- Cisco Community
- Technology and Support
- Security
- Network Security
- Hi, It seems to me that there
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2014 07:51 AM - edited 03-11-2019 09:27 PM
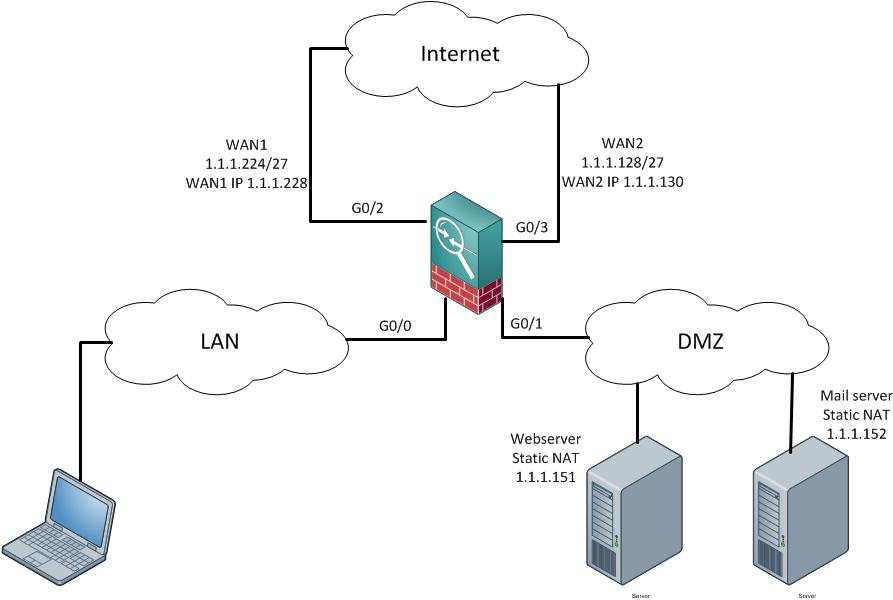
Have an ASA5520 with inside and DMZ interface. My hope is to use separate WAN interfaces for each. WAN1 would be default for any outbound traffic from LAN. WAN2 is a pool of IPs for static NATs to DMZ. below is a breakdown. The issue i have is getting DMZ servers to use the static NAT ip for its outbound traffic. Is this possible? I have been playing with 8.2, 8.4 , and 9.1 and cannot find a solution. I thought 8.4 and 9.1 i could use the NAT to overide the route but cannot seem to get that to work.
1. WAN1 - 1.1.1.228 - default interface for all outbound LAN traffic
2. WAN2 - 1.1.1.130 - have pool (1.1.1.128/27) to use for static NATs to DMZ servers (webserver 1.1.1.151, email 1.1.1.152, etc)
3. LAN - 10.x.x.x - can access DMZ (webserver,email,etc). outbound traffic would use WAN1 interface IP for NAT.
4.DMZ - 172.21.10.x - need DMZ to NAT outbound via WAN2 using the IP assigned for static NAT and not the WAN1 or WAN2 interface IP.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 12:26 AM
Hi,
It seems to me that there has been different results with the NAT configurations depending on the software level. On some software levels the ASA has ignored the NAT configuration completely when forwarding traffic and in another software level it has worked just fine.
If you have access to the ASA softwares from cisco.com then I would suggest trying out the software level 9.1(1). If I remember right that has worked with me atleast. Naturally its not really a good situation if you can only run your setup on a specific software and anything else would break it.
What kind of configurations have you attempted on your ASA with the mentioned software levels. I might be able to test something out.
I have had no problems with some software levels (even in the 8.4 series) to get the above scenario to work.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 01:45 AM
Hi,
I guess it will not work for you as expected. If you have your default route pointed to WAN1 which will take all the traffic towards that from inside and the return as well.,.... In case you have the static pools through WAN2 then from outside to inside wouldn't be the problem.... but any inside traffic from servers to outside would go via WAN1 only.... If that gets NAted to a IP which is not a part of WAN1 pool then it will drop... please correct me if my statement is wrong.
If you have the router on top of fw can do with the policy based routing for you to achieve it.....
Regards
Karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 12:26 AM
Hi,
It seems to me that there has been different results with the NAT configurations depending on the software level. On some software levels the ASA has ignored the NAT configuration completely when forwarding traffic and in another software level it has worked just fine.
If you have access to the ASA softwares from cisco.com then I would suggest trying out the software level 9.1(1). If I remember right that has worked with me atleast. Naturally its not really a good situation if you can only run your setup on a specific software and anything else would break it.
What kind of configurations have you attempted on your ASA with the mentioned software levels. I might be able to test something out.
I have had no problems with some software levels (even in the 8.4 series) to get the above scenario to work.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 06:54 AM
I know it is not ideal, but I am stuck in a tough spot. Our WAN1 IP is tied to many web accounts that need to see LAN users coming from the 1.1.1.228. I also need to build a new DMZ and don't have the IPs in the .228 space. That is why I am trying to move DMZ to a new IP space on WAN2. My concern is outbound email...if all outbound is NAT out WAN1 the IP will be different than what our email domain resolves. many companies will drop the email if they are not the same.
nkarthikeyan-
Yes. the default route is pointed to WAN1. i added a second to WAN2 w/ metric 2. you are correct on the inbound/outbound behavior.
Jouni-
I don't have a config right now. i blew it away last night to move back to 9. it is still labbed up so I will build it up this weekend and update.
Everyone's comments make sense. For some reason I got it in my head that NAT override was more common than i guess it is or accepted use. I read several articles where comments where made that 8.4+ NAT could override the route-lookup and was more of a feature now.
Ideal situation would be to move my LAN to the .130 subnet and run everything off single WAN interface.... next would be add router for PBR or separate ASAs for each.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 07:04 AM
Hi,
I was under the same imperssion too with regards to NAT and traffic forwarding on the newer software. I have used 8.4 series software on my ASA5505 at home for a long time and it has worked fine for me.
There are a few threads on these forums where I have provided the configurations also. But after those posts some people have had problems getting the same configurations working on different software levels.
Here is a link to one of the discussions where I tested this, maybe it will be of some help
https://supportforums.cisco.com/discussion/11784186/asa-5500-x-91-identity-nat
There have been some mentions even from the TAC that this should not work at all and its supposed to be a bug which I can't accept since its been the default behaviour of NAT as long as I can remember with Cisco firewalls. I mean the fact that NAT can affect where traffic is forwarded instead of routing table.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2014 07:34 AM
thank you both for your input. I decided to drop a router outside the ASA for PBR and NAT. Maybe can revisit in the future if feature is added.
mopep
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 01:45 AM
Hi,
I guess it will not work for you as expected. If you have your default route pointed to WAN1 which will take all the traffic towards that from inside and the return as well.,.... In case you have the static pools through WAN2 then from outside to inside wouldn't be the problem.... but any inside traffic from servers to outside would go via WAN1 only.... If that gets NAted to a IP which is not a part of WAN1 pool then it will drop... please correct me if my statement is wrong.
If you have the router on top of fw can do with the policy based routing for you to achieve it.....
Regards
Karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2014 02:05 AM
Hi,
It seems to me that he has tried to use the NAT to modify the behaviour of the ASA. I mean choose a different WAN link depending on the source network. I have been able to do this on a couple different software levels (software 8.4 and up) and it has worked just fine.
It's not really an ideal solution but a solution nevertheless if the situation simply requires a fast solution before doing it the proper way. I agree that a router in front of the ASA would be a lot better/easier solution to handle WAN link usage with PBR.
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


