- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5510 Internal Routing Problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 07:11 AM - edited 03-11-2019 03:18 PM
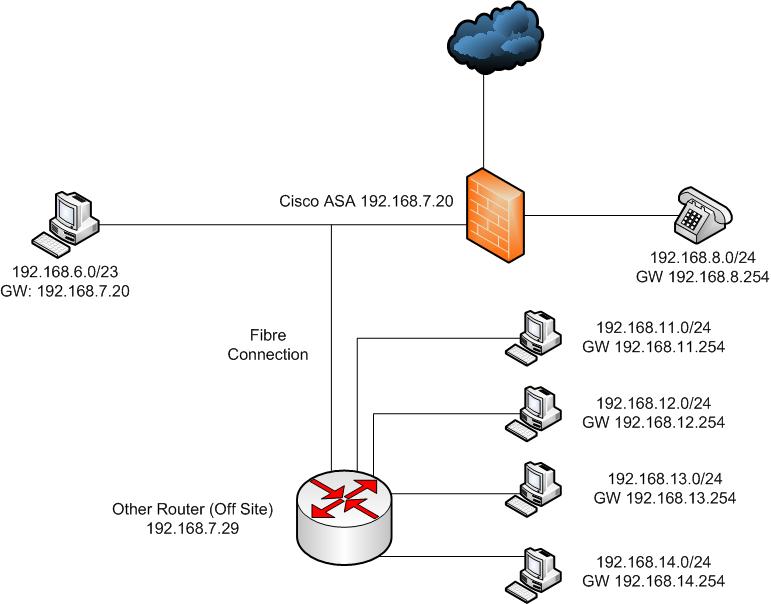
I am having a problem where my (newly setup) ASA 5510 is closing TCP connections for data routed to another router on my internal network. Here is a diagram of how its setup:
Here is my running conf on the ASA (some bits censored):
Result of the command: "show run"
: Saved
:
ASA Version 8.4(3)
!
hostname HPAFW01
domain-name SNIP
enable password SNIP
passwd SNIP
names
name 192.168.7.26 Spam_Firewall
name 192.168.12.0 xxxSt_VideoSec description xxx St Video/Security
name 192.168.8.0 Phone_System-network description Phone System
name 192.168.6.0 Inside-network description Main Network
name 192.168.11.0 EnduraSM-network description Endura System Manager
name 192.168.15.0 Data-network1 description Data1
name 192.168.13.0 Video-network1 description Video/Security1
name 192.168.16.0 Data-network2 description Data2
name 192.168.14.0 Video-network2 description Video/Security2
name 192.168.7.11 FTP_Server description FTP Server
name 192.168.7.17 Mail_Server
name 192.168.6.1 yyy description yyy
name 192.168.6.2 zzz description zzz
name 192.168.7.12 HPA02
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address x.x.x.x 255.255.255.240
!
interface Ethernet0/1
nameif Inside
security-level 100
ip address 192.168.7.20 255.255.254.0
!
interface Ethernet0/2
nameif Phone_System
security-level 100
ip address 192.168.8.254 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
boot system disk0:/asa843-k8.bin
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns server-group DefaultDNS
domain-name abc.ca
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network MainNetwork
subnet 192.168.6.0 255.255.254.0
object network HPA02
host 192.168.7.12
object network Phone_System-network
subnet 192.168.8.0 255.255.255.0
description Created during name migration
object network HPA01
host 192.168.7.11
description FTP Server
object network xxx
host 192.168.6.1
description xxx
object network HPA07
host 192.168.7.17
description Mail Server
object network Pelco_Endura-Network
subnet 192.168.11.0 255.255.255.0
description Endura System Manager
object network Data-Network1
subnet 192.168.15.0 255.255.255.0
description Data Network 1
object network Security-Network1
subnet 192.168.13.0 255.255.255.0
description Sec Network 1
object network Data-Network2
subnet 192.168.16.0 255.255.255.0
description Data Network 2
object network Security-Network2
subnet 192.168.14.0 255.255.255.0
description Sec Network 2
object network Cisco-Management-Network
subnet 192.168.1.0 255.255.255.0
object network xxx
host 192.168.6.2
description xxx
object network SpamFirewall
host 192.168.7.26
description Barracuda Spam Firewall
object network HTTP
host 192.168.7.26
object network msrdp
host 192.168.6.5
object network HPA03
host 192.168.7.13
object network Ping
subnet 192.168.6.0 255.255.254.0
object network HTTP-In-HPA10
host 192.168.6.4
object network NAT-HPA01-FTP-In
host 192.168.7.11
object network NAT-HPA01-FTPData-In
host 192.168.7.11
object service FTPData50000-50010
service tcp source range 50000 50010 destination range 50000 50010
object network NAT-HPA03-PPTP-In
host 192.168.7.13
object network NAT-HPA07-HTTPS-In
host 192.168.7.17
object network NAT-Barracuda-SMTP-In
host 192.168.7.26
object network NAT-HPA07-DrOfficeSMTP-In
host 192.168.7.17
object network NAT-HPA07-HTTPSSPOWA-In
host 192.168.7.17
object network NAT-HPA07-HTTPSIntranet-In
host 192.168.7.17
object network NAT-HPA07-HTTPS2-In
host 192.168.7.17
object network DrOffice
host a.a.a.a
object network DrOffice2
host b.b.b.b
object network HPA07-IP2
host 192.168.7.37
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_TCP_1 tcp
port-object eq ftp
port-object eq www
object-group network DM_INLINE_NETWORK_1
network-object object HPA_MainNetwork
network-object object Pelco_Endura-Network
network-object object Data-Network1
network-object object Security-Network1
network-object object Data-Network2
network-object object Security-Network2
object-group network DM_INLINE_NETWORK_2
network-object object xxx
network-object object yyy
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object ip
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_TCPUDP_1 tcp-udp
port-object eq 2252
port-object eq 5685
object-group service DM_INLINE_TCP_2 tcp
port-object range 50000 50010
port-object eq 990
object-group network DM_INLINE_NETWORK_12
network-object object DrOwsianik
network-object object DrPray
object-group service DM_INLINE_TCP_3 tcp
port-object eq 8000
port-object eq 8008
port-object eq 8332
port-object eq 8333
port-object eq 8480
object-group network DM_INLINE_NETWORK_14
network-object object HPA07
network-object object HPA07-IP2
access-list Inside_access_in remark Allow DNS Out
access-list Inside_access_in extended permit object-group TCPUDP any any eq domain log disable
access-list Inside_access_in remark Allow HTTP Out
access-list Inside_access_in extended permit tcp any any eq www log disable
access-list Inside_access_in remark Allow HTTPS Out
access-list Inside_access_in extended permit tcp any any eq https log disable
access-list Inside_access_in remark Allow FTP Out
access-list Inside_access_in extended permit tcp any any eq ftp log disable
access-list Inside_access_in remark Allow SSH Out
access-list Inside_access_in extended permit tcp any any eq ssh log disable
access-list Inside_access_in remark Allow SMTP Out
access-list Inside_access_in extended permit tcp any any eq smtp log disable
access-list Inside_access_in remark Allow Whois Out
access-list Inside_access_in extended permit tcp any any eq whois log disable
access-list Inside_access_in remark Allow Port 81 Out
access-list Inside_access_in extended permit tcp any any eq 81 log disable
access-list Inside_access_in remark Allow POP3 out for xxx
access-list Inside_access_in extended permit tcp object-group DM_INLINE_NETWORK_2 any eq pop3 log disable
access-list Inside_access_in remark Allow Blackberry BES Out
access-list Inside_access_in extended permit tcp any any eq 3101 log disable
access-list Inside_access_in remark Allow MSRDP Out
access-list Inside_access_in extended permit tcp any any eq 3389 log disable
access-list Inside_access_in remark Allow Port 8000 Out
access-list Inside_access_in extended permit tcp any any object-group DM_INLINE_TCP_3 log disable
access-list Inside_access_in remark Allow Interac Machines Out
access-list Inside_access_in extended permit tcp any any eq 8013 log disable
access-list Inside_access_in remark Allow Network Time Out
access-list Inside_access_in extended permit udp any any eq ntp log disable
access-list Inside_access_in remark Allow AIS Out
access-list Inside_access_in extended permit object-group TCPUDP any any object-group DM_INLINE_TCPUDP_1 log disable
access-list Inside_access_in remark Allow SFTP Out
access-list Inside_access_in extended permit tcp any any object-group DM_INLINE_TCP_2 log disable
access-list Inside_access_in remark Allow Traceroute Out
access-list Inside_access_in extended permit icmp any any traceroute log disable
access-list Inside_access_in extended permit icmp any any echo log disable
access-list Inside_access_in extended permit udp any any eq time log disable
access-list Inside_access_in remark Allow Access to Phone System
access-list Inside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 any any log disable
:SNIPPED OUT FOR SECURITY
pager lines 24
logging enable
logging asdm informational
mtu Outside 1500
mtu Inside 1500
mtu Phone_System 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-647.bin
no asdm history enable
arp timeout 14400
nat (any,Outside) source static NAT-HPA01-FTPData-In interface service FTPData50000-50010 FTPData50000-50010
!
object network HPA_MainNetwork
nat (Inside,Outside) dynamic interface
object network NAT-HPA01-FTP-In
nat (any,Outside) static interface service tcp ftp ftp
object network NAT-HPA03-PPTP-In
nat (any,Outside) static interface service tcp pptp pptp
object network NAT-HPA07-HTTPS-In
nat (any,Outside) static interface service tcp https https
object network NAT-Barracuda-SMTP-In
nat (any,Outside) static interface service tcp smtp smtp
object network NAT-HPA07-DrOSMTP-In
nat (any,any) static y.y.y.y service tcp smtp smtp
object network NAT-HPA07-HTTPSSPOWA-In
nat (any,any) static y.y.y.y service tcp 444 444
object network NAT-HPA07-HTTPSIntranet-In
nat (any,any) static y.y.y.y service tcp https https
object network NAT-HPA07-HTTPS2-In
nat (any,any) static y.y.y.y service tcp www www
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
access-group Phone_System_access_in in interface Phone_System
route Outside 0.0.0.0 0.0.0.0 z.z.z.z 10 :Routes to external Gateway
route Inside 192.168.9.0 255.255.255.0 192.168.7.29 1
route Inside EnduraSM-network 255.255.255.0 192.168.7.29 1
route Inside MainOffice_VideoSec 255.255.255.0 192.168.7.29 1
route Inside Video-network1 255.255.255.0 192.168.7.29 1
route Inside Video-network2 255.255.255.0 192.168.7.29 1
route Inside Data-network1 255.255.255.0 192.168.7.29 1
route Inside Data-network2 255.255.255.0 192.168.7.29 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http Inside-network 255.255.254.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sysopt connection tcpmss 0
telnet Inside-network 255.255.254.0 Inside
telnet timeout 5
ssh Inside-network 255.255.254.0 Inside
ssh timeout 5
console timeout 0
management-access Inside
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
ntp server 132.246.11.227 source Outside prefer
webvpn
!
class-map global-class
match access-list global_mpc
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class global-class
csc fail-open
!
service-policy global_policy global
prompt hostname context
: end
The router/switch at 192.168.7.29 (its an HP) has its default route set to the ASA and knows about all the networks connected to it.
The problem I am having is lets say I am sitting on my 192.168.6.0/23 network and want to send some data (or receive) from the 192.168.12.0/24 network. Packets not requiring the 3 step handshake work perfectly (eg, I can ping the 12.0/24 network and get a reply no problem). Any HTTP or other TCP connection gets immediately built and dropped by the ASA. Here is an excerpt of the log (from last night):
6|Jan 23 2012|18:20:09|302015|HPA02|53|192.168.12.10|64374|Built inbound UDP connection 27987 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/64374 (192.168.12.10/64374)
6|Jan 23 2012|18:20:09|302015|FTP_Server|53|192.168.12.10|64374|Built inbound UDP connection 27986 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/64374 (192.168.12.10/64374)
6|Jan 23 2012|18:20:09|302016|HPA02|53|192.168.12.10|62344|Teardown UDP connection 27984 for Inside:HPA02/53 to Inside:192.168.12.10/62344 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:09|302016|FTP_Server|53|192.168.12.10|62344|Teardown UDP connection 27983 for Inside:FTP_Server/53 to Inside:192.168.12.10/62344 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:09|302016|HPA02|53|192.168.13.178|55282|Teardown UDP connection 27980 for Inside:HPA02/53 to Inside:192.168.13.178/55282 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:09|302016|FTP_Server|53|192.168.13.178|55282|Teardown UDP connection 27979 for Inside:FTP_Server/53 to Inside:192.168.13.178/55282 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:09|302016|HPA02|53|192.168.13.10|57948|Teardown UDP connection 27978 for Inside:HPA02/53 to Inside:192.168.13.10/57948 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:09|302016|FTP_Server|53|192.168.13.10|57948|Teardown UDP connection 27977 for Inside:FTP_Server/53 to Inside:192.168.13.10/57948 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:08|106015|192.168.13.104|1720|192.168.8.1|61444|Deny TCP (no connection) from 192.168.13.104/1720 to 192.168.8.1/61444 flags ACK on interface Inside
6|Jan 23 2012|18:20:08|302015|HPA02|53|192.168.12.10|62344|Built inbound UDP connection 27984 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/62344 (192.168.12.10/62344)
6|Jan 23 2012|18:20:08|302015|FTP_Server|53|192.168.12.10|62344|Built inbound UDP connection 27983 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/62344 (192.168.12.10/62344)
6|Jan 23 2012|18:20:08|302014|192.168.7.16|56861|192.168.14.203|3001|Teardown TCP connection 27773 for Inside:192.168.7.16/56861 to Inside:192.168.14.203/3001 duration 0:00:30 bytes 0 SYN Timeout
6|Jan 23 2012|18:20:08|302013|192.168.7.16|57187|192.168.14.203|3001|Built inbound TCP connection 27982 for Inside:192.168.7.16/57187 (192.168.7.16/57187) to Inside:192.168.14.203/3001 (192.168.14.203/3001)
6|Jan 23 2012|18:20:08|106015|192.168.13.104|1720|192.168.8.1|61440|Deny TCP (no connection) from 192.168.13.104/1720 to 192.168.8.1/61440 flags ACK on interface Inside
6|Jan 23 2012|18:20:08|302015|HPA02|53|192.168.13.178|55282|Built inbound UDP connection 27980 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.13.178/55282 (192.168.13.178/55282)
6|Jan 23 2012|18:20:08|302015|FTP_Server|53|192.168.13.178|55282|Built inbound UDP connection 27979 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.178/55282 (192.168.13.178/55282)
6|Jan 23 2012|18:20:08|302015|HPA02|53|192.168.13.10|57948|Built inbound UDP connection 27978 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.13.10/57948 (192.168.13.10/57948)
6|Jan 23 2012|18:20:08|302015|FTP_Server|53|192.168.13.10|57948|Built inbound UDP connection 27977 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.10/57948 (192.168.13.10/57948)
6|Jan 23 2012|18:20:08|302014|192.168.7.16|56860|192.168.13.207|3001|Teardown TCP connection 27765 for Inside:192.168.7.16/56860 to Inside:192.168.13.207/3001 duration 0:00:30 bytes 0 SYN Timeout
6|Jan 23 2012|18:20:08|302013|192.168.7.16|57186|192.168.13.207|3001|Built inbound TCP connection 27976 for Inside:192.168.7.16/57186 (192.168.7.16/57186) to Inside:192.168.13.207/3001 (192.168.13.207/3001)
6|Jan 23 2012|18:20:08|302016|HPA02|53|192.168.12.10|64374|Teardown UDP connection 27972 for Inside:HPA02/53 to Inside:192.168.12.10/64374 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:07|302014|192.168.7.16|56859|192.168.13.206|3001|Teardown TCP connection 27761 for Inside:192.168.7.16/56859 to Inside:192.168.13.206/3001 duration 0:00:30 bytes 0 SYN Timeout
6|Jan 23 2012|18:20:07|302013|192.168.7.16|57179|192.168.13.206|3001|Built inbound TCP connection 27975 for Inside:192.168.7.16/57179 (192.168.7.16/57179) to Inside:192.168.13.206/3001 (192.168.13.206/3001)
6|Jan 23 2012|18:20:07|302013|192.168.7.16|57178|192.168.13.208|3001|Built inbound TCP connection 27974 for Inside:192.168.7.16/57178 (192.168.7.16/57178) to Inside:192.168.13.208/3001 (192.168.13.208/3001)
6|Jan 23 2012|18:20:07|302014|192.168.7.16|56858|192.168.14.204|3001|Teardown TCP connection 27758 for Inside:192.168.7.16/56858 to Inside:192.168.14.204/3001 duration 0:00:30 bytes 0 SYN Timeout
6|Jan 23 2012|18:20:07|302013|192.168.7.16|57177|192.168.14.204|3001|Built inbound TCP connection 27973 for Inside:192.168.7.16/57177 (192.168.7.16/57177) to Inside:192.168.14.204/3001 (192.168.14.204/3001)
6|Jan 23 2012|18:20:07|302015|HPA02|53|192.168.12.10|64374|Built inbound UDP connection 27972 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/64374 (192.168.12.10/64374)
6|Jan 23 2012|18:20:07|302016|HPA02|53|192.168.12.10|62344|Teardown UDP connection 27971 for Inside:HPA02/53 to Inside:192.168.12.10/62344 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:07|302016|HPA02|53|192.168.13.178|55185|Teardown UDP connection 27970 for Inside:HPA02/53 to Inside:192.168.13.178/55185 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:07|302016|FTP_Server|53|192.168.13.178|55185|Teardown UDP connection 27969 for Inside:FTP_Server/53 to Inside:192.168.13.178/55185 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:07|302016|FTP_Server|53|192.168.12.10|64374|Teardown UDP connection 27968 for Inside:FTP_Server/53 to Inside:192.168.12.10/64374 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:06|302015|HPA02|53|192.168.12.10|62344|Built inbound UDP connection 27971 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/62344 (192.168.12.10/62344)
6|Jan 23 2012|18:20:06|302015|HPA02|53|192.168.13.178|55185|Built inbound UDP connection 27970 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.13.178/55185 (192.168.13.178/55185)
6|Jan 23 2012|18:20:06|302015|FTP_Server|53|192.168.13.178|55185|Built inbound UDP connection 27969 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.178/55185 (192.168.13.178/55185)
6|Jan 23 2012|18:20:06|302015|FTP_Server|53|192.168.12.10|64374|Built inbound UDP connection 27968 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/64374 (192.168.12.10/64374)
6|Jan 23 2012|18:20:06|302016|FTP_Server|53|192.168.12.10|62344|Teardown UDP connection 27965 for Inside:FTP_Server/53 to Inside:192.168.12.10/62344 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:06|106015|192.168.13.105|1720|192.168.8.1|61442|Deny TCP (no connection) from 192.168.13.105/1720 to 192.168.8.1/61442 flags ACK on interface Inside
6|Jan 23 2012|18:20:06|106015|192.168.13.105|1720|192.168.8.1|61443|Deny TCP (no connection) from 192.168.13.105/1720 to 192.168.8.1/61443 flags ACK on interface Inside
6|Jan 23 2012|18:20:06|302016|HPA02|53|192.168.12.10|64374|Teardown UDP connection 27964 for Inside:HPA02/53 to Inside:192.168.12.10/64374 duration 0:00:00 bytes 0
6|Jan 23 2012|18:20:05|302015|FTP_Server|53|192.168.12.10|62344|Built inbound UDP connection 27965 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/62344 (192.168.12.10/62344)
6|Jan 23 2012|18:20:05|302016|HPA02|53|192.168.13.178|61975|Teardown UDP connection 27963 for Inside:HPA02/53 to Inside:192.168.13.178/61975 duration 0:00:00 bytes 0
This setup used to works perfectly on my old firewall (Watchguard) but I cant seem to figure out what is happening here (I am migrating away from the watchguard to the cisco).
The routing between my 6.0/23 and the 8.0/24 works perfectly, as does the internet in and out.
Any help is appreciated.
Thanks!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:38 AM
Hello Peter,
It looks like a TCP stateful inspection problem.
Lets do a TCP state by pass rule and see if that fix it ( I think it will do it)
access-list tcp_bypass permit tcp 192.168.12.0 255.255.255.0 192.168.6.0 255.255.254.0
class-map tcp_bypass
match access-list tcp_bypass
policy-map tcp_bypass
class tcp_bypass
set connection advanced-options tcp-state-bypass
service-policy tcp_bypass interface inside
Let me know the result!
Julio
Rate helpful posts!
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 03:49 PM
The show asp drop frame command can identify the number of DNS packets that the DNS guard function (with the counter name inspect-dns-id-not-matched ) has dropped because the transaction ID in the DNS response message does not match any transaction IDs for DNS queries that have passed across the firewall earlier on the same connection. As shown in the following example, the counter inspect-dns-id-not-matched is represented in the command output as DNS Inspect id not matched.
So in this case I think we are having the same problem, the thing is that the TCP state by pass as its name says its only for TCP, so the only thing I can see here is to disable inspection for DNS.
Please give it a try to this and let me know:
policy-map global_policy
class inspection_default
no inspect dns preset_dns_map
Regards,
Do rate all the helpful posts!!
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 07:16 AM
I am going to quickly add that I built the ASAs configuration in ASDM, I am not affraid to use the console though
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 07:28 AM
Which one will be route for 12.0/24 ?
Cant find
name 192.168.7.26 Spam_Firewall
name 192.168.12.0 xxxSt_VideoSec description xxx St Video/Security
name 192.168.8.0 Phone_System-network description Phone System
name 192.168.6.0 Inside-network description Main Network
name 192.168.11.0 EnduraSM-network description Endura System Manager
name 192.168.15.0 Data-network1 description Data1
name 192.168.13.0 Video-network1 description Video/Security1
name 192.168.16.0 Data-network2 description Data2
name 192.168.14.0 Video-network2 description Video/Security2
name 192.168.7.11 FTP_Server description FTP Server
name 192.168.7.17 Mail_Server
name 192.168.6.1 yyy description yyy
name 192.168.6.2 zzz description zzz
name 192.168.7.12 HPA02
Thanks
Ajay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 07:39 AM
I buggered up my censoring. Its this one to get to 0.12/24
name 192.168.12.0 xxxSt_VideoSec description xxx St Video/Security
route Inside MainOffice_VideoSec 255.255.255.0 192.168.7.29 1
name 192.168.12.0 xxxSt_VideoSec description xxx St Video/Security should have read:
name 192.168.12.0 MainOffice_VideoSec description xxx St Video/Security (And it does on the firewall).
The routes are all correct (from what I can tell) as I can ping the hosts on the other network and get a ping reply. But as soon as there is a handshake, the firewall drops the connection (or is having it dropped).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 07:43 AM
I am going to add, it doesn't just do this on the 12.0/24, it does it on all the networks connected to the second router (there are a few more then in the drawing).
It does it on 0.11/24, 0.12/24, 0.13/24, 0.14/24, 0.15/24 and 0.16/24.
I dont know why the ASA would tear down the connection like that. I tried adding a rule to allow any to any (all tcp and ip) on the internal interface but it didn't help.
Would these routes get passed to the firwall side of things?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:23 AM
Thinking about this problem more,
Could this be happening because the other router (HP5300xl) is routing the data back onto the 6.0/23 network itself and not passing it to the ASA to be "put back" onto the network.
In other words, When my packets go out they travel like this:
Client (6.0/23) --> ASA Router (7.20) --> HP Router (7.29) --> Destination (12.0/24)
When they come back in, they take this route as the HP knows about the 6.0/23 network:
Destination (12.0/24) --> HP Router (12.254/24) --> Client (6.0/23)
Would the ASA box not seeing this cause it to bugger up? Does anyone think the problem might be solved my putting a static route on the HP to the 6.0/23 network pointing to the ASA to have the ASA forward it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:33 AM
Yeah you can check the route on router return traffic should also go via ASA 7.20 .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:38 AM
Hello Peter,
It looks like a TCP stateful inspection problem.
Lets do a TCP state by pass rule and see if that fix it ( I think it will do it)
access-list tcp_bypass permit tcp 192.168.12.0 255.255.255.0 192.168.6.0 255.255.254.0
class-map tcp_bypass
match access-list tcp_bypass
policy-map tcp_bypass
class tcp_bypass
set connection advanced-options tcp-state-bypass
service-policy tcp_bypass interface inside
Let me know the result!
Julio
Rate helpful posts!
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:45 AM
Hi Julio,
Its a question
Looking at the diagram what will be the condition to implement Inspection bypass ?
If both way traffic passes via ASA stiil needed ?
Thanks
Ajay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:52 AM
Hello Ajay,
The problem is that when the hosts on the other side of the router reply the message will be send to their default gateway, then the router will know the packet is going to a host on the 192.168.7.x network witch is directly connected to it so he will send it to the host without going to the ASA.
The ASA will receive a SYN ACK without the ACK and it will drop the packet.
That is what I have understood on this network diagram.
Hope this helps,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:46 AM
I tried adding a static route to the ASA from the HP router/switch and since it knows about the 6.0/23 interface it just dumps it onto the network and doesn't forward it (not surprised, tested via a traceroute on both sides).
I will try the state bypass rule tonight (I have to put the ASA back into production to try this) and let everyone know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 09:52 AM
Hello Peter,
Yeap, lets give it a try and let us know the result.
Regards,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 02:46 PM
Julio, your suggestion worked but we are only half way there. I modified the rule to include all my networks on the second router. I am now getting some strange issue where UDP connections are being torn down from the external network:
6|Jan 24 2012|17:33:15|302016|HPA02|53|192.168.13.178|60231|Teardown UDP connection 37876 for Inside:HPA02/53 to Inside:192.168.13.178/60231 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:15|302016|FTP_Server|53|192.168.13.178|60231|Teardown UDP connection 37875 for Inside:FTP_Server/53 to Inside:192.168.13.178/60231 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:14|302015|HPA02|53|192.168.13.178|60231|Built inbound UDP connection 37876 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.13.178/60231 (192.168.13.178/60231)
6|Jan 24 2012|17:33:14|302015|FTP_Server|53|192.168.13.178|60231|Built inbound UDP connection 37875 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.178/60231 (192.168.13.178/60231)
6|Jan 24 2012|17:33:13|302016|HPA02|53|192.168.12.10|53412|Teardown UDP connection 37874 for Inside:HPA02/53 to Inside:192.168.12.10/53412 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:13|302016|FTP_Server|53|192.168.12.10|53412|Teardown UDP connection 37873 for Inside:FTP_Server/53 to Inside:192.168.12.10/53412 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:12|302015|HPA02|53|192.168.12.10|53412|Built inbound UDP connection 37874 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/53412 (192.168.12.10/53412)
6|Jan 24 2012|17:33:12|302015|FTP_Server|53|192.168.12.10|53412|Built inbound UDP connection 37873 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/53412 (192.168.12.10/53412)
6|Jan 24 2012|17:33:12|302016|HPA02|53|192.168.12.10|62883|Teardown UDP connection 37872 for Inside:HPA02/53 to Inside:192.168.12.10/62883 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:12|302016|FTP_Server|53|192.168.12.10|62883|Teardown UDP connection 37871 for Inside:FTP_Server/53 to Inside:192.168.12.10/62883 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:12|302015|HPA02|53|192.168.12.10|62883|Built inbound UDP connection 37872 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/62883 (192.168.12.10/62883)
6|Jan 24 2012|17:33:12|302015|FTP_Server|53|192.168.12.10|62883|Built inbound UDP connection 37871 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/62883 (192.168.12.10/62883)
6|Jan 24 2012|17:33:11|302016|HPA02|53|192.168.13.178|60231|Teardown UDP connection 37870 for Inside:HPA02/53 to Inside:192.168.13.178/60231 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:11|302016|FTP_Server|53|192.168.13.178|60231|Teardown UDP connection 37869 for Inside:FTP_Server/53 to Inside:192.168.13.178/60231 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:10|302015|HPA02|53|192.168.13.178|60231|Built inbound UDP connection 37870 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.13.178/60231 (192.168.13.178/60231)
6|Jan 24 2012|17:33:10|302015|FTP_Server|53|192.168.13.178|60231|Built inbound UDP connection 37869 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.178/60231 (192.168.13.178/60231)
6|Jan 24 2012|17:33:09|302016|FTP_Server|53|192.168.13.178|60231|Teardown UDP connection 37868 for Inside:FTP_Server/53 to Inside:192.168.13.178/60231 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:09|302016|HPA02|53|192.168.12.10|53412|Teardown UDP connection 37867 for Inside:HPA02/53 to Inside:192.168.12.10/53412 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:09|302016|FTP_Server|53|192.168.12.10|53412|Teardown UDP connection 37866 for Inside:FTP_Server/53 to Inside:192.168.12.10/53412 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:08|302016|HPA02|53|192.168.12.10|54311|Teardown UDP connection 37865 for Inside:HPA02/53 to Inside:192.168.12.10/54311 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:08|302016|FTP_Server|53|192.168.12.10|54311|Teardown UDP connection 37864 for Inside:FTP_Server/53 to Inside:192.168.12.10/54311 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:08|302015|FTP_Server|53|192.168.13.178|60231|Built inbound UDP connection 37868 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.13.178/60231 (192.168.13.178/60231)
6|Jan 24 2012|17:33:08|302015|HPA02|53|192.168.12.10|53412|Built inbound UDP connection 37867 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/53412 (192.168.12.10/53412)
6|Jan 24 2012|17:33:08|302015|FTP_Server|53|192.168.12.10|53412|Built inbound UDP connection 37866 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/53412 (192.168.12.10/53412)
6|Jan 24 2012|17:33:08|302016|HPA02|53|192.168.12.10|62883|Teardown UDP connection 37863 for Inside:HPA02/53 to Inside:192.168.12.10/62883 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:08|302016|FTP_Server|53|192.168.12.10|62883|Teardown UDP connection 37862 for Inside:FTP_Server/53 to Inside:192.168.12.10/62883 duration 0:00:00 bytes 0
6|Jan 24 2012|17:33:08|302015|HPA02|53|192.168.12.10|54311|Built inbound UDP connection 37865 for Inside:HPA02/53 (HPA02/53) to Inside:192.168.12.10/54311 (192.168.12.10/54311)
6|Jan 24 2012|17:33:08|302015|FTP_Server|53|192.168.12.10|54311|Built inbound UDP connection 37864 for Inside:FTP_Server/53 (FTP_Server/53) to Inside:192.168.12.10/54311 (192.168.12.10/54311)
6|Jan 24 2012|17:33:08|302016|HPA02|53|192.168.12.10|54447|Teardown UDP connection 37861 for Inside:HPA02/53 to Inside:192.168.12.10/54447 duration 0:00:00 bytes 0
FTP_Server is my primary DNS server and HPA02 is my secondary. My guess is the requests are hitting me but not being returned...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 03:04 PM
Hello Peter,
You were not receiving those logs before right??
capture asp type asp-drop all
Provide the following:
sh capture asp | include 192.168.7.11
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2012 03:15 PM
I was getting them before as well (the partial log is in my first post).
Here is the result of the log you requested:
10: 18:13:13.970637 192.168.7.11.53 > 192.168.12.10.60709: udp 55
11: 18:13:14.500889 192.168.7.11.53 > 192.168.12.10.62242: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
16: 18:13:16.043134 192.168.7.11.53 > 192.168.15.101.50317: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
20: 18:13:16.996957 192.168.7.11.53 > 192.168.12.10.60709: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
25: 18:13:18.518222 192.168.7.11.53 > 192.168.12.10.62242: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
28: 18:13:19.043042 192.168.7.11.53 > 192.168.15.101.50317: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
30: 18:13:21.006408 192.168.7.11.53 > 192.168.12.10.60709: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
36: 18:13:23.043058 192.168.7.11.53 > 192.168.15.101.50317: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
44: 18:13:26.138878 192.168.7.11.53 > 192.168.12.10.59729: udp 55
49: 18:13:29.165396 192.168.7.11.53 > 192.168.12.10.59729: udp 55 Drop-reason: (inspect-dns-id-not-matched) DNS Inspect id not matched
52: 18:13:30.592986 192.168.7.11.53 > 192.168.15.101.56902: udp 55
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
