- Cisco Community
- Technology and Support
- Security
- Network Security
- ACLs for NTP and DNS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACLs for NTP and DNS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2021 06:35 AM - edited 07-25-2021 06:36 AM
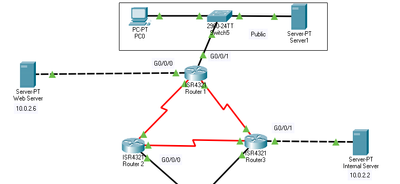
I have an Internal Server connected to Router 3 that is using the Windows Time Service which acts as the NTP Server for the 3 Routers. I have configured it to obtain the NTP pool from the public network, specifically 0.sg.pool.ntp.org from the NTP Pool Project. This internal server uses the Web Server(10.0.2.6)'s DNS Service.
On the Web Server connected to Router 1, I have a Webpage alongside DNS configured. This Web Server is in the DMZ that I will establish with ACLs.
I have an extended ACL configured on Router 1's G0/0/1's ingress interface. This ACL basically permits the public to access the Web Server and permits all established TCP traffic.
- access-list 100 permit tcp any host 200.0.0.2 eq 443 (SNAT is configured for Web Server)
- access-list 100 permit tcp any any established
After configuring this ACL, my internal Server is unable to obtain the NTP pool from 0.sg.pool.ntp.org. I assumed that this is because NTP uses a different port which is denied by my ACL. I then tried to permit NTP with the following command:
- access-list 100 permit udp any host 10.0.2.2 eq 123
This still did not work. At this point, I am wondering if it is because the ACL I implemented on R1 G0/0/1 Ingress is blocking something else. I am thinking that it has something to do with the ACL blocking DNS but I am not sure. Any help?
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2021 11:33 AM
Is this a lab setup in or are you just simulating the issue in packet tracer?
Are you NATing traffic from the 10.0.2.2 server so it reaches the internet?
Since it is 10.0.2.2 which is initiating the NTP traffic here, the access list on Gig0/0/1 should reflect that the reply is coming with a source port of udp/123 and a destination port of any high random port. Change your ACL to the following and test.
access-list 100 permit udp any eq 123 host 10.0.2.2
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


