- Cisco Community
- Technology and Support
- Security
- Network Security
- AnyConnect DTLS TLS 4125 5585
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect DTLS TLS 4125 5585
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 06:45 PM
AnyConnect remote to multiple location headend vpn, when different location users reach to multiple DC servers got application errors randomly, especially after application up long time with large search on users pc, hard to capture the error no matter from remote users or DC servers end, only see disconnection log from Splunk. Once change to TLS only, no more issue, but speed slower than DTLS/TLS both. and found FPR 4125 worse than ASA 5585, DPD changed from default 30 seconds into 10 seconds looks not help much. Question: when DTLS tunnel detect fail and automatically transfer to TLS tunnel, can cause this kind of disconnections? Cisco tech with us did a lot of captures, looks never successful. Need brain storm to troubleshoot, please share your idea. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 06:58 PM
Are your systems in China? If so, it might be related to inspection-related restrictions/enforcement being applied on the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2021 07:31 AM
in Canada
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 07:04 PM
The answer to your question of if the transition from DTLS to TLS can cause disconnections, yes it can. According to (https://community.cisco.com/t5/vpn/anyconnect-client-reconnects-after-1-minute/td-p/2217458), you should be able to adjust the MTU value 1300 so if DTLS fails, the renegotiation to TLS is not noticed
group-policy ac_users_group attributes webvpn anyconnect mtu 1300
Have you tried debugging on the ASA to see if any logs appear during the failure?
debug webvpn anyconnect 255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 07:36 PM
DTLS is use UDP
TLS is use TCP
this explain the slowness.
since the DTLS is used UDP and since UDP don't have any message to terminate the session, then
ASA use idea timer for UDP to terminate the session,
I think this is issue here
just make UDP idea timer long enough and check your connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2021 11:07 AM - edited 01-31-2021 05:37 PM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 04:50 PM
tried below all, looks didn't help
webvpn
anyconnect ssl dtls enable
anyconnect ssl keepalive 60
anyconnect dpd-interval client 5
anyconnect mtu 1300
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 05:59 PM
Show vpn session dB
can I see output of this when vpn is disconnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 10:55 AM
vcst-d09a-asvp-fw5/pri/act# sh vpn-sessiondb de
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
AnyConnect Client : 1024 : 86956 : 1253 : 2
SSL/TLS/DTLS : 1024 : 86956 : 1253 : 2
Clientless VPN : 0 : 7 : 2
Browser : 0 : 7 : 2
---------------------------------------------------------------------------
Total Active and Inactive : 1026 Total Cumulative : 86963
Device Total VPN Capacity : 20000
Device Load : 5%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
Clientless : 0 : 7 : 2
AnyConnect-Parent : 1026 : 86956 : 1253
SSL-Tunnel : 1018 : 415096 : 1243
DTLS-Tunnel : 30 : 26090 : 916
---------------------------------------------------------------------------
Totals : 2074 : 528149
---------------------------------------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2021 05:57 PM - edited 02-05-2021 04:23 PM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 05:43 AM - edited 02-05-2021 04:23 PM
...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2021 05:58 PM
Did you do any debugs and was there any good information in that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2021 11:20 AM
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-MTU: 1399'
Processing CSTP header line: 'X-CSTP-MTU: 1399'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Address-Type: IPv6,IPv4'
Processing CSTP header line: 'X-CSTP-Address-Type: IPv6,IPv4'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Local-Address-IP4: 192.168.0.24'
Processing CSTP header line: 'X-CSTP-Local-Address-IP4: 192.168.0.24'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Base-MTU: 1500'
Processing CSTP header line: 'X-CSTP-Base-MTU: 1500'
webvpn_cstp_parse_request_field()
....
Iphdr=20 base-mtu=1500 def-mtu=1500 conf-mtu=1406
tcp-mss = 1460
path-mtu = 1460(mss)
TLS Block size = 16, version = 0x303
mtu = 1460(path-mtu) - 0(opts) - 5(ssl) - 16(iv) = 1439
mod-mtu = 1439(mtu) & 0xfff0(complement) = 1424
tls-mtu = 1424(mod-mtu) - 8(cstp) - 48(mac) - 1(pad) = 1367
computed tls-mtu=1367 dtls-mtu=0 conf-mtu=1406
tls-mtu=1367 dtls-mtu=0
Legacy mode so default dtls mtu to tls mtu
....
from client netsh ipv4 show interface MTU: 1300
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 04:35 PM
So as I mention before some topic is very interest and it is not about the NAT and other regular issue that can easily solve but like this issue is very interest.
So Friend,
Why DTLS fallback into TLS ?
if you specify other port than 443 then some FW in path can be block these port and hence make any connect fallback to TLS connection.
Note:- need DPD for fallback
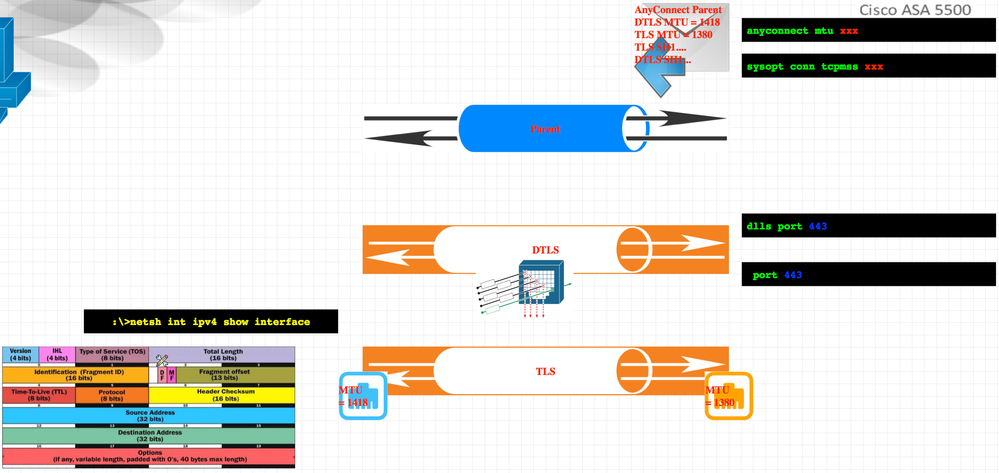
Why issue with the MTU?
the any connect build two-tunnel
one tunnel is parent which use to exchange the cipher auth between client and ASA
second TLS Or DTLS "depend"
during the parent tunnel there are two value send to client
1-DTLS MTU
2-TLS MTU
client will use DTLS MTU value
do netsh ipv4 show interface
DTLS MTU value for default large than TLS MTU
ASA use TLS MTU value
NOW
client will use DTLS MTU in TCP MSS and send this value to server behind the ASA
server send packet with value equal to DTLS MTU with "DF bit set"
ASA see this value BUT because it use TLS MTU which is lower than DTLS MTU and DF bit set it cannot frag and the packet drop!!!
even if it not drop this need from the ASA frag each packet from Server go toward client and this so slow.
what we check here is :-
check the MTU client used is it
DTLS MTU or TLS MTU ..
waiting your reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2021 12:27 PM
sh run all sysopt:
no sysopt traffic detailed-statistics
no sysopt connection timewait
sysopt connection tcpmss 1380
sysopt connection tcpmss minimum 0
sysopt connection permit-vpn
debug webvpn anyconnect 255:
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-MTU: 1399'
Processing CSTP header line: 'X-CSTP-MTU: 1399'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Address-Type: IPv6,IPv4'
Processing CSTP header line: 'X-CSTP-Address-Type: IPv6,IPv4'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Local-Address-IP4: 192.168.0.24'
Processing CSTP header line: 'X-CSTP-Local-Address-IP4: 192.168.0.24'
webvpn_cstp_parse_request_field()
...input: 'X-CSTP-Base-MTU: 1500'
Processing CSTP header line: 'X-CSTP-Base-MTU: 1500'
webvpn_cstp_parse_request_field()
....
tcp-mss = 1460
path-mtu = 1460(mss)
TLS Block size = 16, version = 0x303
mtu = 1460(path-mtu) - 0(opts) - 5(ssl) - 16(iv) = 1439
mod-mtu = 1439(mtu) & 0xfff0(complement) = 1424
tls-mtu = 1424(mod-mtu) - 8(cstp) - 48(mac) - 1(pad) = 1367
DTLS Block size = 16
mtu = 1500(base-mtu) - 20(ip) - 8(udp) - 13(dtlshdr) - 16(dtlsiv) = 1443
mod-mtu = 1443(mtu) & 0xfff0(complement) = 1440
dtls-mtu = 1440(mod-mtu) - 1(cdtp) - 20(mac) - 1(pad) = 1418
computed tls-mtu=1367 dtls-mtu=1418 conf-mtu=1300
overide computed tls-mtu=1367 with conf-mtu=1300
DTLS enabled for intf=3 (outside)
overide computed dtls-mtu=1418 with conf-mtu=1300
tls-mtu=1300 dtls-mtu=1300
....
from client netsh ipv4 show interface MTU: 1300
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide