- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5506 Port Forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 03:55 PM - edited 03-12-2019 01:46 AM
Hello,
I have a 5506-x that needs to port forward a range of ports. My outside IP is also Dynamic from the ISP.
So far I made a Network\Service Object for the ports I want to use in the port forwarding.
object service Service_OBJ_IPcamPorts_UDP
service udp source range 8186 8191 destination range 8186 8191
object service Service_OBJ_IPcamPort_TCP
service tcp source range 8186 8191 destination range 8186 8191
object network Network-Object-SOHO-Cisco-Router
host 10.0.0.2
After the creation of the objects I'm unsure how to nat and make the acl to allow the packets.
nat (CISCO-SOHO-Router,outside) source static Network-Object-SOHO-Cisco-Router Network-Object-SOHO-Cisco-Router service Service_OBJ_IPcamPort_TCP Service_OBJ_IPcamPort_TCP
Then my Current ACL
access-list outside_access_in line 2 extended permit tcp any range 8186 8191 host 10.0.0.2 range 8186 8191 log disable (hitcnt=0) 0x95da1b49
access-list outside_access_in line 2 extended permit udp any range 8186 8191 host 10.0.0.2 range 8186 8191 log disable (hitcnt=0) 0x401fe7ac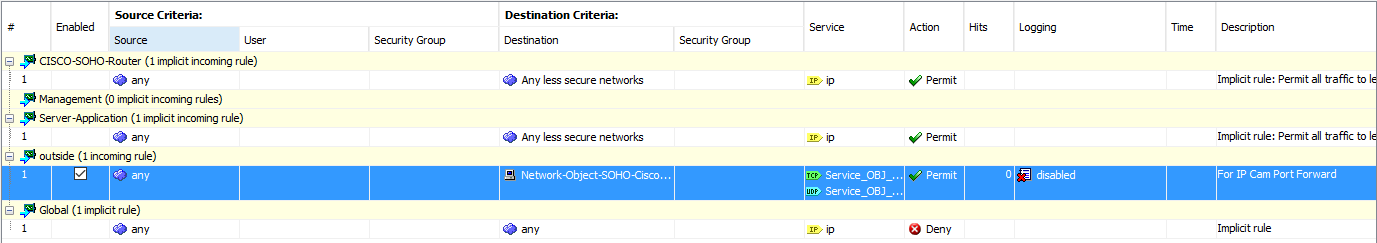
any is the internet
10.0.0.2 is a SOHO home router that is nating again with the same port ranges
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2017 12:29 PM
ASA by default inspects the traffic leaving and allows the returning traffic to pass through without any need for any ACL, but if you want to allow the traffic initiated from outside to inside, you need an ACL entry to allow it.
Regards,
Aref
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 10:38 PM
Hi,
Can you capture traffic on your outside interface to make sure that you are receiving traffic from SOHO using the right IP/Port
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2017 03:43 PM
Hi,
You need to translate the private IP address 10.0.0.2 to a public one. You can use the outside interface public IP, similar to this:
nat (CISCO-SOHO-Router,outside) source static Network-Object-SOHO-Cisco-Router interface service Service_OBJ_IPcamPort_TCP Service_OBJ_IPcamPort_TCP
Another thing, I am not sure if the incoming traffic would be sourcing from the same destination range ports toward the 10.0.0.2. If not please correct the ACLs to read as following:
access-list outside_access_in extended permit tcp any host 10.0.0.2 range 8186 8191 log disable
access-list outside_access_in extended permit udp any host 10.0.0.2 range 8186 8191 log disable
Also please remove the destination range from the service object.
Regards,
Aref
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2017 12:12 PM
I found out my main problem.
for acls for natting, only one acl needs to be Specified for the node that has the natted service. I believe the asa will build acls on there own to allow non nated traffic to come back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2017 12:29 PM
ASA by default inspects the traffic leaving and allows the returning traffic to pass through without any need for any ACL, but if you want to allow the traffic initiated from outside to inside, you need an ACL entry to allow it.
Regards,
Aref
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




