- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA5506 - BVI - Port Forwarding issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2020 07:44 AM
Hello All -
My ASA5506 is configured as BVI - Interface. I have tried to set some port forwarding following these steps and still not able to get the port working!!!
1. I need to forward these ports (5000, 5001, 1194, 3389, 1701, 4500, 500) from my NAS -
My network configuration - ISP Modem - Firewall - Switch L2.
I have followed these steps to forward any port with no luck - I'm not sure what is missing?
object network NAS
host 10.203.111.131 ------ This IP is for the NAS-Synology
object service 5001
service tcp source eq 5001
nat (any,outside) 1 source static NAS interface service 5001 5001
access-list outside_in permit tcp any host 10.203.111.131 eq 5001
access-group outside_in in interface outside
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 02:14 AM
as you have issues connecting to your network from anyconnect inthat case to access your internal resources in your internal network you have to define some rule.
!
object network POOL-A
here anyconenct pool you define
!
nat (any,outside) static source any any destin static POOL-A POOL-A no-proxy-arp route-lookup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 06:30 AM
Hello - All - any feedback - please.
My ASA is configured as bridge mode BVI1 -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 06:53 AM
object network NAS
host 10.203.111.131
nat (any,outside) 1 source static NAS interface service 5001 5001
Change "any" to be more specific, such as "inside" if the NAS is connected to inside.
Provide the output of "show nat detail"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 07:32 AM
Here are the details -
1. If select inside then i will get an error as it is not existing because of the ASA in BVI mode, so it has to be any or inside_1, iside_2,inside_3,ect
2. Also, I got an error that 1194 is not a valid service object name.
1 (inside_1) to (outside) source dynamic obj_any1 interface
translate_hits = 305981, untranslate_hits = 900
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
2 (inside_2) to (outside) source dynamic obj_any2 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
3 (inside_3) to (outside) source dynamic obj_any3 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
4 (inside_4) to (outside) source dynamic obj_any4 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
5 (inside_5) to (outside) source dynamic obj_any5 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
6 (inside_6) to (outside) source dynamic obj_any6 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
7 (inside_7) to (outside) source dynamic obj_any7 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 07:38 AM
Here is the NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 07:49 AM
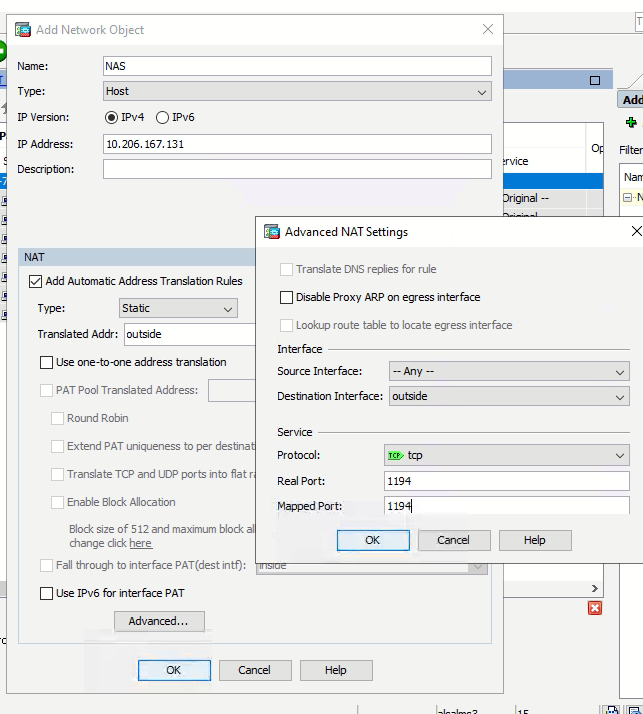
You need to define a service object for 1194 then you can create an object and reference the service called 1194 in the nat configuration. e.g:-
object service 1194
service tcp source eq 1194
object network NAS-1194
host 10.203.111.131
nat (any,outside) 1 source static NAS-1194 interface service 1194 1194
access-list outside_in permit tcp any host 10.203.111.131 eq 1194
When you run "show nat detail" again you should see that rule you added should be added to Manual NAT Rules Section 1 - and above the dynamic rules you already have in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 07:57 AM
Here is the show run -
Manual NAT Policies (Section 1)
1 (any) to (outside) source static NAS-1194 interface service 1194 1194
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.206.167.131/32, Translated: 192.168.100.3/24
Service - Origin: tcp source eq 1194 , Translated: tcp source eq 1194
Auto NAT Policies (Section 2)
1 (inside_1) to (outside) source dynamic obj_any1 interface
translate_hits = 307395, untranslate_hits = 900
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
2 (inside_2) to (outside) source dynamic obj_any2 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
3 (inside_3) to (outside) source dynamic obj_any3 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
4 (inside_4) to (outside) source dynamic obj_any4 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
5 (inside_5) to (outside) source dynamic obj_any5 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
6 (inside_6) to (outside) source dynamic obj_any6 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
7 (inside_7) to (outside) source dynamic obj_any7 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 192.168.100.3/24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 08:00 AM
Run packet-tracer from the CLI and provide the output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 08:03 AM
The port 1194 is forward from the ISP Modem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 08:16 AM - edited 02-21-2020 08:18 AM
NM2WCASA1(config)# packet-tracer input outside tcp 192.168.100.3 1194 10.206.167.131 1194
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.206.167.131 using egress ifc inside
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
NM2WCASA1(config)# packet-tracer input outside tcp 10.206.167.131 1194 192.168.100.3 1194
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.206.167.131 using egress ifc inside
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (any,outside) source static NAS-1194 interface service 1194 1194
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.100.3/1194 to 10.206.167.131/1194
Phase: 3
Type: SUBOPTIMAL-LOOKUP
Subtype: suboptimal next-hop
Result: ALLOW
Config:
Additional Information:
ifc selected is not same as preferred ifc
Doing route lookup again on ifc inside
Phase: 4
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.206.167.131 using egress ifc inside
Phase: 5
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (any,outside) source static NAS-1194 interface service 1194 1194
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.100.3/1194 to 10.206.167.131/1194
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (no-adjacency) No valid adjacency
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 08:27 AM
"packet-tracer input outside tcp 8.8.8.8 3000 192.168.100.3 1194"
Run a packet capture on the ASA, confirm you are actually receiving traffic destined to port 1194.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 08:51 AM
NM2WCASA1(config)#
NM2WCASA1(config)# packet-tracer input outside tcp 8.8.8.8 3000 192.168.100.3 $
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 192.168.100.3 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
NM2WCASA1(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 12:18 PM
You need to setup NAT for each specific interface and not the BVI interface. BVI is used for management and not through the box traffic.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 02:14 AM
as you have issues connecting to your network from anyconnect inthat case to access your internal resources in your internal network you have to define some rule.
!
object network POOL-A
here anyconenct pool you define
!
nat (any,outside) static source any any destin static POOL-A POOL-A no-proxy-arp route-lookup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2020 02:28 AM
THANK YOU FOR THE HELP --
Apprciate the collobration
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide