- Cisco Community
- Technology and Support
- Security
- Network Security
- I assume that you are having
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2016 03:10 AM - edited 03-12-2019 12:32 AM
Hi all,
I have a very weird issue with our office ASA. It's a ASA 5510 running on version 9.1.6 (the latest version available for this model).
The ASA is configured as router on a stick. The inside Ethernet0/1 interface is divided into multiple subinterfaces, each serving its own VLAN. I have a Management VLAN configured on Security level 100. In this network we host a Hyper-V server. We also have a VMNet VLAN configured on security level 90. This one houses the virtual machines. And our third VLAN is the Office VLAN (workstations) configured on security level 50.
By default, a higher level security interface should be able to access all lower security level networks without creating any ACL's. Because the ASA maintains a stateful connection table, return traffic should flow back without having to create an ACL for that. Now here's where it gets strange. My Management network (sec. level 100) is able to ping and access all virtual machines in VMNet (sec. level 90) but it is unable to access or ping any machines in the Office network (sec. level 50). Same thing for the VMNet VLAN. The virtual machines are unable to access or ping Office machines. The Office machines are not running any internal firewalls such as Windows firewall. For instance, the Office printer is unaccessible. And yes, the printer's IP, subnetmask and gateway are all correct.
Also, our Outside interface is configured on security level 0. However, our Active Directory virtual machine in VMNet, which also hosts the internal DNS server, was unable to resolve external domainnames. I had to create an ACL in the ASA telling it the AD server was allowed to perform UDP/53 requests to the outside world.
What am I doing wrong? This kind of goes against all theories...
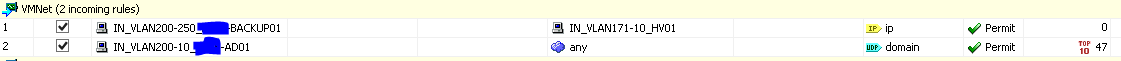
Due to our security policies I am unable to share the full ASA config with you, as it contains stuff like IP adressing and object names. The config is too big to sensor all these names and numbers by hand. However, I can show you the following two pictures taken from ASDM.
As you can see, on MGMT, all traffic should be allowed, but it isn't to the Office network. On VMNet, the backup server is allowed to do anything to the HV01 server in MGMT. This works as expected. As you can see, I had to explicitly configure an ACL that tells the ASA that DNS queries to the outside world are allowed by AD01.

Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2016 03:17 PM
I assume that you are having two problems here:
- The default behavior that traffic can freely travel from higher to a lower security-level, is removed the moment you apply an ACL to the higher level interface. On your VMnet interface you have an ACL, so you need a permit-ACE also for traffic that goes to the outside.
- For all testing with ICMP, you have to tell the ASA that ICMP/Ping should be inspected statefully which is not done by default. You need the following config for that:
policy-map global_policy
class inspection_default
inspect icmp
!
service-policy global_policy global
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2016 03:17 PM
I assume that you are having two problems here:
- The default behavior that traffic can freely travel from higher to a lower security-level, is removed the moment you apply an ACL to the higher level interface. On your VMnet interface you have an ACL, so you need a permit-ACE also for traffic that goes to the outside.
- For all testing with ICMP, you have to tell the ASA that ICMP/Ping should be inspected statefully which is not done by default. You need the following config for that:
policy-map global_policy
class inspection_default
inspect icmp
!
service-policy global_policy global
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


