- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5506-X getting ip from ISP but no DNS servers, also can't connect to outside
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 12:29 PM
Okay so in my last discussion I wasn't getting an IP address from the ISP. Now I'm getting the ISP assigned dynamic IP address on the ASA, but I'm not getting the DNS servers of the ISP automatically on the ASA. I do get the DNS servers automatically when I connect a different device so it has to be a wrong configuration.
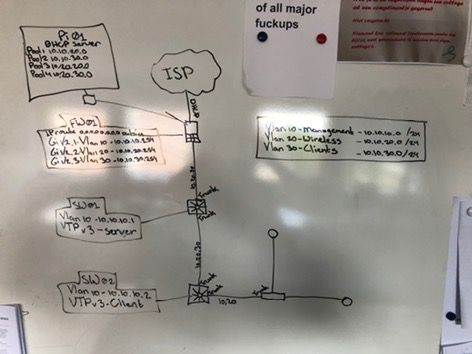
Also this network is gonna be a little difficult for a starter, so I'm trying my best to explain it with a picture.
Facts:
Firewall:
int gi1/1 - outside interface - dynamic IP - does get an IP address assigned from the DHCP of the ISP, but no DNS servers.
int gi1/2 - split in 3 subinterfaces
int gi1/2.1 - vlan 10 - subnet 10.10.10.0 /24 - management
int gi1/2.2 - vlan 20 - subnet 10.10.20.0 /24 - wireless
int gi1/2.3 - vlan 30 - subnet 10.10.30.0 /24 - clients
int gi1/3 - range 10.1.1.0 /24 - im gonna put the DHCP server (raspberry pi) here later under 10.1.1.1
SW01:
Int gi0/1 - To-->FW01 - trunk - allow Vlan 10,20,30
Int gi0/2 - To-->SW02 - trunk - allow Vlan 10,20,30
VTP - server - ver 3
SW02:
Int gi0/1 - To-->SW01 - trunk - allow Vlan 10,20,30
Int gi0/2 - To-->WLC01 - trunk - allow Vlan 10,20
So let me first focus on this part. The WLC and APs aren't important at the moment.
I've got 2 layer 3 switches, but they run as a layer 2. I put them both in Vlan 10 to assign an IP address so they are reachable with SSH later. Lets be honest, putting that console cable in everytime gets annoying :).
So I've got a client on SW01 fa0/1. Put the port in Vlan 30. Since I don't have a DHCP server yet I had to assign an IP by hand. I assigned it 10.10.30.100 255.255.255.0 default gateway 10.10.30.254. I can ping my default gateway, so that works, but I can't ping the 10.10.10.1 which I assigned to the SW01, so there is something wrong in the config of the ASA since that is the one who routes at the moment. Also when I ping to outside from the ASA it works, for example 8.8.8.8
FW01(config)# ping 8.8.8.8 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 10/14/20 ms
So it works to outside from the ASA, but when I ping 8.8.8.8 on the client it doesn't go through, also an issue with the ASA config. I'll put the config in another comment.
TL;DR
- ASA isn't getting the ISP assigned DNS servers, but does get an IP address from the ISP DHCP server.
- From the inside network I can ping the gateway but I can't ping further than the gateway.
Solved! Go to Solution.
- Labels:
-
Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 02:40 PM
Ok, looks like you have no ACL to permit ICMP replies. 2 options, ACL or MPF
access-list Outside_access_in permit icmp any any echo-reply
access-group Outside_access_in in interface Outside
OR
policy-map global_policy
class inspection_default
inspect icmp
inspect icmp error
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 12:34 PM - edited 07-04-2019 12:36 PM
ASA Version 9.8(3)14 ! hostname FW01 domain-name levoo.com names ddns update method FW01 ddns both ! no mac-address auto ! interface GigabitEthernet1/1 description outside nameif outside security-level 0 ddns update hostname FW01 ddns update FW01 dhcp client update dns ip address dhcp setroute ! interface GigabitEthernet1/2 bridge-group 1 nameif inside_1 security-level 100 ! interface GigabitEthernet1/2.1 description MANAGEMENT management-only vlan 10 nameif MANAGEMENT security-level 100 ip address 10.10.10.254 255.255.255.0 ! interface GigabitEthernet1/2.2 description WIRELESS vlan 20 nameif WIRELESS security-level 100 ip address 10.10.20.254 255.255.255.0 ! interface GigabitEthernet1/2.3 description CLIENTS vlan 30 nameif CLIENTS security-level 100 ip address 10.10.30.254 255.255.255.0 ! interface GigabitEthernet1/3 description DHCP nameif DHCP security-level 100 ip address 10.1.1.254 255.255.255.0 ! interface GigabitEthernet1/4 bridge-group 1 nameif inside_3 security-level 100 ! interface GigabitEthernet1/5 bridge-group 1 nameif inside_4 security-level 100 ! interface GigabitEthernet1/6 bridge-group 1 nameif inside_5 security-level 100 ! interface GigabitEthernet1/7 bridge-group 1 nameif inside_6 security-level 100 ! interface GigabitEthernet1/8 bridge-group 1 nameif inside_7 security-level 100 ! interface Management1/1 management-only no nameif no security-level no ip address ! interface BVI1 nameif inside security-level 100 ip address 192.168.1.1 255.255.255.0 ! ftp mode passive clock timezone CEST 1 clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00 dns domain-lookup outside dns server-group DefaultDNS name-server 8.8.8.8 outside name-server 8.8.4.4 outside domain-name levoo.com same-security-traffic permit inter-interface object network obj_any1 subnet 0.0.0.0 0.0.0.0 object network obj_any2 subnet 0.0.0.0 0.0.0.0 object network obj_any3 subnet 0.0.0.0 0.0.0.0 object network obj_any4 subnet 0.0.0.0 0.0.0.0 object network obj_any5 subnet 0.0.0.0 0.0.0.0 object network obj_any6 subnet 0.0.0.0 0.0.0.0 object network obj_any7 subnet 0.0.0.0 0.0.0.0 object network MANAGEMENT subnet 10.10.10.0 255.255.255.0 object network WIRELESS subnet 10.10.20.0 255.255.255.0 object network CLIENTS subnet 10.10.30.0 255.255.255.0 pager lines 24 logging asdm informational mtu outside 1500 mtu inside_1 1500 mtu MANAGEMENT 1500 mtu WIRELESS 1500 mtu CLIENTS 1500 mtu DHCP 1500 mtu inside_3 1500 mtu inside_4 1500 mtu inside_5 1500 mtu inside_6 1500 mtu inside_7 1500 no failover no monitor-interface inside no monitor-interface service-module icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected arp rate-limit 16384 nat (any,any) source static any any nat (MANAGEMENT,outside) source static any any ! object network obj_any3 nat (inside_3,outside) dynamic interface object network obj_any4 nat (inside_4,outside) dynamic interface object network obj_any5 nat (inside_5,outside) dynamic interface object network obj_any6 nat (inside_6,outside) dynamic interface object network obj_any7 nat (inside_7,outside) dynamic interface object network MANAGEMENT nat (MANAGEMENT,outside) dynamic interface object network WIRELESS nat (WIRELESS,outside) dynamic interface object network CLIENTS nat (CLIENTS,outside) dynamic interface timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 timeout conn-holddown 0:00:15 timeout igp stale-route 0:01:10 user-identity default-domain LOCAL aaa authentication login-history http server enable http 192.168.1.0 255.255.255.0 inside_3 http 192.168.1.0 255.255.255.0 inside_4 http 192.168.1.0 255.255.255.0 inside_5 http 192.168.1.0 255.255.255.0 inside_6 http 192.168.1.0 255.255.255.0 inside_7 http 10.10.10.0 255.255.255.0 MANAGEMENT http 10.10.20.0 255.255.255.0 WIRELESS http 10.10.30.0 255.255.255.0 CLIENTS no snmp-server location no snmp-server contact service sw-reset-button crypto ipsec security-association pmtu-aging infinite crypto ca trustpool policy telnet timeout 5 ssh stricthostkeycheck ssh key-exchange group dh-group1-sha1 console timeout 0 dhcp-client client-id interface outside dhcp-client update dns server both dhcpd auto_config outside ! dhcpd address 192.168.1.5-192.168.1.254 inside dhcpd enable inside ! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept ntp server 80.127.119.186 source outside prefer webvpn anyconnect-essentials cache disable error-recovery disable dynamic-access-policy-record DfltAccessPolicy username levoo privilege 15 ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 no tcp-inspection policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options ! service-policy global_policy global prompt hostname context no call-home reporting anonymous Cryptochecksum:0b323b9e49bdc52bcbc532f698988e82
ps. if you see anything else that could be adjusted in this config for best practice please let me know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 03:16 AM
Is there actually no one that can help?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 01:29 PM
What is the output of "show nat", it could be traffic is unintentially natted behind "nat (any,any) source static any any". Upload the output so we can confirm the hit counts on the rules.
Can you run a test with the packet-tracer command on the CLI and upload the output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 01:35 PM
Will this do?
FW01(config-if)# show nat
Manual NAT Policies (Section 1)
1 (any) to (any) source static any any
translate_hits = 58688, untranslate_hits = 87033
2 (MANAGEMENT) to (outside) source static any any
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (MANAGEMENT) to (outside) source dynamic MANAGEMENT interface
translate_hits = 0, untranslate_hits = 0
2 (WIRELESS) to (outside) source dynamic WIRELESS interface
translate_hits = 0, untranslate_hits = 0
3 (CLIENTS) to (outside) source dynamic CLIENTS interface
translate_hits = 0, untranslate_hits = 0
4 (inside_3) to (outside) source dynamic obj_any3 interface
translate_hits = 0, untranslate_hits = 0
5 (inside_4) to (outside) source dynamic obj_any4 interface
translate_hits = 0, untranslate_hits = 0
6 (inside_5) to (outside) source dynamic obj_any5 interface
translate_hits = 0, untranslate_hits = 0
7 (inside_6) to (outside) source dynamic obj_any6 interface
translate_hits = 0, untranslate_hits = 0
8 (inside_7) to (outside) source dynamic obj_any7 interface
translate_hits = 0, untranslate_hits = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 01:54 PM
Remove the first nat rule "no nat (any,any) source static any any" traffic should then start to hit the dynamic nat rules you've already got defined.
Post the output of "show nat" and a packet-tracer output if this does not work. E.g-
packet-tracer input CLIENTS icmp 10.10.30.100 8 0 8.8.8.8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 02:33 PM
ping request to any ip that's not in the same subnet gets timed out.
Here is the packet-tracer, which shows it's allowed, but doesn't seem like it actually is.
FW01(config)# packet-tracer input cLIENTS icmp 10.10.30.100 8 0 8.8.8.8
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 94.212.130.1 using egress ifc outside
Phase: 2
Type: NAT
Subtype:
Result: ALLOW
Config:
object network CLIENTS
nat (CLIENTS,outside) dynamic interface
Additional Information:
Dynamic translate 10.10.30.100/0 to 94.212.130.164/23014
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 74244, packet dispatched to next module
Result:
input-interface: CLIENTS
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allowAnd here is the show NAT
FW01(config)# sh nat
Auto NAT Policies (Section 2)
1 (MANAGEMENT) to (outside) source dynamic MANAGEMENT interface
translate_hits = 0, untranslate_hits = 0
2 (WIRELESS) to (outside) source dynamic WIRELESS interface
translate_hits = 0, untranslate_hits = 0
3 (CLIENTS) to (outside) source dynamic CLIENTS interface
translate_hits = 126, untranslate_hits = 0
4 (inside_3) to (outside) source dynamic obj_any3 interface
translate_hits = 0, untranslate_hits = 0
5 (inside_4) to (outside) source dynamic obj_any4 interface
translate_hits = 0, untranslate_hits = 0
6 (inside_5) to (outside) source dynamic obj_any5 interface
translate_hits = 0, untranslate_hits = 0
7 (inside_6) to (outside) source dynamic obj_any6 interface
translate_hits = 0, untranslate_hits = 0
8 (inside_7) to (outside) source dynamic obj_any7 interface
translate_hits = 627, untranslate_hits = 55
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 02:40 PM
Ok, looks like you have no ACL to permit ICMP replies. 2 options, ACL or MPF
access-list Outside_access_in permit icmp any any echo-reply
access-group Outside_access_in in interface Outside
OR
policy-map global_policy
class inspection_default
inspect icmp
inspect icmp error
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 02:55 PM
Thanks for your quick responses!
I can ping from the client on 10.10.30.100 to outside now. I also can browse the internet. Which is great of course!
Thanks a lot!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2019 02:37 PM
Now it says it failed.
FW01(config)# packet-tracer input CLIENTS icmp 10.10.30.100 0 8 8.8.8.8 Phase: 1 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 94.212.130.1 using egress ifc outside Phase: 2 Type: NAT Subtype: Result: ALLOW Config: object network CLIENTS nat (CLIENTS,outside) dynamic interface Additional Information: Phase: 3 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 4 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Result: input-interface: CLIENTS input-status: up input-line-status: up output-interface: outside output-status: up output-line-status: up Action: drop Drop-reason: (nat-xlate-failed) NAT failed
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide