- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Add new tunnel to ASA that has an existing ipsec vpn.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 04:15 AM
Hello,
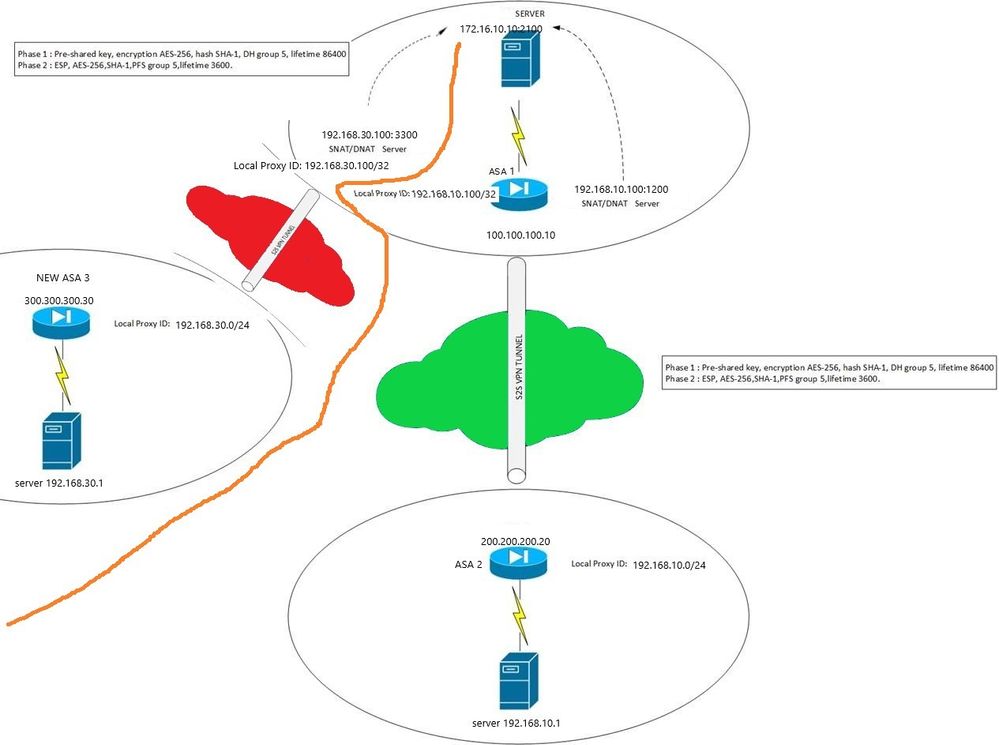
I have the following case: ASA1 has a tunnel made and NAT to another ASA2.
I must add another ASA3 to ASA1, which must be tunneled and access the same resource from ASA1.
Warnings: there should be no connection between ASA2 and ASA3 networks.
How can I do that.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 04:23 AM
@m.petrov1 you will need to modify the crypto ACL of each of the ASAs to include the remote networks. On ASA1 you will need a NAT exemption rule to ensure traffic between the ASA2 and ASA3 networks are not unintentially translated. On ASA1 you will also need to add the command same-security-traffic permit intra-interface to allow traffic to enter and exit the same interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 04:23 AM
@m.petrov1 you will need to modify the crypto ACL of each of the ASAs to include the remote networks. On ASA1 you will need a NAT exemption rule to ensure traffic between the ASA2 and ASA3 networks are not unintentially translated. On ASA1 you will also need to add the command same-security-traffic permit intra-interface to allow traffic to enter and exit the same interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2022 04:42 AM
Thanks, I will test and share the result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2022 03:37 AM
Hi, to add a new tunnel to ASA1, I need to use another physical interface of ASA1 or I can use the subinterface? Here's how the configuration is done now:
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 100.100.100.10 255.255.255.0
!
interface GigabitEthernet1/3
nameif inside2
security-level 100
no ip address
!
interface GigabitEthernet1/3.1
vlan 70
nameif inside3
security-level 100
ip address 192.168.10.100 255.255.255.0
!
same-security-traffic permit intra-interface
!
object network obj_any
subnet 0.0.0.0 0.0.0.0
!
object network 192.168.10.100_32
host 192.168.10.100
!
object network 192.168.10.0_25
subnet 192.168.10.0 255.255.255.0
!
object network SERVER
host 172.16.10.10
!
object-group service SERVER-proxy tcp
port-object eq 2100
!
access-list 100 extended permit ip object 192.168.10.100_32 object 192.168.10.0_25
access-list outside_access_in extended permit ip object 192.168.10.0_25 object SERVER
access-list outside_access_in extended permit ip object 192.168.10.0_25 object 192.168.10.100_32
!
object network obj_any
nat (any,outside) dynamic interface
!
object network SERVER
nat (inside3,outside) static 192.168.10.100_32 service tcp 2100 1200
access-group outside_access_in in interface outside
!
route outside 0.0.0.0 0.0.0.0 100.100.100.10 1
route outside 192.168.10.0 255.255.255.128 200.200.200.20 1
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2022 04:39 AM - edited 01-24-2022 04:41 AM
@m.petrov1 either a physical or sub-interface will work. You will need to define a NAT exemption rule to ensure that new network traffic is not unintentially translated over the VPN tunnel and you will need to amend the crypto ACL to define the new network, to ensure the traffic is encrypted. You will also need to amend the peer VPn configuration to include the new network in it's crypto ACL.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide