- Cisco Community
- Technology and Support
- Security
- Network Security
- AMP/IPS Rule on FTD 1120 using FDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2020 02:52 PM
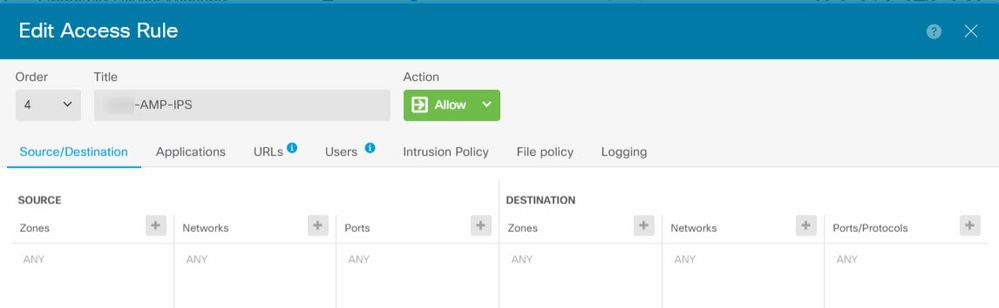
I attempted to create an access control rule for IPS and AMP from information I found online, and apparently it was completely wrong, because it had the effect of ignoring all block rules and opening up my whole network to the Internet. No matter what position I put the AMP/IPS rule in, ports like RDP were open on my Internet-facing servers, so obviously I did it wrong. I've deleted the rule for now and things seem secure again, but I wanted to ask for help before making another attempt. Here's a screenshot of the rule I created:
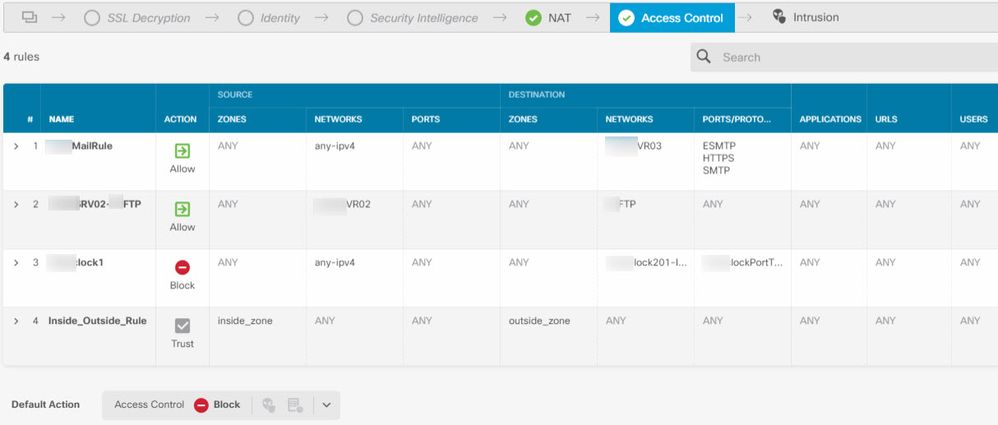
It's basically open; the only changes I made were to the Intrusion Policy tab, which I set to Connectivity over Security, and File, which I set to Cloud Lookup. I thought that my Default Action rule (set to Block) at the bottom of the list would successfully block any outside access I hadn't specifically allowed (like SMTP), but that didn't happen. It seems this rule just overrode all blocks and opened everything. I was able to block RDP by putting a rule above this one, but that wasn't a long term solution so I just got rid of this rule altogether. Can someone help me format a rule properly to turn on IPS and AMP without opening up the network? Here's a shot of the current ACL:
Thanks in advance for any help!
Chris
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2020 11:00 PM
In your example, the AMP and IPS settings should be part of each allow rule under the File Policy and Intrusion Policy tabs of the existing access control rules 1-4.
It should not be it's own separate rule. The example of that which you gave will, as you observed, allow any traffic (as long as it doesn't trigger any IPS or file policy rules).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2020 11:00 PM
In your example, the AMP and IPS settings should be part of each allow rule under the File Policy and Intrusion Policy tabs of the existing access control rules 1-4.
It should not be it's own separate rule. The example of that which you gave will, as you observed, allow any traffic (as long as it doesn't trigger any IPS or file policy rules).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 05:26 AM
Thanks Marvin, that makes sense. Doing it that way I could choose different levels of IPS for each of the rules? So on the SMTP rule I could choose Balanced, and on that currently blocked rule I could set it to Security over connectivity?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 07:12 AM
Yes you can choose different levels of IPS and File policies per rule.
Sometimes you don't need them at all - for instance a block rule only blocks so why tell it to inspect or check for file hashes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2020 02:32 PM
While that IPS rule was created I did see it reject some PHP attacks on the blocked port, so I turned that rule off temporarily, but eventually I want to turn it back on. It's just for one specific job so when I re-enable it I'll do it with the highest IPS policy I can get away with. I'll take a lighter touch with the mail rule to make sure it doesn't break anything.
Thanks for all the info. I probably should have known this, but I'm new to the FTD firewalls and IPS in general and had it in my head that it should be its own separate ruleset. Appreciate your help!
Chris
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide