- Cisco Community
- Technology and Support
- Security
- Network Security
- AnyConnect hairpin to public ip address
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect hairpin to public ip address
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 03:17 AM
We have an ASA 5515-X running 9.2(4) firmware with AnyConnect users and site-to-site vpns configured. All works fine (including hairpinning to the site-to-site connections), but I have been asked to change the config so that AnyC users can access a server on the internet, via the public ip of the ASA. I googled answers and have tried many of the solutions suggested, but still can't get it to work.
Steps taken:
Added the server to the split for the AnyC users.
Created an object for the AnyC address pool.
Created an object-group which includes the ip address of the server in question.
Then I have tried a variety of "nat (outside,outside)" entries (as found in various google searches), but none have worked.
Can anybody help please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 03:27 AM
@Phil Smith you will need the command same-security-traffic permit intra-interface to permit the traffic to hairpin.
And an object like this
object network RAVPN_USERS
subnet 10.4.4.0 255.255.255.0
nat (outside,outside) dynamic interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 03:52 AM
did that, still no go
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 04:55 AM
Can you attempt a packet trace from an AnyConnect client IP --> destined server and share results so the community can better assist with troubleshooting? Note that this may shed some light that may further assist you with troubleshooting the issue. In ASDM->Tools->Pakcet Tracer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 05:30 AM
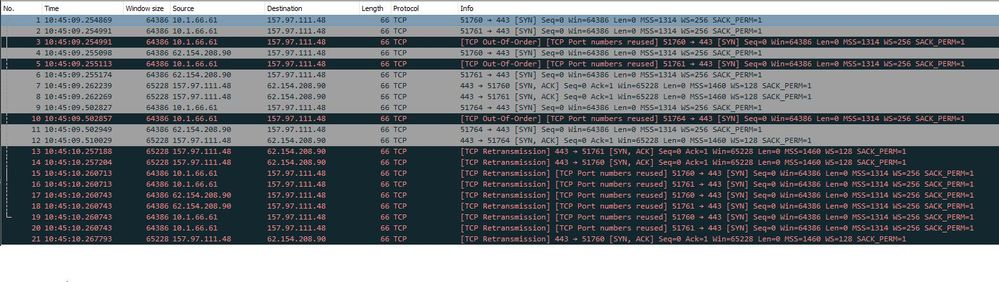
Best I can do - saves as a pcap file. This is the merged ingress and egress files.
It looks like AnyC client (10.1.66.1) can send out to server (157.97.111.48), and server tries to reply (to the public ip), but it doesn't get through the ASA back to the client, so both sides just retransmit (I think?)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide