- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: RV130 VPN Server + iOS / macOS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV130 VPN Server + iOS / macOS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 03:28 AM
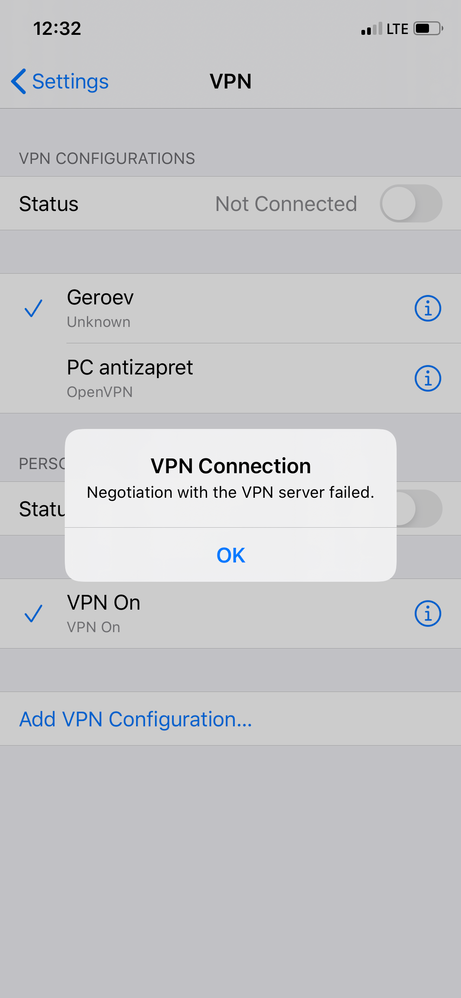
Hello. I’m try to connect through IPsec RV130 VPN Server via iPhone iOS 13.
I have some trouble (see attached)
What mistakes do I make?
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 03:35 AM
- Enable all logging categories on the RV130 (at least in the initial analysis phaze of the problem) and preferably use a syslog server. Then when you connect with the iPhone examine the logs and check for error messages concerning VPN connections :
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2020 08:29 AM
Thanks for advice. This logs. Can you see it? Tnx.
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [RFC 3947] meth=109, but port floating is off
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike] meth=110, but port floating is off
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring unknown Vendor ID payload [8f8d83826d246b6fc7a8a6a428c11de8]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring unknown Vendor ID payload [439b59f8ba676c4c7737ae22eab8f582]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring unknown Vendor ID payload [4d1e0e136deafa34c4f3ea9f02ec7285]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring unknown Vendor ID payload [80d0bb3def54565ee84645d4c85ce3ee]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring unknown Vendor ID payload [9909b64eed937c6573de52ace952fa6b]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but port floating is off
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but port floating is off
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but port floating is off
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [XAUTH]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [Cisco-Unity]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: ignoring Vendor ID payload [FRAGMENTATION 80000000]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received Vendor ID payload [Dead Peer Detection]
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: responding to Main Mode from unknown peer 188.170.81.168
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: STATE_MAIN_R1: sent MR1, expecting MI2
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: STATE_MAIN_R2: sent MR2, expecting MI3
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: ignoring informational payload, type IPSEC_INITIAL_CONTACT msgid=00000000
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: Main mode peer ID is ID_IPV4_ADDR: '100.65.41.198'
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[1] 188.170.81.168 #15: switched from "shrew" to "shrew"
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: deleting connection "shrew" instance with peer 188.170.81.168 {isakmp=#0/ipsec=#0}
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: transition from state STATE_MAIN_R2 to state STATE_MAIN_R3
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY cipher=aes_256 prf=OAKLEY_SHA2_256 group=modp2048}
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: Dead Peer Detection (RFC 3706): enabled
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: Sending XAUTH Login/Password Request
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: Sending Username/Password request (XAUTH_R0)
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: User roman: Attempting to login
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: md5 authentication being called to authenticate user roman
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: password file (/etc/ipsec.d/passwd) open.
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: checking user(roman:shrew)
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: User roman: Authentication Successful
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: XAUTH: xauth_inR1(STF_OK)
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: transition from state STATE_XAUTH_R1 to state STATE_MAIN_R3
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: STATE_MAIN_R3: sent MR3, ISAKMP SA established
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: Dead Peer Detection (RFC 3706): enabled
2020-01-14 19:17:58 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:02 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:05 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:08 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:11 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:14 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:17 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:18 RV130 local2.debug pppd[2702]: rcvd [LCP pid=(2702) EchoReq id=0x7f magic=0x28f7c94f]
2020-01-14 19:18:18 RV130 local2.debug pppd[2702]: sent [LCP pid=(2702) EchoRep id=0x7f magic=0xddcfd93d]
2020-01-14 19:18:20 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:23 RV130 local2.debug pppd[2702]: sent [LCP pid=(2702) EchoReq id=0x4f magic=0xddcfd93d]
2020-01-14 19:18:23 RV130 local2.debug pppd[2702]: rcvd [LCP pid=(2702) EchoRep id=0x4f magic=0x28f7c94f]
2020-01-14 19:18:23 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:27 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received MODECFG message when in state STATE_MAIN_R3, and we aren't xauth client
2020-01-14 19:18:28 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168 #15: received Delete SA payload: deleting ISAKMP State #15
2020-01-14 19:18:28 RV130 authpriv.warning pluto[28270]: "shrew"[2] 188.170.81.168: deleting connection "shrew" instance with peer 188.170.81.168 {isakmp=#0/ipsec=#0}
2020-01-14 19:18:28 RV130 authpriv.warning pluto[28270]: packet from 188.170.81.168:64506: received and ignored informational message
2020-01-14 19:18:28 RV130 authpriv.warning pluto[28270]: ERROR: asynchronous network error report on ppp0 (sport=500) for message to 188.170.81.168 port 64506, complainant 188.170.81.168: Connection refused [errno 111, origin ICMP type 3 code 3 (not auth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 12:56 AM
- Difficult to tell, advising to re-post in group VPN and Anyconnect , include the logs in the initial body of the post too. More experts may be available in this group.
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide