- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA 5512 Dual Homed and Failure Notification
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5512 Dual Homed and Failure Notification
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2018 01:37 PM - edited 02-21-2020 08:19 AM
Hi everyone! Here is my quetions:
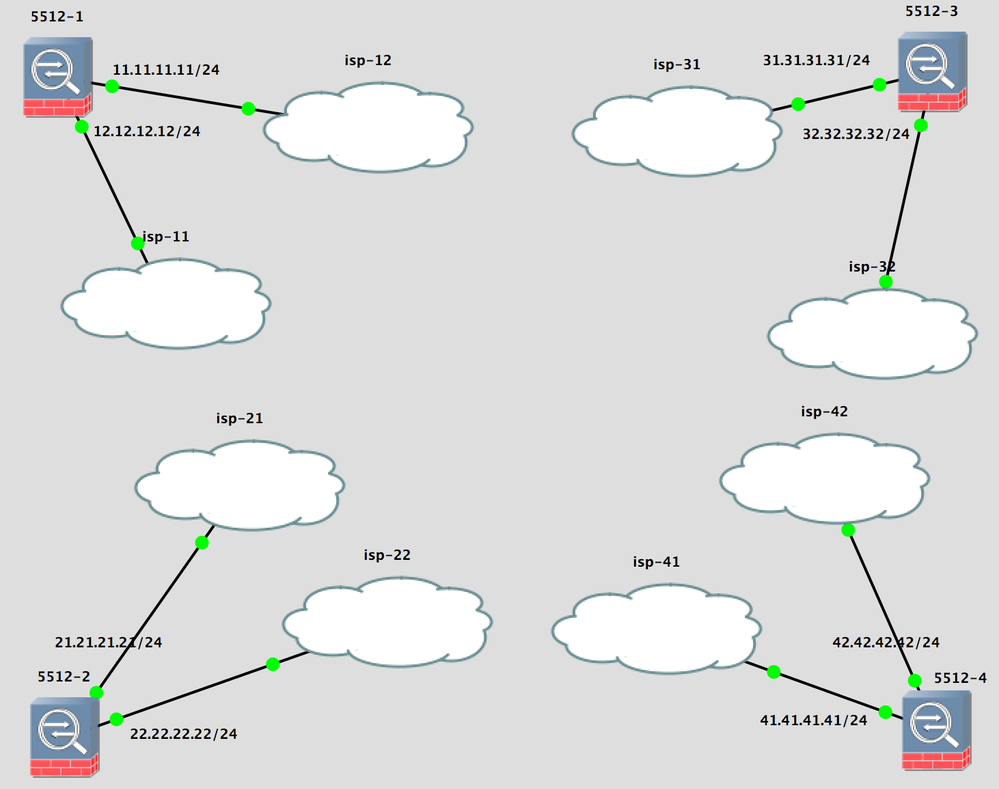
- We have 4 ASA 5512, each ASA have dualhomed connection to the Internet. Each ASA have 3 tunnels to other ASA.
How to configure backup action:
1) If one ISP goes down, second links comes up and tunnel reistablished?
2) If main ISP link comes up - tunnel reistablished from main connection
3) Does It possible to send any kind of notification from ASA if any of ISP goes down. (any type of build in email client which can send email )
4) If all of that possible, does it possible to emulate in GNS3 to check how it's works
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2018 01:57 PM
One of client have same setup, but we used syslog message to track the VPN and syslog messages to syslog(running under linux).
cron job keep checking the logs, if the log found VPN failed one, send email to user.
Personally i have not tried below method, this thread may help you :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 07:47 AM
So... Here is still main question
How to configure ASA for creating new VPN from backup link and get VPN back when main link is UP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 08:56 AM
So... Here is still main question
How to configure ASA for creating new VPN from backup link and get VPN back when main link is UP?
As per your diagram i was in impression that you already have 2 VPN's configured working.
You configure same way the primary tunnel configuration only change here different ISP and remote end IP address and ACL.
Once both the tunnel up and running, you can use IP SLA to track the VPN links, So example ISP1 VPN Primary do down, you track with IP SLA and configure to fail over to Secondary ISP2 VPN Link.
You can also configure Preempt once the primary link stable you can route back the traffic back to Primary Link depends on your requirement.
below example guide for IP SLA.
Hope this what you looking for ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2018 10:22 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide