- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Asa lan to lan ipsec tunnel tunnel on a stick
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2019 04:27 AM - edited 02-21-2020 08:39 AM
Hello
I want to confirm if this deployment would work or not.
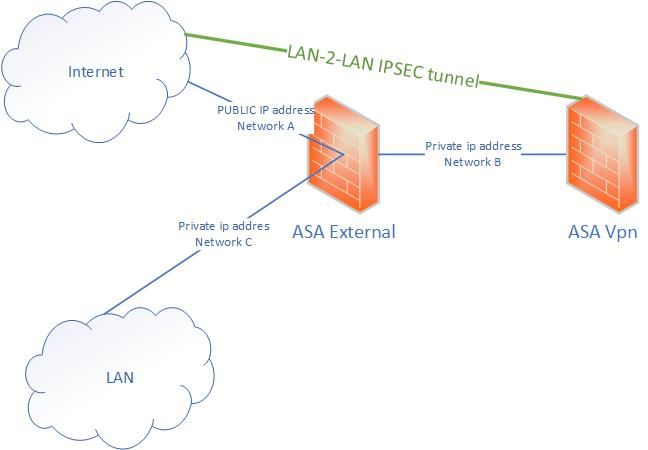
We would have a asa firewall (external) conected to the internet router. The link between the internet routers and the asa would use a public ip address range. And another asa (vpn) connected to this firewall using a private subnet.
The external firewall would nat the private ip address from the vpn asa to a public ip address from the range.
The router in the lan network would have a default route to internet pointing to the external firewall.
The vpn firewall would have a default route pointing to the external firewall.
The external firewall would have a default route pointing to internet and more specific routes pointing to the LAN and to the vpn firewall.
We would like to set a lan to lan tunnel between some internal networks to some networks in other offices through internet.
So for example. The intarl network would be the subnet 10.1.1.0/24 and the remote network in the other office would be the subnet 20.1.1.0/24. There would be a route in the external firewall for reaching the network 10.1.1.0/24 where the next hop is the LAN router ip address (network C) and another route for reaching the network 20.1.1.1/24 where the next hop is the VPN firewall private ip address (network B). And the VPN router would have a default route where the next hop is the External firewall (network B)
In this case the vpn router would receive the packets to the network 20.1.1.0/24 in the same interface (network B) that it would use for reaching the same destination using the default ip route.
The question is: Would the vpn firewall accept those packets and would try to establish the ipsec tunnel or would discard these packets and would not try to setup the ipsec tunnel? Once the ipsec tunnel is established the destination for the packets in the tunnel would not be the subnet 20.1.1.0/24 so the external firewall would route them to the internet.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2019 08:29 AM
This is just standard hairpinning. This should work fine so long as NAT and ACLs on the external ASA are correct, and VPN on the VPN ASA is correct.
Another option you could look into is setting up subinterfaces so that you would be using one physical interface but two logical interfaces for this traffic.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 12:52 AM
traffic coming in to the ASA from the LAN will be unencrypted, traffic heading toward the remote site will be encrypted so the "core" ASA will see different IPs . All you need to do is configure same-security-traffic permit intra-interface and make sure that routing on the VP ASA and core ASA is correct.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2019 06:05 AM
oh dear. That was a long story :-)
here is my input. looking into the topology. if you want to bypass the ASA external
in order to create a site to site vpn with ASA vpn. yes that is possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2019 08:29 AM
This is just standard hairpinning. This should work fine so long as NAT and ACLs on the external ASA are correct, and VPN on the VPN ASA is correct.
Another option you could look into is setting up subinterfaces so that you would be using one physical interface but two logical interfaces for this traffic.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2019 08:38 AM - edited 01-15-2019 08:38 AM
Let us know if you need help. We are happy to help that’s why we are here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 12:07 AM
Hello.
So there would not be any routing issue or anti spoofing check in the vpn asa that would affect to this setup?
Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 12:52 AM
traffic coming in to the ASA from the LAN will be unencrypted, traffic heading toward the remote site will be encrypted so the "core" ASA will see different IPs . All you need to do is configure same-security-traffic permit intra-interface and make sure that routing on the VP ASA and core ASA is correct.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2019 01:07 AM
Thanks for the confirmation.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide