- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5510 v.7 portmap creation failed for tcp src
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5510 v.7 portmap creation failed for tcp src
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2011
12:11 PM
- last edited on
03-25-2019
05:47 PM
by
ciscomoderator
![]()
Hello,
Spent many hours serching and unable to find answer that fits senario.
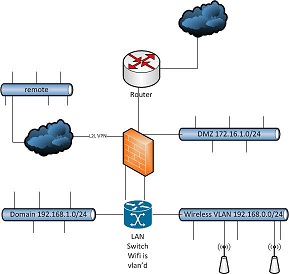
I have tried several ways to skin this cat but I always get either "portmap creation failed", "deny due to DDNS query" or "no translation group found".
The way it is currently configured it seems to almost work but when I try to connect, say to www.google.com, from the Wireless Lan (wlan) I get an error like:
3|Oct 07 2011 13:03:48|305006: portmap translation creation failed for tcp src wlan:192.168.0.16/57203 dst outside:74.125.73.104/80
Here is my config:
ASA Version 7.0(8)
!
names
no dns-guard
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 66.xx.xx.244 255.255.255.128
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
!
interface Ethernet0/2
nameif dmz
security-level 50
ip address 172.16.1.254 255.255.255.0
!
interface Ethernet0/3
description Wireless Network
nameif wlan
security-level 100
ip address 192.168.0.254 255.255.255.0
!
interface Management0/0
description LAN/STATE Failover Interface
speed 100
duplex full
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_acl extended permit ip host 199.204.136.252 192.168.1.0 255.255.255.0
access-list outside_acl extended permit ip host 199.204.136.140 192.168.1.0 255.255.255.0
access-list outside_acl extended permit ip host 199.204.136.157 192.168.1.0 255.255.255.0
access-list outside_acl extended permit tcp any host 66.xx.xx.230 eq smtp
access-list outside_acl remark DMZ incomming HTTP
access-list outside_acl extended permit tcp any any eq www
access-list outside_acl extended permit tcp any host 66.xx.xx.243 eq domain
access-list outside_acl extended permit udp any host 66.xx.xx.243 eq domain
access-list dns extended permit udp any eq domain any
access-list dns extended permit udp any any eq domain
access-list dns extended permit tcp any any eq domain
access-list wlan_access_in extended permit udp any any eq domain
access-list wlan_access_in extended permit tcp any any eq domain
access-list wlan_access_in extended permit tcp any any eq 9005
access-list wlan_access_in extended permit tcp any any eq www
access-list wlan_access_in extended permit tcp any any eq https
access-list wlan_access_in extended permit udp any any eq ntp
access-list outside_access_out remark inside allow http out
access-list outside_access_out extended permit tcp any any eq www
access-list outside_access_out extended permit tcp any any eq https
access-list outside_access_out extended permit udp any any eq domain
access-list outside_access_out extended permit tcp any any eq domain
access-list outside_access_out extended permit tcp any any eq smtp
access-list outside_access_out extended permit tcp any any eq ssh
access-list outside_access_out extended permit tcp any any eq ftp
access-list outside_access_out remark Wireless Internet
access-list outside_access_out extended permit ip any any
access-list wlan_nat0_inbound extended deny ip any any
access-list inside_access_in extended permit tcp any any eq www
access-list inside_access_in extended permit tcp any any eq https
access-list inside_access_in extended permit tcp any any eq domain
access-list inside_access_in extended permit udp any any eq domain
access-list inside_access_in extended permit tcp any any eq smtp
access-list inside_access_in extended permit tcp any any eq ssh
access-list inside_access_in extended permit tcp any any eq ftp
access-list inside_pnat_outbound extended permit ip any any
access-list wlan_pnat_outbound extended permit ip any any
access-list wlan_nat0_outbound extended permit ip 192.168.0.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list wlan_pnat_outbound_V1 extended permit ip any any
pager lines 15
logging enable
logging buffered debugging
logging trap debugging
logging asdm informational
logging facility 23
logging host inside 192.168.1.121
logging permit-hostdown
no logging message 305012
no logging message 305011
no logging message 710005
no logging message 302015
no logging message 302014
no logging message 302013
no logging message 304001
no logging message 609001
no logging message 302016
mtu outside 1500
mtu inside 1500
mtu dmz 1500
mtu wlan 1500
ip local pool Remote 192.168.194.1-192.168.194.254
failover
failover lan unit primary
failover lan interface FAILOVER Management0/0
failover link FAILOVER Management0/0
failover interface ip FAILOVER 10.1.253.254 255.255.255.252 standby 10.1.253.253
monitor-interface outside
monitor-interface inside
monitor-interface dmz
no monitor-interface wlan
asdm image disk0:/asdm-508.bin
asdm location 192.168.1.99 255.255.255.255 inside
asdm history enable
arp timeout 14400
global (outside) 1 interface
global (outside) 4 66.xx.xx.242
global (inside) 2 interface
global (wlan) 3 interface
nat (inside) 0 access-list no-nat
nat (inside) 1 access-list inside_pnat_outbound
nat (wlan) 0 access-list wlan_nat0_outbound
nat (wlan) 0 access-list wlan_nat0_inbound outside
nat (wlan) 2 access-list wlan_pnat_outbound
nat (wlan) 4 access-list wlan_pnat_outbound_V1 dns
static (inside,outside) 66.xx.xx.131 192.168.1.3 netmask 255.255.255.255
static (inside,outside) 66.xx.xx.132 192.168.1.10 netmask 255.255.255.255
static (inside,wlan) 192.168.0.200 192.168.1.3 netmask 255.255.255.255
static (inside,wlan) 192.168.0.201 192.168.1.10 netmask 255.255.255.255
access-group outside_acl in interface outside
access-group outside_access_out out interface outside
access-group inside_access_in in interface inside
access-group wlan_access_in in interface wlan
route outside 0.0.0.0 0.0.0.0 66.xx.xx.129 1
timeout xlate 0:05:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00
timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
service resetinbound
telnet 192.168.1.0 255.255.255.0 inside
telnet timeout 5
ssh 192.168.1.0 255.255.255.0 inside
ssh timeout 60
console timeout 0
dhcpd address 192.168.0.1-192.168.0.51 wlan
dhcpd dns 192.168.0.200 192.168.0.201
dhcpd lease 3600
dhcpd ping_timeout 50
dhcpd domain domain.local
dhcpd auto_config wlan
dhcpd enable wlan
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect dns maximum-length 512
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
Thanks for any assist.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2011 09:32 AM
Hello Jesse,
That is great, any other question just let us know.
Have a great day,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
