- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA5505 - Need help with port forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 01:26 AM - edited 02-21-2020 08:37 AM
Hi everyone,
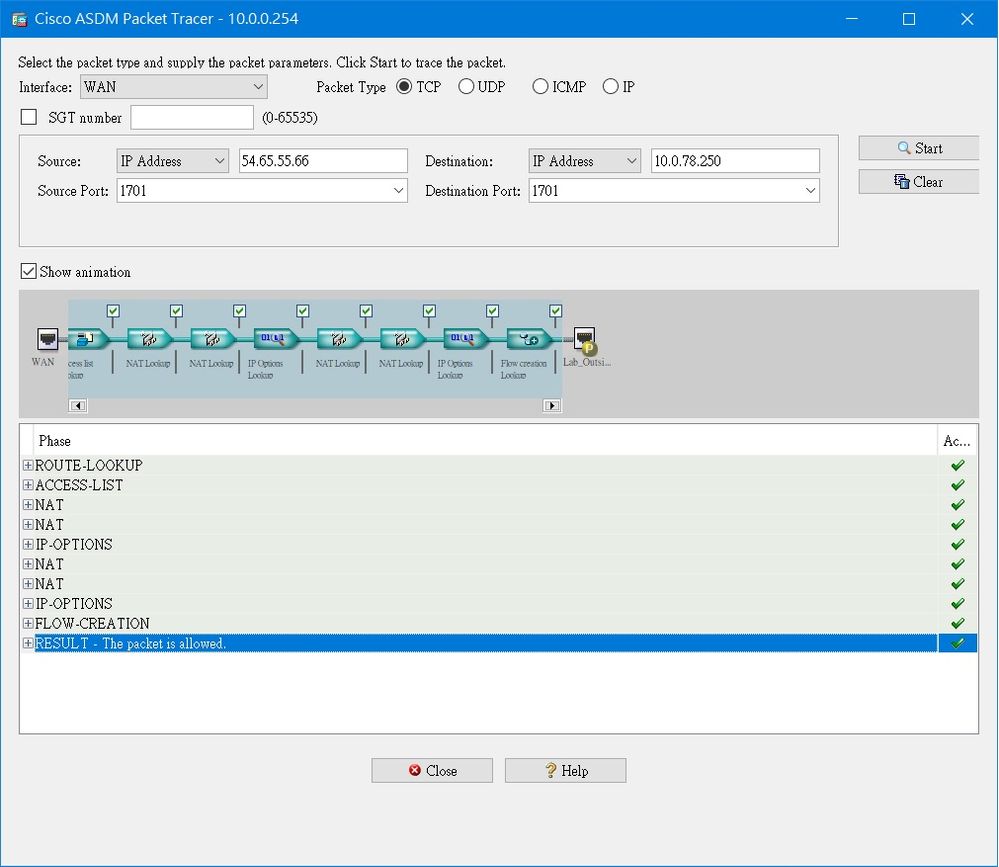
I have been struggling to get port forwarding to work on my ASA5505.
So far I have setup an ACL to permit the port traffic and NAT rule to forward to port to the specific host.
Packet tracer in the ASDM shows that the packet is allowed. However when I test using the below powershell command :
tnc [ASA outside interface address] -port [port number]
it shows that the connection to the port is failed. ASDM syslog doesnt even have logged the tcp connnection try.
Any help would be appreciated.
ASA Version : 9.2(4)33
ASDM Version : 7.9(2)152
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 06:04 PM
after looking at the packet tracer log and looking at your nat order if seems you have a nat order issue. VPN-Server rule should be in section 1
ciscoasa(config)# show nat
Manual NAT Policies (Section 1)
1 (Lab_Outside_Gateway) to (WAN) source dynamic any interface
translate_hits = 28304, untranslate_hits = 815
2 (Lab_Host_Network) to (WAN) source dynamic any interface
translate_hits = 18387, untranslate_hits = 172
3 (Home_Network_1_Gateway) to (WAN) source dynamic any interface
translate_hits = 73636, untranslate_hits = 729
4 (Home_Network_2_Gateway) to (WAN) source dynamic any interface
translate_hits = 59292, untranslate_hits = 11423
5 (WAN) to (Lab_Outside_Gateway) source dynamic any interface
translate_hits = 9, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (Lab_Outside_Gateway) to (WAN) source static VPN-Server interface service tcp 1701 1701
translate_hits = 0, untranslate_hits = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 01:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 02:08 AM - edited 01-02-2019 02:09 AM
Here is the config. Thanks.
ASA Version 9.2(4)33
!
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
switchport access vlan 11
!
interface Ethernet0/2
switchport access vlan 12
!
interface Ethernet0/3
switchport access vlan 13
!
interface Ethernet0/4
switchport access vlan 14
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan10
nameif WAN
security-level 0
ip address dhcp setroute
!
interface Vlan11
nameif Lab_Outside_Gateway
security-level 100
ip address 10.0.255.254 255.255.255.0
!
interface Vlan12
nameif Home_Network_1_Gateway
security-level 90
ip address 172.31.255.254 255.255.255.0
!
interface Vlan13
nameif Home_Network_2_Gateway
security-level 10
ip address 192.168.255.254 255.255.255.0
!
interface Vlan14
nameif Lab_Host_Network
security-level 100
ip address 10.0.0.254 255.255.255.0
!
ftp mode passive
clock timezone HKST 8
dns server-group DefaultDNS
same-security-traffic permit inter-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network VPN-Server
host 10.0.78.250
object service VPN-Service-Port-3
service tcp destination eq 1701
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
access-list WAN_access_in extended permit icmp any 10.0.0.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 10.0.255.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 172.31.255.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 192.168.255.0 255.255.255.0
access-list WAN_access_in extended permit object VPN-Service-Port-3 any object VPN-Server
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
pager lines 24
logging enable
logging asdm informational
mtu Lab_Outside_Gateway 1500
mtu Home_Network_1_Gateway 1500
mtu Lab_Host_Network 1500
mtu WAN 1500
mtu Home_Network_2_Gateway 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (Lab_Outside_Gateway,WAN) source dynamic any interface
nat (Lab_Host_Network,WAN) source dynamic any interface
nat (Home_Network_1_Gateway,WAN) source dynamic any interface
nat (Home_Network_2_Gateway,WAN) source dynamic any interface
nat (WAN,Lab_Outside_Gateway) source dynamic any interface
!
object network VPN-Server
nat (Lab_Outside_Gateway,WAN) static interface service tcp 1701 1701
access-group WAN_access_in in interface WAN
route Lab_Outside_Gateway 10.0.11.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.14.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.78.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.254.0 255.255.255.0 10.0.255.10 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 10.0.0.0 255.255.255.0 Lab_Host_Network
no snmp-server location
no snmp-server contact
no sysopt connection permit-vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 02:12 AM
Here is the config. Thanks.
ASA Version 9.2(4)33
!
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
switchport access vlan 11
!
interface Ethernet0/2
switchport access vlan 12
!
interface Ethernet0/3
switchport access vlan 13
!
interface Ethernet0/4
switchport access vlan 14
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan10
nameif WAN
security-level 0
ip address dhcp setroute
!
interface Vlan11
nameif Lab_Outside_Gateway
security-level 100
ip address 10.0.255.254 255.255.255.0
!
interface Vlan12
nameif Home_Network_1_Gateway
security-level 90
ip address 172.31.255.254 255.255.255.0
!
interface Vlan13
nameif Home_Network_2_Gateway
security-level 10
ip address 192.168.255.254 255.255.255.0
!
interface Vlan14
nameif Lab_Host_Network
security-level 100
ip address 10.0.0.254 255.255.255.0
!
ftp mode passive
clock timezone HKST 8
dns server-group DefaultDNS
same-security-traffic permit inter-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network VPN-Server
host 10.0.78.250
object service VPN-Service-Port-3
service tcp destination eq 1701
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
access-list WAN_access_in extended permit icmp any 10.0.0.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 10.0.255.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 172.31.255.0 255.255.255.0
access-list WAN_access_in extended permit icmp any 192.168.255.0 255.255.255.0
access-list WAN_access_in extended permit object VPN-Service-Port-3 any object VPN-Server
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
pager lines 24
logging enable
logging asdm informational
mtu Lab_Outside_Gateway 1500
mtu Home_Network_1_Gateway 1500
mtu Lab_Host_Network 1500
mtu WAN 1500
mtu Home_Network_2_Gateway 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (Lab_Outside_Gateway,WAN) source dynamic any interface
nat (Lab_Host_Network,WAN) source dynamic any interface
nat (Home_Network_1_Gateway,WAN) source dynamic any interface
nat (Home_Network_2_Gateway,WAN) source dynamic any interface
nat (WAN,Lab_Outside_Gateway) source dynamic any interface
!
object network VPN-Server
nat (Lab_Outside_Gateway,WAN) static interface service tcp 1701 1701
access-group WAN_access_in in interface WAN
route Lab_Outside_Gateway 10.0.11.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.14.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.78.0 255.255.255.0 10.0.255.10 1
route Lab_Outside_Gateway 10.0.254.0 255.255.255.0 10.0.255.10 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 10.0.0.0 255.255.255.0 Lab_Host_Network
no snmp-server location
no snmp-server contact
no sysopt connection permit-vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 06:01 AM
you config is wrong
put this command
no access-list WAN_access_in extended permit object VPN-Service-Port-3 any object VPN-Server
access-list WAN_access_in extended permit tcp any object VPN-Service-Port-3 object VPN-Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 04:03 PM - edited 01-02-2019 04:04 PM
Thanks for taking a look at the config.
I have tried to put in the two commands you listed. the second command doesn't seem to work.
ERROR : specified object <VPN-Service-Port-3> has wrong type;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 02:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:16 PM - edited 01-02-2019 05:24 PM
test this
no access-list WAN_access_in extended permit tcp any object VPN-Service-Port-3 object VPN-Server
access-list WAN_access_in extended permit tcp any object VPN-Server eq 1701
also thought instead of this
!
object network VPN-Server
host 10.0.78.250
nat (Lab_Outside_Gateway,WAN) static interface service tcp 1701 1701
!
you can have this
!
object network VPN-Server
host 10.0.78.250
nat (Lab_Outside_Gateway,WAN) static interface
!
because we have access-list narrow it down to certain port no. so when someone from outside internet connects to your asa WAN link address with port 1701 will be directed to VPN-Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:25 PM - edited 01-02-2019 05:32 PM
The commands can be successfully applied.
However ASDM still doesnt register any hit when I try to make connection to port 1701 and the connection still fails.
Edit : I have also tried to change the NAT rule like you stated. but it seems like the asa internet facing interface (WAN) is still not registering any connection made to port 1701
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:32 PM - edited 01-02-2019 05:33 PM
run this and share the output
packet-tracer input WAN tcp 8.8.8.8 1701 10.0.78.250 1701 detail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:37 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:42 PM
share the output of command
show nat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 05:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 06:04 PM
after looking at the packet tracer log and looking at your nat order if seems you have a nat order issue. VPN-Server rule should be in section 1
ciscoasa(config)# show nat
Manual NAT Policies (Section 1)
1 (Lab_Outside_Gateway) to (WAN) source dynamic any interface
translate_hits = 28304, untranslate_hits = 815
2 (Lab_Host_Network) to (WAN) source dynamic any interface
translate_hits = 18387, untranslate_hits = 172
3 (Home_Network_1_Gateway) to (WAN) source dynamic any interface
translate_hits = 73636, untranslate_hits = 729
4 (Home_Network_2_Gateway) to (WAN) source dynamic any interface
translate_hits = 59292, untranslate_hits = 11423
5 (WAN) to (Lab_Outside_Gateway) source dynamic any interface
translate_hits = 9, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (Lab_Outside_Gateway) to (WAN) source static VPN-Server interface service tcp 1701 1701
translate_hits = 0, untranslate_hits = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2019 06:19 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide