- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5506-X-W trunk
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5506-X-W trunk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2017 02:23 PM - edited 02-21-2020 06:17 AM
Hi
I have some trouble creating a "trunk" on the ASA5506-x-w.
On the old 5505 easy switchport trunk etc..
but on the 5506 with sub-interfacec, i have a hard time to get my setup working, (simple setup)
and is a bit embarrassed that i have to ask for help about this, but i am in a dead lock and don't know how to get any further.
the setup:
have a inside network 192.168.1.0/24 vlan10 and have a DMZ 192.168.200.0/24. vlan 200
My main building only have vlan 10 and the other building have both vlan 10 and 200 (Trunk)
from my main building a can reach vlan 200 but not my default vlan 10.
from my other building i can reach vlan 10 and internet.
as is it now in a non working state:
ASA:
interface GigabitEthernet1/3
bridge-group 1
nameif inside_2
security-level 100
!
interface GigabitEthernet1/3.1
shutdown
vlan 1
bridge-group 1
nameif inside-vlan1
security-level 100
!
interface GigabitEthernet1/3.10
vlan 10
nameif inside-vlan10
security-level 100
no ip address
!
interface GigabitEthernet1/3.200
vlan 200
nameif DMZ
security-level 50
ip address 192.168.200.1 255.255.255.0
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
Switch:
(can't reach the switch right now, so this is from memmory)
interface gigabit 0/1
switchport mode trunk
switchport mode trunk native vlan 10
switchport allowed vlan 1,20,200
fa interface 0/1
switchport access
swich port access vlan 10
fa interface 0/3
switchport access
swich port access vlan 200
vlan 1,10,200
interface vlan 200
ip add 192.168.1.200/24
default gateway 192.168.1.1
Do anyone know what i am doint wrong?
Br Kevin
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2017 04:53 PM - edited 09-09-2017 04:57 PM
Hi
Why are you using bridge-group ?
Your subnets are 192.168.1.0/24 for vlan10 and 192.168.200.0/24 for DMZ.
Have you tried the following configuration?
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
no shutdown
!
interface GigabitEthernet1/3.10
vlan 10
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
no shutdown
!
interface GigabitEthernet1/3.200
vlan 200
nameif dmz
security-level 100
ip address 192.168.200.1 255.255.255.0
no shutdown
This configuration is straight forward and standard. Try that and let us know.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2017 10:59 PM
Hi Francesco
Thanks for the reply
I am using bridge-group because i want the "switch" function of the asa.
I have a AP direct attached in gi 0/2 to provide wireless to my house.
I dont have a switch in my main building
And from what i know i have to ude bridge-group to get this function or is there a nother way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2017 08:21 AM
Hi
I missed the part where you don't have switch on your site and this is why you absoluetly need to use bridge-group.
I'm using an ASAv version 9.8 within GNS3 to make it quick.
PC1 is connected on G0/0
PC2 is connected on G0/1
PC3 is connected on G0/2
PC4 and switch are connected to G0/3
ISP router connected to G0/4
I attach the ASA config, then you can take a look how I managed the bridge-group and apply the same philosophy to your asa. It's a very basic config with acl permitting any just to show you how it works.
All PCs can be reached no matter from which vlan you're.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 01:37 PM - edited 09-11-2017 01:39 PM
HI franccesco
sorry to say still cant get it to work?
i got it to semi work, i could reach the guest house from the main house, as i want but then the guest house lost its internet access.. Hmmm and now back to only being able to reach vlan 200
i have changed vlan 10 to 1 just to see if that did anything good.
cant figure out what i am doing wrong.. here is my config
Switch config:
version 12.1
no service pad
service timestamps debug uptime
service timestamps log uptime
service password-encryption
!
hostname xx
!
clock timezone cet 1
clock summer-time ECTD recurring last Sun Mar 2:00 last Sun Oct 3:00
ip subnet-zero
ip dhcp excluded-address 192.168.200.1 192.168.200.5
!
ip dhcp pool xx-pool
network 192.168.200.0 255.255.255.0
default-router 192.168.200.1
dns-server 8.8.8.8 8.8.4.4
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
interface FastEthernet0/1
switchport mode access
random-detect
spanning-tree portfast
!
interface FastEthernet0/2
switchport access vlan 200
switchport mode access
spanning-tree portfast
!
interface FastEthernet0/3
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/4
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/5
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/6
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/7
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/8
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface GigabitEthernet0/1
switchport mode trunk
no keepalive
spanning-tree portfast
!
interface Vlan1
ip address 192.168.1.200 255.255.255.0
no ip route-cache
!
interface Vlan200
ip address 192.168.200.2 255.255.255.0
no ip route-cache
shutdown
!
ip default-gateway 192.168.1.1
ip http server
banner motd ^CCC
UNAUTHORISED ACCESS TO THIS DEVICE IS PROHIBITED.
You must have explicit permission to access this
device. All activities performed on this device
are logged, any violations of this policy will be
prosecuted.
^C
!
line con 0
exec-timeout 90 0
logging synchronous
line vty 0 4
logging synchronous
login
line vty 5 15
logging synchronous
login
!
ntp clock-period 17180147
ntp server
!
end
ASA config:
hostname
names
ip local pool vpn_subnet 192.168.100.10-192.168.100.100 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.2.2 255.255.255.0
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
bridge-group 1
no nameif
no security-level
!
interface GigabitEthernet1/3.10
vlan 1
bridge-group 1
nameif Inside_vlan1
security-level 100
!
interface GigabitEthernet1/3.200
vlan 200
bridge-group 2
nameif DMZ_vlan200
security-level 50
!
interface GigabitEthernet1/4
bridge-group 1
nameif inside_3
security-level 100
!
interface GigabitEthernet1/5
bridge-group 1
nameif inside_4
security-level 100
!
interface GigabitEthernet1/6
bridge-group 1
nameif inside_5
security-level 100
!
interface GigabitEthernet1/7
bridge-group 1
nameif inside_6
security-level 100
!
interface GigabitEthernet1/8
bridge-group 1
nameif inside_7
security-level 100
!
interface GigabitEthernet1/9
nameif wifi
security-level 100
ip address 192.168.10.1 255.255.255.0
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface BVI2
nameif DMZ
security-level 50
ip address 192.168.200.1 255.255.255.0
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
!
object network obj_any1
nat (inside_1,outside) dynamic interface
object network obj_any3
nat (inside_3,outside) dynamic interface
object network obj_any4
nat (inside_4,outside) dynamic interface
object network obj_any5
nat (inside_5,outside) dynamic interface
object network obj_any6
nat (inside_6,outside) dynamic interface
object network obj_any7
nat (inside_7,outside) dynamic interface
object network obj_any_wifi
nat (wifi,outside) dynamic interface
access-group outside_access_in in interface outside
access-group inside_access_in_1 in interface inside
!
route outside 0.0.0.0 0.0.0.0 192.168.2.1 1
!
dhcpd dns 8.8.8.8 8.8.4.4
dhcpd auto_config outside
!
dhcpd address 192.168.10.2-192.168.10.254 wifi
dhcpd enable wifi
!
dhcpd address 192.168.1.5-192.168.1.36 inside
dhcpd dns 8.8.8.8 8.8.4.4 interface inside
dhcpd enable inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 02:06 PM - edited 09-11-2017 02:08 PM
Hi Francesco
Thanks for the effert.
But i still cant make it work, or i got it to semi work.. i could reach the guest houe as wanted but then the guest house lost it's internet connection??
i have tryed to change vlan 10 to 1 just to see if that did anything good, but it didnt.
i am still able to reach vlan 200
im lost... :(
ASA config:
hostname xx
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.2.2 255.255.255.0
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
bridge-group 1
nameif null
security-level 0
!
interface GigabitEthernet1/3.10
vlan 1
bridge-group 1
nameif Inside_vlan1
security-level 100
!
interface GigabitEthernet1/3.200
vlan 200
bridge-group 2
nameif DMZ_vlan200
security-level 50
!
interface GigabitEthernet1/4
bridge-group 1
nameif inside_3
security-level 100
!
interface GigabitEthernet1/5
bridge-group 1
nameif inside_4
security-level 100
!
interface GigabitEthernet1/6
bridge-group 1
nameif inside_5
security-level 100
!
interface GigabitEthernet1/7
bridge-group 1
nameif inside_6
security-level 100
!
interface GigabitEthernet1/8
bridge-group 1
nameif inside_7
security-level 100
!
interface GigabitEthernet1/9
nameif wifi
security-level 100
ip address 192.168.10.1 255.255.255.0
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface BVI2
nameif DMZ
security-level 50
ip address 192.168.200.1 255.255.255.0
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
!
object network obj_any1
nat (inside_1,outside) dynamic interface
object network obj_any3
nat (inside_3,outside) dynamic interface
object network obj_any4
nat (inside_4,outside) dynamic interface
object network obj_any5
nat (inside_5,outside) dynamic interface
object network obj_any6
nat (inside_6,outside) dynamic interface
object network obj_any7
nat (inside_7,outside) dynamic interface
object network obj_any_wifi
nat (wifi,outside) dynamic interface
access-group outside_access_in in interface outside
access-group inside_access_in_1 in interface inside
!
route outside 0.0.0.0 0.0.0.0 192.168.2.1 1
!
Switch config:
hostname xx
!
clock timezone cet 1
clock summer-time ECTD recurring last Sun Mar 2:00 last Sun Oct 3:00
ip subnet-zero
ip dhcp excluded-address 192.168.200.1 192.168.200.5
!
ip dhcp pool xx-pool
network 192.168.200.0 255.255.255.0
default-router 192.168.200.1
dns-server 8.8.8.8 8.8.4.4
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
interface FastEthernet0/1
description Bio_router
switchport mode access
random-detect
spanning-tree portfast
!
interface FastEthernet0/2
description Intel NUC port 0/1
switchport access vlan 200
switchport mode access
spanning-tree portfast
!
interface FastEthernet0/3
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/4
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/5
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/6
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/7
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface FastEthernet0/8
switchport mode access
shutdown
random-detect
spanning-tree portfast
!
interface GigabitEthernet0/1
switchport mode trunk
no keepalive
spanning-tree portfast
!
interface Vlan1
ip address 192.168.1.200 255.255.255.0
no ip route-cache
!
interface Vlan200
ip address 192.168.200.2 255.255.255.0
no ip route-cache
shutdown
!
ip default-gateway 192.168.1.1
ip http server
banner motd ^CCC
UNAUTHORISED ACCESS TO THIS DEVICE IS PROHIBITED.
You must have explicit permission to access this
device. All activities performed on this device
are logged, any violations of this policy will be
prosecuted.
^C
!
line con 0
exec-timeout 90 0
logging synchronous
line vty 0 4
logging synchronous
login
line vty 5 15
logging synchronous
login
!
ntp clock-period 17180147
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 05:10 PM
On interface GigabitEthernet1/3, you have configured some stuff and you don't have because the config is done on sub-interfaces:
interface GigabitEthernet1/3
no bridge-group 1
no nameif null
no security-level 0
For the nat, I trust what you did but I don't see your groups like obj_any1
On the switch the svi vlan 200 is down. Is that normal?
What is the default gateway for vlan 1 and vlan 200 hosts?
Then, when you're doing ping tests, do it from the device to ping another device. Don't use ASA to make ping tests.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 02:18 PM
Do you have an IP address for both Bridge groups? Do you have SVIs on the switch?
Mike.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 02:29 PM
Hi Mike
taken from the config i have uploaded:
ASA:
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface BVI2
nameif DMZ
security-level 50
ip address 192.168.200.1 255.255.255.0
Switch:
nterface Vlan1
ip address 192.168.1.200 255.255.255.0
no ip route-cache
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 02:33 PM
OK, what happens if you try to ping devices on both vlans? Do you have ARP entries for both vlans?
Show ARP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2017 02:55 PM
From the ASA
ping 192.168.1.200
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.200, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
sh arp
outside 192.168.2.1 e0b9.e59a.6946 14
DMZ 192.168.200.5 c03f.d561.85c2 3570
wifi 192.168.10.2 0042.5ad0.00b4 170
inside 192.168.1.5 8019.343f.0fe8 0
inside 192.168.1.10 5840.4e1b.26fa 35
inside 192.168.1.12 b827.eb73.2b54 48
inside 192.168.1.120 c097.2716.a246 487
inside 192.168.1.8 484b.aab9.8ca7 870
inside 192.168.1.6 5032.75a9.fed5 1728
inside 192.168.1.2 d850.e6af.17b0 5524
inside 192.168.1.200 0011.5cfa.4440 6934
inside 192.168.1.7 f48c.5079.595a 8781
inside 192.168.1.9 0024.e415.3ddc 10980
inside 192.168.1.30 f48c.5079.595a 11384
inside 192.168.1.29 484b.aab9.8ca7 12782
inside 192.168.1.28 5840.4e1b.26fa 13097
inside 192.168.1.22 5032.75a9.fed5 13177
inside 192.168.1.19 8019.343f.0fe8 13268
From switch:
ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
...
Success rate is 0 percent (0/3)
Bio-Switch#ping 192.168.200.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.200.1, timeout is 2 seconds:
...
Success rate is 0 percent (0/3)
Bio-Switch#sh arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.1.1 75 286f.7fd1.39d3 ARPA Vlan1
Internet 192.168.1.200 - 0011.5cfa.4440 ARPA Vlan1
Internet 192.168.200.2 - 0011.5cfa.4440 ARPA Vlan200
if i take the switch port fa0/1 direct into my computer i am getting:
Spanning-tree-(for-briges)_00
5 times and the loop
and 5 time again over and over
dont get any dhcp from the ASA
Dont know if that means anything?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2017 05:17 AM
I would either suggest to open a ticket with TAC or get into a call so we can take a look at this together? is the firewall facing the Internet so I can help you configure?
I just recently stopped working for TAC so I think I still have it.
juanmh8419@gmail.com
Skype: juanmh8419@hotmail.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2017 06:16 AM
Hi Again
Now i have made a small simple setup at work with new equipment similar to mine just to see if this ware a problem with my equipment.
Have anyone actually tried this and made this work?
Why can i access cross networks but not connect to something that is connected to the same network?
Have anyone made this work, or is this a bug and TAC have to look into?
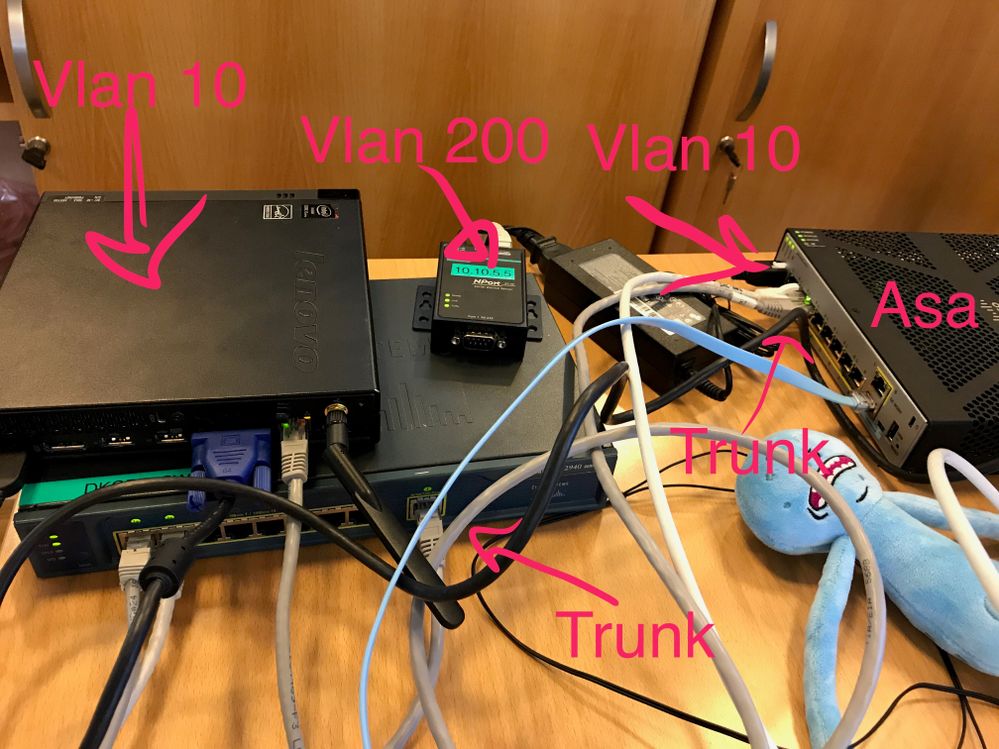
here is the config and test from pc to the other equipment
So in the ASA the 'white cable' is vlan 10 connected to the computer
and the 'grey cable' is a trunk to the switch
Here is the config and test
hostname Switch
!
ip subnet-zero
!
vtp domain DKCPH-TERM
vtp mode transparent
!
spanning-tree mode pvst
no spanning-tree optimize bpdu transmission
spanning-tree extend system-id
!
vlan 10
name inside
!
vlan 200
name DMZ
!
interface FastEthernet0/1
switchport access vlan 10
switchport mode access
!
interface FastEthernet0/2
switchport access vlan 200
switchport mode access
!
interface FastEthernet0/3
switchport access vlan 10
switchport mode access
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface GigabitEthernet0/1
switchport mode trunk
spanning-tree portfast trunk
!
interface Vlan1
no ip address
no ip route-cache
shutdown
!
interface Vlan10
ip address 192.168.1.200 255.255.255.0
no ip route-cache
!
interface Vlan200
ip address 192.168.200.2 255.255.255.0
no ip route-cache
shutdown
!
ip default-gateway 192.168.1.1
ip http server
!
line con 0
line vty 5 15
!
!
end
------------------------------------------------------------------------
Switch#sh interfaces trunk
Port Mode Encapsulation Status Native vlan
Gi0/1 on 802.1q trunking 1
Port Vlans allowed on trunk
Gi0/1 1-4094
Port Vlans allowed and active in management domain
Gi0/1 1,10,200
Port Vlans in spanning tree forwarding state and not pruned
Gi0/1 1,10,200
---------------------------------------------------------------------------
ASA
ASA Version 9.8(1)
!
hostname ciscoasa
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address dhcp setroute
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/3.10
vlan 10
bridge-group 1
nameif Inside_vlan10
security-level 100
!
interface GigabitEthernet1/3.200
vlan 200
bridge-group 2
nameif DMZ_vlan200
security-level 50
!
interface GigabitEthernet1/4
bridge-group 1
nameif inside_3
security-level 100
!
interface GigabitEthernet1/5
bridge-group 1
nameif inside_4
security-level 100
!
interface GigabitEthernet1/6
bridge-group 1
nameif inside_5
security-level 100
!
interface GigabitEthernet1/7
bridge-group 1
nameif inside_6
security-level 100
!
interface GigabitEthernet1/8
bridge-group 1
nameif inside_7
security-level 100
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface BVI2
nameif DMZ
security-level 50
ip address 192.168.200.1 255.255.255.0
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network inside
subnet 192.168.1.0 255.255.255.0
object network DMZ
subnet 192.168.200.0 255.255.255.0
object-group service DM_INLINE_SERVICE_2
service-object icmp
service-object icmp echo-reply
service-object icmp echo
object-group service DM_INLINE_SERVICE_1
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_3
service-object icmp
service-object icmp echo
service-object icmp echo-reply
object-group service DM_INLINE_SERVICE_5
service-object icmp
service-object icmp echo
service-object icmp echo-reply
access-list DMZ_vlan200_access_in extended permit object-group DM_INLINE_SERVICE_2 192.168.200.0 255.255.255.0 192.168.1.0 255.255.255.0 inactive
access-list DMZ_vlan200_access_in extended permit ip any any
access-list Inside_vlan10_access_in extended permit object-group DM_INLINE_SERVICE_5 192.168.1.0 255.255.255.0 192.168.200.0 255.255.255.0 inactive
access-list Inside_vlan10_access_in extended permit ip any any
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_3 192.168.1.0 255.255.255.0 192.168.200.0 255.255.255.0
access-list inside_access_in extended permit ip any any
access-list DMZ_access_in extended permit object-group DM_INLINE_SERVICE_1 192.168.200.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list DMZ_access_in extended permit ip any any inactive
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu inside_3 1500
mtu inside_4 1500
mtu inside_5 1500
mtu inside_6 1500
mtu inside_7 1500
mtu Inside_vlan10 1500
mtu DMZ_vlan200 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
!
object network obj_any1
nat (inside_1,outside) dynamic interface
object network obj_any3
nat (inside_3,outside) dynamic interface
object network obj_any4
nat (inside_4,outside) dynamic interface
object network obj_any5
nat (inside_5,outside) dynamic interface
object network obj_any6
nat (inside_6,outside) dynamic interface
object network obj_any7
nat (inside_7,outside) dynamic interface
access-group inside_access_in in interface inside
access-group Inside_vlan10_access_in in interface Inside_vlan10
access-group DMZ_access_in in interface DMZ
access-group DMZ_vlan200_access_in in interface DMZ_vlan200
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 inside_1
http 192.168.1.0 255.255.255.0 inside_3
http 192.168.1.0 255.255.255.0 inside_4
http 192.168.1.0 255.255.255.0 inside_5
http 192.168.1.0 255.255.255.0 inside_6
http 192.168.1.0 255.255.255.0 inside_7
http 192.168.1.0 255.255.255.0 Inside_vlan10
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.1.5-192.168.1.254 inside
dhcpd enable inside
!
dhcpd address 192.168.200.5-192.168.200.254 DMZ
dhcpd enable DMZ
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:306ca950ee815065e3ff375b5914fa6f
: end
-------------------------------
ciscoasa# sh arp
inside 192.168.1.25 0023.2461.e54b 7
inside 192.168.1.7 c85b.7674.8284 9
inside 192.168.1.200 0019.55fb.f080 1390
DMZ 192.168.200.25 0090.e85f.b57a 641
--------------------------------------------------------------
Ping from PC on vlan10 in ASA
Ping statistics for 192.168.1.25:
Packets: Sent = 2, Received = 0, Lost = 2 (100% loss),
---------------------------------------------------------------
Pinging 192.168.1.200 with 32 bytes of data:
Reply from 192.168.1.7: Destination host unreachable.
Request timed out.
Request timed out.
Ping statistics for 192.168.1.200:
Packets: Sent = 3, Received = 1, Lost = 2 (66% loss),
--------------------------------------------------------------
Pinging 192.168.200.25 with 32 bytes of data:
Reply from 192.168.200.25: bytes=32 time=1ms TTL=255
Reply from 192.168.200.25: bytes=32 time=2ms TTL=255
Reply from 192.168.200.25: bytes=32 time=2ms TTL=255
Reply from 192.168.200.25: bytes=32 time=2ms TTL=255
Ping statistics for 192.168.200.25:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 2ms, Average = 1ms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2017 08:43 AM
Remove the vlan 10 address from the switch please and test
juanmh8419@gmail.com
Skype: juanmh8419@hotmail.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2017 08:50 AM
Please remove the vlan 10 address from the switch and please and test. it seems as if you have two devices doing the inter vlan routing
juanmh8419@gmail.com
Skype: juanmh8419@hotmail.com
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide