- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA 5516 / FirePower - Restricted packets showing as allowed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5516 / FirePower - Restricted packets showing as allowed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 10:43 AM
Hi,
We found no interfaces are set with a security zone in FMC, and when looking at the firepower module in the ASA all interfaces are set as ASA for the type. We confirmed the drop when inline box was checked, and noted the base policy is set for connectivity over security. Can anyone answer of questions below, I posed this before but didn't receive a confirmation.
Do the interfaces need to be configured with a security zone in FMC for this to work, or should this work as it is configured currently?
Also, is the recommended base policy for it to be set to balanced security and connectivity?
I've attached screenshots to go with this as well.
Thanks for your assistance it's greatly appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 12:40 PM
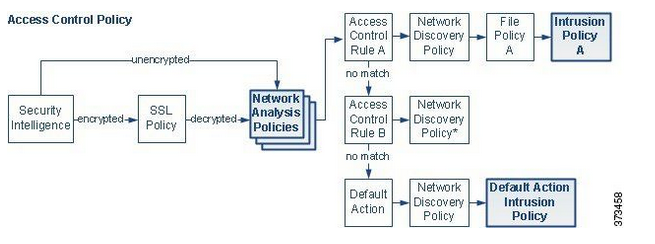
so just to confirm you running ASA with SFR sensor? if this is correct. here is my input into this. A security zone is a grouping of one or more ASA interfaces that you can use to manage and classify traffic flow in various policies and configuration.
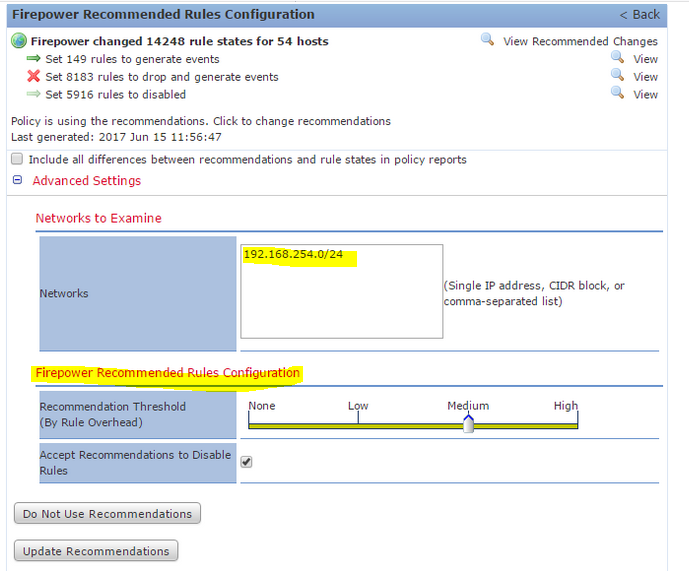
have a security zone I see it as a best practice it will give you more insight when you doing a tshoot and understand/implement you security posture. without configuration the security zone the flow of L7 will still work. in regards to which intrusion policy to use it all depend on your company/organization security policy. here is a document to give you a bit of understand which policy is best. (the document is old but the foundation apply to all intrusion policy to date software.) I recommend you to generate the Firepower recommendations policy under policy information at Intrusion policy. so make sure you network discovery is also configured properly. as network discovery play a vital rule in L7 inspection.
here this will give you some understanding.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 06:49 PM
Zones are an optional component in both native ASA and FTD deployments. They are most useful when grouping multiple interfaces in order to apply similar security policy to them.
The majority of deployments I have seen use a "Balanced Security and Connectivity" intrusion policy.
We would need to know more about your configuration to ascertain why what you want to be restricted is allowed. It is more often the Access Control Policy (and not the IPS policy) that drops traffic.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide