- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5510 v.7 portmap creation failed for tcp src
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5510 v.7 portmap creation failed for tcp src
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2011
12:11 PM
- last edited on
03-25-2019
05:47 PM
by
ciscomoderator
![]()
Hello,
Spent many hours serching and unable to find answer that fits senario.
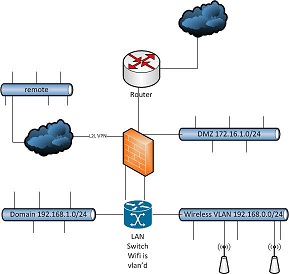
I have tried several ways to skin this cat but I always get either "portmap creation failed", "deny due to DDNS query" or "no translation group found".
The way it is currently configured it seems to almost work but when I try to connect, say to www.google.com, from the Wireless Lan (wlan) I get an error like:
3|Oct 07 2011 13:03:48|305006: portmap translation creation failed for tcp src wlan:192.168.0.16/57203 dst outside:74.125.73.104/80
Here is my config:
ASA Version 7.0(8)
!
names
no dns-guard
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 66.xx.xx.244 255.255.255.128
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
!
interface Ethernet0/2
nameif dmz
security-level 50
ip address 172.16.1.254 255.255.255.0
!
interface Ethernet0/3
description Wireless Network
nameif wlan
security-level 100
ip address 192.168.0.254 255.255.255.0
!
interface Management0/0
description LAN/STATE Failover Interface
speed 100
duplex full
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_acl extended permit ip host 199.204.136.252 192.168.1.0 255.255.255.0
access-list outside_acl extended permit ip host 199.204.136.140 192.168.1.0 255.255.255.0
access-list outside_acl extended permit ip host 199.204.136.157 192.168.1.0 255.255.255.0
access-list outside_acl extended permit tcp any host 66.xx.xx.230 eq smtp
access-list outside_acl remark DMZ incomming HTTP
access-list outside_acl extended permit tcp any any eq www
access-list outside_acl extended permit tcp any host 66.xx.xx.243 eq domain
access-list outside_acl extended permit udp any host 66.xx.xx.243 eq domain
access-list dns extended permit udp any eq domain any
access-list dns extended permit udp any any eq domain
access-list dns extended permit tcp any any eq domain
access-list wlan_access_in extended permit udp any any eq domain
access-list wlan_access_in extended permit tcp any any eq domain
access-list wlan_access_in extended permit tcp any any eq 9005
access-list wlan_access_in extended permit tcp any any eq www
access-list wlan_access_in extended permit tcp any any eq https
access-list wlan_access_in extended permit udp any any eq ntp
access-list outside_access_out remark inside allow http out
access-list outside_access_out extended permit tcp any any eq www
access-list outside_access_out extended permit tcp any any eq https
access-list outside_access_out extended permit udp any any eq domain
access-list outside_access_out extended permit tcp any any eq domain
access-list outside_access_out extended permit tcp any any eq smtp
access-list outside_access_out extended permit tcp any any eq ssh
access-list outside_access_out extended permit tcp any any eq ftp
access-list outside_access_out remark Wireless Internet
access-list outside_access_out extended permit ip any any
access-list wlan_nat0_inbound extended deny ip any any
access-list inside_access_in extended permit tcp any any eq www
access-list inside_access_in extended permit tcp any any eq https
access-list inside_access_in extended permit tcp any any eq domain
access-list inside_access_in extended permit udp any any eq domain
access-list inside_access_in extended permit tcp any any eq smtp
access-list inside_access_in extended permit tcp any any eq ssh
access-list inside_access_in extended permit tcp any any eq ftp
access-list inside_pnat_outbound extended permit ip any any
access-list wlan_pnat_outbound extended permit ip any any
access-list wlan_nat0_outbound extended permit ip 192.168.0.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list wlan_pnat_outbound_V1 extended permit ip any any
pager lines 15
logging enable
logging buffered debugging
logging trap debugging
logging asdm informational
logging facility 23
logging host inside 192.168.1.121
logging permit-hostdown
no logging message 305012
no logging message 305011
no logging message 710005
no logging message 302015
no logging message 302014
no logging message 302013
no logging message 304001
no logging message 609001
no logging message 302016
mtu outside 1500
mtu inside 1500
mtu dmz 1500
mtu wlan 1500
ip local pool Remote 192.168.194.1-192.168.194.254
failover
failover lan unit primary
failover lan interface FAILOVER Management0/0
failover link FAILOVER Management0/0
failover interface ip FAILOVER 10.1.253.254 255.255.255.252 standby 10.1.253.253
monitor-interface outside
monitor-interface inside
monitor-interface dmz
no monitor-interface wlan
asdm image disk0:/asdm-508.bin
asdm location 192.168.1.99 255.255.255.255 inside
asdm history enable
arp timeout 14400
global (outside) 1 interface
global (outside) 4 66.xx.xx.242
global (inside) 2 interface
global (wlan) 3 interface
nat (inside) 0 access-list no-nat
nat (inside) 1 access-list inside_pnat_outbound
nat (wlan) 0 access-list wlan_nat0_outbound
nat (wlan) 0 access-list wlan_nat0_inbound outside
nat (wlan) 2 access-list wlan_pnat_outbound
nat (wlan) 4 access-list wlan_pnat_outbound_V1 dns
static (inside,outside) 66.xx.xx.131 192.168.1.3 netmask 255.255.255.255
static (inside,outside) 66.xx.xx.132 192.168.1.10 netmask 255.255.255.255
static (inside,wlan) 192.168.0.200 192.168.1.3 netmask 255.255.255.255
static (inside,wlan) 192.168.0.201 192.168.1.10 netmask 255.255.255.255
access-group outside_acl in interface outside
access-group outside_access_out out interface outside
access-group inside_access_in in interface inside
access-group wlan_access_in in interface wlan
route outside 0.0.0.0 0.0.0.0 66.xx.xx.129 1
timeout xlate 0:05:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00
timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
service resetinbound
telnet 192.168.1.0 255.255.255.0 inside
telnet timeout 5
ssh 192.168.1.0 255.255.255.0 inside
ssh timeout 60
console timeout 0
dhcpd address 192.168.0.1-192.168.0.51 wlan
dhcpd dns 192.168.0.200 192.168.0.201
dhcpd lease 3600
dhcpd ping_timeout 50
dhcpd domain domain.local
dhcpd auto_config wlan
dhcpd enable wlan
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect dns maximum-length 512
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
Thanks for any assist.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2011 05:58 PM
Hello Netjess,
Can you run this command and gives us the output
Packet-tracer input Wlan tcp 192.168.1.5 1025 4.2.2.2 80
And by the way what is the purpose of these lines,
access-list wlan_nat0_inbound extended deny ip any any
nat (wlan) 0 access-list wlan_nat0_outbound
Please provide us this information.
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-07-2011 06:56 PM
This has already been fixed. I'l post the working config later.
Now I just need to figure out why it is so slow. I think it could be a physical layer issue.
The lines you are asking about were automaticaly generated from the ASDM. That's also the cause of a lot of redunant rules.
I fixed it by getting a command line and starting over.
Thanks for your attention.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2011 10:07 AM
You didn't elaborate on what flow is slow.
1. source and dest interfaces
2. protocol
Pls. refer this link and use it as your check list:
https://supportforums.cisco.com/docs/DOC-8982
-Kureli
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2011 01:56 PM
Hello Jesse,
That is why there are sometimes where you would like to use the CLI instead of the ASDM.
Please let us know the resolution of this, and also mark the question as answered you anyone having the same issue can take a llook at this.
Have a great weekend,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 05:10 PM
@Sankar While your URL was good information it doesn't address my current issue, but thanks.
Now I am not sure what I did but last week when I quit working on this I had loaded a web page but it took very long.
Today I cam in a started checking some things. I tried taking the switch/vlan out of the mix and connected my wlan ap directly to the line that goes to the ASA.That did not work. I could ping the AP and the ASA wlan interface but no further. I plugged the ASA and the AP back into the switch.
I went back to the basics of my config.
I made sure I had a NAT and corresponding rules for DNS and ICMP. I also have an NAT Exempt rule for inside outbound to wlan.
I have also test the configuration bypassing the AP by plugging in a laptop directly to the switch/vlan and I could again ping the AP and the wlan interface of the ASA but no further. I could also not get a DNS reply even though I have a translation rule for the DNS servers. This ASA is also the default route for our LAN so should not be a routing issue since ASA is aware of all the networks concerned.
Here is my current config:
ASA Version 7.0(8)
!
names
no dns-guard
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 66.xxx.xxx.244 255.255.255.128
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
!
interface Ethernet0/2
nameif dmz
security-level 50
ip address 172.16.1.254 255.255.255.0
!
interface Ethernet0/3
description Wireless Network
nameif wlan
security-level 75
ip address 192.168.0.254 255.255.255.0
!
interface Management0/0
description LAN/STATE Failover Interface
speed 100
duplex full
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_acl extended permit icmp interface outside host 66.xxx.xxx.132
access-list outside_acl remark testing wlan
access-list outside_acl extended permit icmp any host 66.xxx.xxx.242
access-list outside_acl extended permit tcp any host 66.xxx.xxx.243 eq smtp
access-list outside_acl extended permit tcp any host 66.xxx.xxx.243 eq www
access-list outside_acl extended permit tcp any host 66.xxx.xxx.243 eq https
access-list outside_acl extended permit tcp any host 66.xxx.xxx.243 eq domain
access-list outside_acl extended permit udp any host 66.xxx.xxx.243 eq domain
access-list no-nat extended permit ip 192.168.1.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list no-nat extended permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0
access-list dns extended permit udp any eq domain any
access-list dns extended permit udp any any eq domain
access-list dns extended permit tcp any any eq domain
access-list wlan_access_in extended permit ip any any
access-list wlan_access_in extended permit icmp any any
access-list outside_access_out remark inside allow http out
access-list outside_access_out extended permit tcp any any eq www
access-list outside_access_out extended permit tcp any any eq https
access-list outside_access_out extended permit udp any any eq domain
access-list outside_access_out extended permit tcp any any eq domain
access-list outside_access_out remark Wireless Internet
access-list outside_access_out extended permit ip any any
access-list inside_pnat_outbound extended permit ip any any
access-list inside_access_in extended permit tcp any any eq www
access-list inside_access_in extended permit tcp any any eq https
access-list inside_access_in remark DNS tcp COX forward
access-list inside_access_in extended permit tcp host 192.168.1.3 host 68.12.16.25 eq domain
access-list inside_access_in remark DNS tcp COX forward
access-list inside_access_in extended permit tcp host 192.168.1.10 host 68.12.16.25 eq domain
access-list inside_access_in remark DNS tcp COX forward
access-list inside_access_in extended permit tcp host 192.168.1.3 host 68.12.16.30 eq domain
access-list inside_access_in remark DNS tcp COX forward
access-list inside_access_in extended permit tcp host 192.168.1.10 host 68.12.16.30 eq domain
access-list inside_access_in remark DNS udp COX forward
access-list inside_access_in extended permit udp host 192.168.1.3 host 68.12.16.25 eq domain
access-list inside_access_in remark DNS udp COX forward
access-list inside_access_in extended permit udp host 192.168.1.10 host 68.12.16.25 eq domain
access-list inside_access_in remark DNS udp COX forward
access-list inside_access_in extended permit udp host 192.168.1.3 host 68.12.16.30 eq domain
access-list inside_access_in remark DNS udp COX forward
access-list inside_access_in extended permit udp host 192.168.1.10 host 68.12.16.30 eq domain
access-list inside_access_in remark wlan DNS tcp
access-list inside_access_in extended permit tcp host 192.168.1.3 192.168.0.0 255.255.255.0 eq domain
access-list inside_access_in remark wlan DNS tcp
access-list inside_access_in extended permit tcp host 192.168.1.10 192.168.0.0 255.255.255.0 eq domain
access-list inside_access_in remark wlan DNS udp
access-list inside_access_in extended permit udp host 192.168.1.3 192.168.0.0 255.255.255.0 eq domain
access-list inside_access_in remark wlan DNS udp
access-list inside_access_in extended permit udp host 192.168.1.10 192.168.0.0 255.255.255.0 eq domain
access-list inside_access_in extended permit tcp any any eq smtp
access-list inside_access_in remark testing from wlan
access-list inside_access_in extended permit icmp any 192.168.0.0 255.255.255.0
access-list dmz_access_in extended permit tcp any any eq www
access-list dmz_access_in extended permit tcp any any eq https
access-list dmz_access_in extended permit tcp any any eq smtp
pager lines 15
logging enable
logging buffered debugging
logging trap debugging
logging asdm informational
logging facility 23
logging host inside 192.168.1.121
logging permit-hostdown
no logging message 305012
no logging message 305011
no logging message 710005
no logging message 302015
no logging message 302014
no logging message 302013
no logging message 304001
no logging message 609001
no logging message 302016
mtu outside 1500
mtu inside 1500
mtu dmz 1500
mtu wlan 1500
failover
failover lan unit primary
failover lan interface FAILOVER Management0/0
failover link FAILOVER Management0/0
failover interface ip FAILOVER 10.1.253.254 255.255.255.252 standby 10.1.253.253
monitor-interface outside
monitor-interface inside
monitor-interface dmz
no monitor-interface wlan
arp timeout 14400
nat-control
global (outside) 1 interface
global (outside) 2 66.xxx.xxx.241
global (outside) 3 66.xxx.xxx.242
nat (inside) 0 access-list no-nat
nat (inside) 1 access-list inside_pnat_outbound
nat (dmz) 2 172.16.1.0 255.255.255.0
nat (wlan) 3 192.168.0.0 255.255.255.0
static (inside,outside) 66.xxx.xxx.131 192.168.1.3 netmask 255.255.255.255
static (inside,outside) 66.xxx.xxx.132 192.168.1.10 netmask 255.255.255.255
static (inside,wlan) 192.168.0.200 192.168.1.3 netmask 255.255.255.255
static (inside,wlan) 192.168.0.201 192.168.1.10 netmask 255.255.255.255
access-group outside_acl in interface outside
access-group outside_access_out out interface outside
access-group inside_access_in in interface inside
access-group dmz_access_in in interface dmz
access-group wlan_access_in in interface wlan
route outside 0.0.0.0 0.0.0.0 66.xxx.xxx.129 1
timeout xlate 0:05:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00
timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect dns maximum-length 512
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
I appreciate your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 05:17 PM
BTW, Part of my hurdle and the whole reason I am trying to set it up this way is to secure the wireless access to the LAN but still be able to control access to LAN resources from wireless when needed.
If you notice I change the security level of the wlan to 75 to protect the LAN and that is also why I made a NAT for the DNS servers to the wlan.
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 05:37 PM
Hello Jesse,
So at this point everything seems to be ok, the Wlan has a lower security level than the inside., you have created the Nat statements and the ACLs required to allow the comunication between these two interfaces.
On the outside interface you have two different ACLs, one applied on the inbound direction and the other one outbound.They do not block the connections created by the Wlan users. I would use just one ACL on the Outside interface ( Inbound direction).
Now regarding why the connections are slow, are the connections on the DMZ zone as slow as the ones being generated on the Wlan?
Regards,
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 05:44 PM
@ jcarvaja
I am unable to run the packet-tracer command. My ASA v7.0(8) returns "Invalid input". If I issue a ? it is not in the command list. Only ping but here is what I get from that:
PrimaryASA5510# ping inside 192.168.1.3 size 1024
Sending 5, 1024-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
There does seem to be some latency from my AP (0.253)
PrimaryASA5510# ping wlan 192.168.0.253 size 1024
Sending 5, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!?!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024
Sending 5, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!??
Success rate is 60 percent (3/5), round-trip min/avg/max = 1/1/1 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024
Sending 5, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
?!??!
Success rate is 40 percent (2/5), round-trip min/avg/max = 1/1/1 ms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 05:48 PM
Hello Jesse,
Correct there seems to be an issue with the Wlan interface.
Can you share the output of the
Show interface Ethernet 0/3
Also place the following command on the ASA
Debug icmp trace
And finally ping from the Wlan computer to the ASA and share the debug.
Regards,
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 06:26 PM
I posted about results from my phone before I realized you had updated your assistance.
I eliminated some of the latency by removing the Dell 3548 switch that I had vlan'd a few ports for the wireless and connected a small 8 port 10/100 switch.
PrimaryASA5510# sh int eth0/3
Interface Ethernet0/3 "wlan", is up, line protocol is up
Hardware is i82546GB rev03, BW 100 Mbps
Auto-Duplex(Full-duplex), Auto-Speed(100 Mbps)
Description: Wireless Network
MAC address 0024.1413.7d95, MTU 1500
IP address 192.168.0.254, subnet mask 255.255.255.0
38239417 packets input, 3647292409 bytes, 0 no buffer
Received 9167 broadcasts, 0 runts, 0 giants
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 L2 decode drops
188086570 packets output, 99110793673 bytes, 1247 underruns
0 output errors, 0 collisions, 89 interface resets
0 late collisions, 0 deferred
0 input reset drops, 0 output reset drops
input queue (curr/max packets): hardware (4/9)
output queue (curr/max packets): hardware (0/1)
Traffic Statistics for "wlan":
63766 packets input, 5205778 bytes
47556 packets output, 26495681 bytes
31130 packets dropped
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 20 bytes/sec
5 minute output rate 0 pkts/sec, 3 bytes/sec
5 minute drop rate, 0 pkts/sec
Some pings:
PrimaryASA5510# ping wlan 192.168.0.253 size 1024 repeat 20
Sending 20, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!!!!!!!!!!!!?!!!!?
Success rate is 90 percent (18/20), round-trip min/avg/max = 1/2/10 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024 repeat 20
Sending 20, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!!!!!!!!!?!!!!!!!!
Success rate is 95 percent (19/20), round-trip min/avg/max = 1/1/1 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024 repeat 20
Sending 20, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (20/20), round-trip min/avg/max = 1/1/10 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024 repeat 20
Sending 20, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (20/20), round-trip min/avg/max = 1/1/10 ms
PrimaryASA5510# ping wlan 192.168.0.253 size 1024 repeat 20
Sending 20, 1024-byte ICMP Echos to 192.168.0.253, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (20/20), round-trip min/avg/max = 1/1/10 ms
Debug ICMP:
PrimaryASA5510# debug icmp trace (across wireless connection)
debug icmp trace enabled at level 1
PrimaryASA5510# ICMP echo request from 192.168.1.2 to 192.168.1.254 ID=512 seq=57578 len=32
ICMP echo reply from 192.168.1.254 to 192.168.1.2 ID=512 seq=57578 len=32
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=12544 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=12544 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=12800 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=12800 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=13056 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=13056 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=13312 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=13312 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=13568 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=13568 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=13824 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=13824 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=14080 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=14080 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=14336 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=14336 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=14592 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=14592 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=14848 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=14848 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=15104 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=15104 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=15360 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=15360 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=15616 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=15616 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=15872 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=15872 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=16128 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=16128 len=1024
ICMP echo request from 192.168.0.37 to 192.168.0.254 ID=768 seq=16384 len=1024
ICMP echo reply from 192.168.0.254 to 192.168.0.37 ID=768 seq=16384 len=1024
ICMP echo request from 192.168.1.2 to 192.168.1.254 ID=512 seq=58090 len=32
ICMP echo reply from 192.168.1.254 to 192.168.1.2 ID=512 seq=58090 len=32
Thanks again for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 06:18 PM
From my Android phone I can ping all the way to 192.168.0.254 (ASA wlan interface) but I cannot get a reply from 192.168.1.254 (ASA inside interface) or any other inside network address.
I also tried with a laptop connected to wireless network and same result when both wired and wireless to wlan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 06:37 PM
OK, So going through all of this It seems somehoe the culprit is my Dell 3548 switch. Either a problem with the switch or a problem with the ports.
Without changing anything since my last config post only changing to the littel switch and rebooting the AP I can ping the DNS server and pull web pages.
Thanks for the sounding board. It helps just bouncing your progress and not feel like your just talking to yourself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2011 09:01 PM
Hello Jesse,
I just got home, sorry I could not answer bedore.
Just to let you know you cannot ping a distant interface, as a security box the ASA is not going to allow you to ping from one host behind one interface to another interface, this as a security meassure.
The good thing is that you are able to go to the internet from the Wlan right?
Hope you are doing great.
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2011 06:20 AM
Yes I can reach the Internet from my wlan and recieve DNS from my inside lan. This is what I was trying to do.
Thanks.
I also removed the redundant outside outbound acl as you suggested.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

