would be helpful.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2019 12:43 PM
Going to preface your questions with my goal for this project, then come back and answer the questions.
I have a new wireless network that I would like to be able to broadcast 2 SSIDs, each SSID is tied to a different VLAN/Network.
Network 1: Plant Network - VLAN 1 - 199.8.0.0/24
Network 2: Comcast Network - VLAN 10 (sorry, in the post I stated 15, but meant 10) - 10.1.10.0/24
Both networks are on their own separate set of Switches and are separated by the Firewall.
VLAN 1 should be kept within the 199.8.0.0 network, with a few (less than 10) devices selected in firewall opened to internet. VLAN 10 should be opened to the internet, option to peer into VLAN 1.
PN-SW33 is connected to FW via a Trunk port. CC-SW07 is connected to FW via a trunk port, set native VLAN to 10.
I removed the DHCP off the firewall, moved to a PN-SW33 as a DHCP Pool serving up 10.1.10.0 IPs on VLAN 10.
I would, in theory, like to be able to plug into either a PN or CC switch and access either VLAN. depending on if I'm plugging in a desktop, I give it 10. If it's a plant device, I give it 1.
PN-SW33 - Port 12 is going to FW
PN-SW33#sh run
Building configuration...
Current configuration : 6101 bytes
!
! Last configuration change at 13:32:52 CST Mon Dec 30 2019 by admin
! NVRAM config last updated at 13:31:07 CST Mon Dec 30 2019
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname PN-SW33
!
boot-start-marker
boot-end-marker
!
!
enable secret 5 $1$BpbD$3jeMnQ7h4tq2Eh6Ncv4D4.
!
username admin privilege 15 secret 5 $1$GiOk$fZxoMrVZntOs5jQODJtTx/
no aaa new-model
clock timezone CST -6 0
clock summer-time CDT recurring
system mtu routing 1500
ip routing
no ip cef optimize neighbor resolution
!
ip dhcp excluded-address 10.1.10.1 10.1.10.8
!
ip dhcp pool VLAN10
network 10.1.10.0 255.255.255.0
default-router 10.1.10.1
cip instance 1
!
!
no ip domain-lookup
ip igmp snooping querier
vtp mode transparent
!
!
!
!
!
ptp mode e2etransparent
!
!
crypto pki trustpoint TP-self-signed-2953378432
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2953378432
revocation-check none
rsakeypair TP-self-signed-2953378432
!
!
crypto pki certificate chain TP-self-signed-2953378432
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32393533 33373834 3332301E 170D3036 30313032 30353239
31305A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 39353333
37383433 3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
81009F88 82F657D6 879B3285 773057AA E27FABCA A95743EF DA14E2E3 004F822A
CB520B87 36BF957D 120322AA 4BED65F5 E64DF74D CD13B037 B751CA81 62673B0F
EACD3780 051E4313 F8429F6F 2E07F183 9FAD46DB F8E7E3C2 22B3738A 27905501
A529FB9C 80764619 07657016 DB617AD2 92AB968B 172B099E BA5DF2DC 76E3A776
BF670203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 140BBB96 88C53BE0 F8E6A70D 73708BB6 9F2426F9 63301D06
03551D0E 04160414 0BBB9688 C53BE0F8 E6A70D73 708BB69F 2426F963 300D0609
2A864886 F70D0101 05050003 81810033 48108FF3 BB5BF0E2 CF90C69C B8D36D08
1E5AF74B 58D9593B 54827947 7E668F41 33594FD0 FEFD53C9 EEF76666 5EE1F7EB
6D22B2A2 1D75724D 910025C6 531ACDC0 72304359 061F5F7C 1334DAA6 2D8DC000
2ECA7DD2 75DCB7D0 56853FE3 2DDF07EA CA0BDDCF 1293A6EA ED2CE90B AC03FD8C
5ED735E5 1450595F 364EDC3A 5F5D44
quit
license boot level ipservices
!
spanning-tree mode rapid-pvst
spanning-tree portfast edge bpduguard default
spanning-tree extend system-id
errdisable recovery cause bpduguard
errdisable recovery interval 120
!
alarm profile defaultPort
alarm not-operating
syslog not-operating
notifies not-operating
!
!
!
!
transceiver type all
vlan internal allocation policy ascending
!
vlan 10,99
!
lldp run
!
!
!
!
!
interface GigabitEthernet1/1
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/2
description Uplinked to Port 1 PN-SW30
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/3
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/4
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/5
switchport trunk allowed vlan 1,10,99
switchport mode trunk
shutdown
!
interface GigabitEthernet1/6
switchport trunk allowed vlan 1,10,99
switchport trunk native vlan 999
switchport mode trunk
!
interface GigabitEthernet1/7
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/8
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/9
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/10
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/11
switchport access vlan 99
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/12
switchport access vlan 99
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/13
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/14
switchport trunk allowed vlan 1,10,99
switchport mode trunk
power inline port priority high
!
interface GigabitEthernet1/15
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/16
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/17
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/18
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/19
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/20
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/21
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/22
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/23
switchport trunk allowed vlan 1
switchport mode trunk
!
interface GigabitEthernet1/24
switchport access vlan 99
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/25
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/26
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/27
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface GigabitEthernet1/28
switchport trunk allowed vlan 1,10,99
switchport mode trunk
!
interface Vlan1
ip address 199.8.0.1 255.255.0.0
no ip redirects
!
interface Vlan10
ip address 10.1.10.5 255.255.255.0
!
interface Vlan99
ip address 10.1.99.1 255.255.255.0
!
ip forward-protocol nd
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 199.8.0.2
!
!
!
snmp-server community 1lr3ad RO
!
!
line con 0
logging synchronous
login local
line vty 0 4
logging synchronous
login local
transport input ssh
line vty 5 15
logging synchronous
login local
transport input ssh
!
ntp server 10.1.99.97
mac address-table notification mac-move
!
end
PN-SW33#CC-SW07 - Gi1/12 is to the fire wall
CC-SW07#sh run
Building configuration...
Current configuration : 5893 bytes
!
! Last configuration change at 07:43:25 CST Mon Dec 30 2019 by admin
!
version 15.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname CC-SW07
!
boot-start-marker
boot-end-marker
!
!
enable secret 5 $1$iUQT$gogQeiIrkUffRsdA/WpEO/
!
username admin privilege 15 secret 5 $1$ndIX$8w/KIIdyClsNfpPKZekSQ.
no aaa new-model
clock timezone CST -6 0
clock summer-time CDT recurring
system mtu routing 1500
!
!
!
no ip domain-lookup
vtp mode transparent
!
!
!
!
!
ptp mode e2etransparent
!
!
crypto pki trustpoint TP-self-signed-2953378688
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2953378688
revocation-check none
rsakeypair TP-self-signed-2953378688
!
!
crypto pki certificate chain TP-self-signed-2953378688
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32393533 33373836 3838301E 170D3036 30313032 30303038
35365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 39353333
37383638 3830819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100BABA 3654211B F848485E A7CFAB14 284F5448 81FC28E6 5A30BFA1 41AA2034
263AE2A2 AD5C26BA FF24BB98 C2E257DF B170DFAB EBE1839C 5A6DD6EF 79949F9A
68C892B2 0C53B0A3 C7BBD199 13041043 BE5F1F59 1665E603 28E02D3E FF3F295F
052D6643 66FF632F 4C2D5A66 1FE65250 1DC80962 891E1410 0480CE2D 6FFC35CE
1B390203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 1441FB47 35961A33 E847AD33 084EB1E9 BB62DA22 26301D06
03551D0E 04160414 41FB4735 961A33E8 47AD3308 4EB1E9BB 62DA2226 300D0609
2A864886 F70D0101 05050003 81810000 88185F9A CBDCC452 A5253C39 678DB3CF
E24E61FC 812B5DD9 7A4CF225 AA443CC2 9F57B324 45542266 08430EFE 67F39C86
38304D11 3E69668E 48D3BCB6 98E71C0E B77276C9 860DA530 B89B9D69 9588A863
174468A2 AF49D319 A7456FD9 92F5B2A1 BD8073A0 973BC883 042BC267 AF915AB7
BA752D87 F46B50FC 16DC9B54 AF0625
quit
license boot level lanbase
!
spanning-tree mode rapid-pvst
spanning-tree portfast edge bpduguard default
spanning-tree extend system-id
errdisable recovery cause bpduguard
errdisable recovery interval 120
!
alarm profile defaultPort
alarm not-operating
syslog not-operating
notifies not-operating
!
!
!
!
transceiver type all
vlan internal allocation policy ascending
!
vlan 10,99
!
lldp run
!
!
!
!
!
interface GigabitEthernet1/1
switchport mode trunk
!
interface GigabitEthernet1/2
switchport mode trunk
!
interface GigabitEthernet1/3
switchport mode trunk
!
interface GigabitEthernet1/4
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/5
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/6
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/7
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/8
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/9
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/10
switchport mode trunk
spanning-tree portfast edge
!
interface GigabitEthernet1/11
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/12
switchport access vlan 10
switchport trunk allowed vlan 1,10,99
switchport trunk native vlan 10
switchport mode trunk
spanning-tree portfast edge
!
interface GigabitEthernet1/13
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/14
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/15
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/16
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/17
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/18
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/19
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/20
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/21
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/22
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/23
switchport access vlan 10
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/24
switchport access vlan 99
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/25
switchport mode trunk
!
interface GigabitEthernet1/26
switchport mode trunk
!
interface GigabitEthernet1/27
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/28
switchport access vlan 10
switchport mode access
!
interface Vlan1
ip address 199.8.210.40 255.255.0.0
!
interface Vlan10
ip address 10.1.10.251 255.255.255.0
!
interface Vlan99
ip address 10.1.99.144 255.255.255.0
!
ip default-gateway 10.1.99.1
ip forward-protocol nd
ip http server
ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 10.1.10.1
!
!
!
snmp-server community 1lr3ad RO
!
!
line con 0
logging synchronous
login local
line vty 0 4
logging synchronous
login local
transport input ssh
line vty 5 15
logging synchronous
login local
transport input ssh
!
!
end
CC-SW07#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2019 03:08 PM
Thank you for the update and for the configs. It is helpful to have information about the context and your explanation helps provide that. There are a couple of points that I am not clear about. You describe a new wireless network that will broadcast 2 SSIDs. That typically uses WAPs and the placement (and connectivity of the WAPs) is important to their functionality. But we have no information so far about your WAPs. And if the WAP manages 2 SSIDs (with each SSID in a separate network) then I would expect the WAP to have connectivity to both networks. But you tell us that "Both networks are on their own separate set of Switches and are separated by the Firewall." If both networks are separated by firewall then how does the WAP communicate on both networks?
There is another high level item that is not clear to me. When you indicated that the networks were separated by the firewall I assumed that the firewall would be routing between the networks and would be controlling access from one network to the other. But in looking at SW33 I see that it does have ip routing enabled, that it has trunks that carry both vlan 1 and vlan 10 (and vlan 99, which we do not know anything about), and that it has vlan interfaces for vlan 1 and vlan 10. So any traffic passing through this switch will be routed between the vlans and would not necessarily be controlled by the firewall.
Here are some observations about what I see in the configs you posted:
- PN-SW33 connects to the firewall on port 12 which has this configuration
interface GigabitEthernet1/12 switchport access vlan 99 switchport mode access spanning-tree portfast edge
I do not understand how this switch will communicate for vlan 1 to the firewall if the connection to the firewall is in vlan 99.
- Related to this is the point that the default route for this switch is 199.8.0.1. How will this switch get to its default gateway if the connection from the switch to the firewall is in vlan 99?
-PN-SW33 has the DHCP scope for the CC network. So any client requesting an IP address in the CC network must access the PN switch. So that pretty much bypasses the firewall which really means that the networks are not separated by the firewall. Which means that the CC network can function without the firewall except for access to the Internet.
- The DHCP scope for 10.1.10.0 defines the default gateway as 10.1.10.1. That address is not either of the switches for which you provide configs. Would that address be the firewall address in vlan 10?
- The DHCP scope fo 10.1.10.0 excludes addresses 10.1.10.1 and 10.1.10.8. What are these addresses? The excluded addresses should include the 2 switch vlan interfaces in that subnet which are 10.1.10.5 and 10.1.10.251.
- PN-SW33 Gig1/6 specifies
switchport trunk native vlan 999
which is probably a typo.
- PN-SW33 interface vlan 1 specified this
ip address 199.8.0.1 255.255.0.0
which is a /16 and not the /24 that your description indicated.
- CC-SW07 connection to the firewall is on 1/12 which is configured as a trunk and is configured to have its native vlan as 10. The result of this is that Ethernet frames in vlan 10 are transmitted without tagging while frames in other vlans will be tagged. We do not know how the firewall is configured. If it is configured as a trunk is it configured to have its native vlan as 10? If the firewall interface is configured as a access port it will process frames from vlan 10 but not from other vlans. If the firewall is configured as a trunk with default vlan for untagged frames it will process vlan 10 frames but associate them with some other subnet.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2019 08:11 PM
WAP communicate on both networks
At the moment, the WAPs are plugged into VLAN 1/Plant network (but are trunked) and broadcasting the SSID fine. We want to be able to broadcast a 2nd SSID, while plugged into these trunk ports to broadcast VLAN 10/Comcast network.
We are hoping to keep the architecture the same, but the more I work on this, the more it seems like I will have to remove the firewall and add routes to the switches to direct traffic between the 2 networks(?). We have a WLC (3504 cisco) that is sitting on PN-SW33 and assigned a management IP of 10.1.99.2 on VLAN 99.
But in looking at SW33 I see that it does have ip routing enabled, that it has trunks that carry both vlan 1 and vlan 10
Correct, before I came on board, the engineer before me set up a small /30 network sitting between PN-SW33 and the FW (10.255.10.0/30). So the route on the switch was 0.0.0.0 0.0.0.0 10.255.10.2 and the firewall and a route going to 10.255.10.1.
PN-SW33 connects to the firewall on port 12 which has this configuration
Apologies, PN-SW33 connects to firewall on port 10. Been running around in circles on this problem and keep switching out which port is which.
-PN-SW33 has the DHCP scope for the CC network. So any client requesting an IP address in the CC network must access the PN switch. So that pretty much bypasses the firewall which really means that the networks are not separated by the firewall. Which means that the CC network can function without the firewall except for access to the Internet.
This pool was to remove the DHCP scope from the FW, as my WAPs were sending out DHCP requests, but not getting a response. A cisco rep is under the assumption that the DHCP return message is being sent back on VLAN 1, so my device isn't getting an IP. I assure you, the only way the networks meet is at the FW.
The DHCP scope for 10.1.10.0 defines the default gateway as 10.1.10.1. That address is not either of the switches for which you provide configs. Would that address be the firewall address in vlan 10?
This is indeed the IP for the Comcast Interface on the FW.
The DHCP scope fo 10.1.10.0 excludes addresses 10.1.10.1 and 10.1.10.8. What are these addresses? The excluded addresses should include the 2 switch vlan interfaces in that subnet which are 10.1.10.5 and 10.1.10.251
Was under the assumption that this command excluded a range. All of the Comcast Switch have a static IP assigned on VLAN 10, but I believe the DHCP scope on the FW would drop those IPs from the pool.
PN-SW33 Gig1/6 specifies
This interface connects to the WLC. When first setting up the network, WAPs weren't joining the network and getting their configs. This dummy native VLAN allowed for it to work. I'm sorry, can't remember the direct explanation for it.
PN-SW33 interface vlan 1 specified this which is a /16 and not the /24 that your description indicated.
It is a typo on my part. 199.8.0.0/16 and 10.1.10.0/24
Last note to probably cover your final post: It seems as if my firewall (CheckPoint 1430) has no way of assigning VLANs to its interface. I appreciate these questions into all of this, definitely helps me piece things together. It is looking like I have 3 possible solution
1. Find a new firewall that can handle VLAN (i.e. Cisco ASA)
2. Directly connect the switches for Plant and Comcast together. Have a single connection going into the FW. Might have to set up routing on the switches (?)
3. Drop VLAN 10 from the plant side. Try to find out how I can assign a device plugged into the Plant Network a 10.1.10.0/24 IP, and talk with the outside world as well as comcast side devices. I'm not sure if this is possible(?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2019 06:37 AM
Your original post had a diagram that showed a simple network with two networks that were separate and connected by a firewall. As we have learned more about your environment and the changes being made we see things that mean that this is no longer the appropriate design, at least from a physical perspective.
- if the WAP is to broadcast 2 SSIDs and support different subnets for each SSID then both subnets must be operational on the plant switches.
- if some PCs in the plant need to get IP addresses in 10.1.10.0 and to communicate with devices in the Comcast network then vlan 10 must be active and operational on the plant switches.
If you do want to implement a structure that does maintain two logically separate networks you could accomplish that by removing from the plant switch interface vlan 1 and interface vlan 10. That would mean that routing between those networks would then be done on the firewall. Note that this will result in the firewall also needing to route between those vlans and vlan 99. This would mean that the DHCP scope would have to go back to the firewall. You have told us that there were problems when the DHCP scope was on the firewall and I am not clear how you would resolve that.
I have worked some with Checkpoint firewalls but do not claim expertise with that platform and can not address whether it can assign vlans to interfaces (when you mention assigning vlans to interfaces I assume that you are talking about making the firewall interfaces into trunks). I would think this should be possible but if it is problematic then the solution could be to connect on the plant switch to the firewall an access port in vlan 1, an access port in vlan 10, and an access port in vlan 99 and on the Comcast switch connect an access port in vlan 10 and an access port in vlan 99.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2019 08:16 AM
but if it is problematic then the solution could be to connect on the plant switch to the firewall an access port in vlan 1, an access port in vlan 10, and an access port in vlan 99 and on the Comcast switch connect an access port in vlan 10 and an access port in vlan 99.
This makes sense. Yea documentation says it can't do trunk ports. Appreciate the help and I'll update once I set this up after the new year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2019 10:12 AM
If the documentation says it can not do trunk ports then you certainly need a solution that does not use trunks. My suggestion uses more firewall interfaces, but it does achieve the desired result without using trunks.
I do not know your environment as well as you do. But it seems to me that identifying the switches as "plant" switch or "comcast" switch is not accurate and that it might be helpful to think about them in somewhat different terms. If some PCs in the plant will be in vlan 10 and have IP addresses in 10.1.10.0 then the plant switch is not just for "plant" since it is active in all 3 vlans. And the Comcast switch looks like it will be active in both vlan 10 and vlan 99. So that switch is more than just Comcast. Perhaps it might be helpful to think of some other way to identify the switches (maybe distribution and access).
It also seems to me that the network as depicted in the drawing with the two switches separated from each other and connected by the firewall will not work as drawn. If some PCs in the plant will have addresses in 10.1.10.0 and need to communicate with other devices in the Comcast side then the PCs will arp for the destination address. If the path from one switch to the other switch is through the firewall then I believe that the arp will fail and the PCs will not be able to communicate. For the PCs in the plant to communicate with devices in Comcast there needs to be a physical connection between the switches. So from the perspective of layer 1 and layer 2 you will have switches communicating with each other and with the firewall.
If you agree that the switches will need to be connected to each other then you may want to think about whether the Comcast side switch needs to have its own connection to the firewall or whether its connection through the distribution switch is sufficient.
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide