- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Hi Community,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Back to Back Cisco ASA Firewall (Internal and External)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2017 04:26 AM - edited 03-12-2019 01:46 AM
Hi Community,
I am new with Cisco firewall and need some advice on the network diagram.
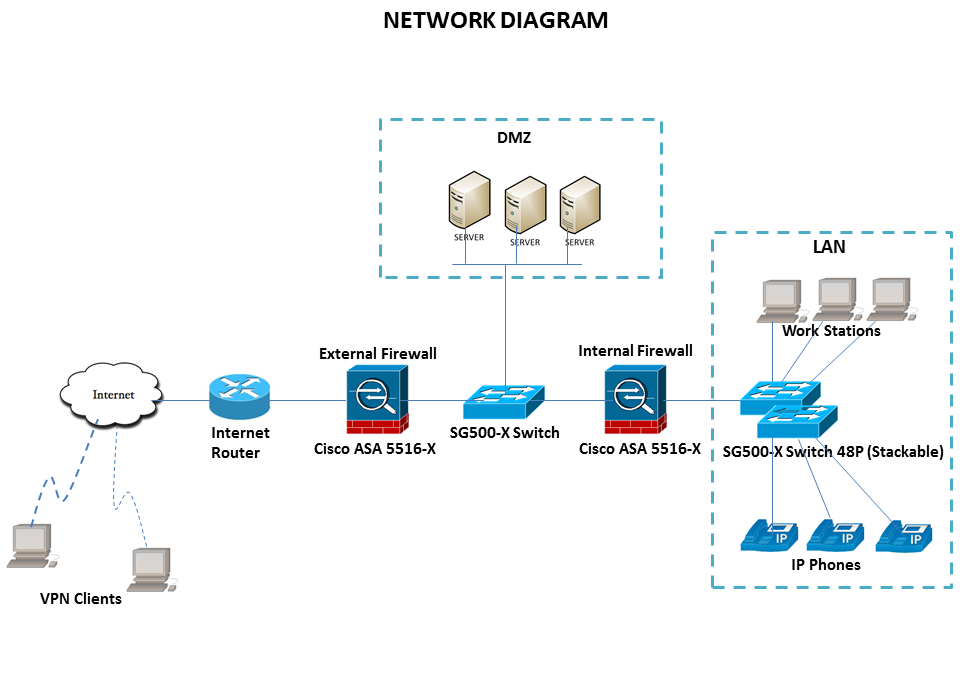
We will deploy 2x ASA firewall 5516 with Firepower for external and internal. We will use SG500-X switch in the network for DMZ and LAN.
Based on the diagram and network devices, i need to know if this will work? Also i need some deployment guide on how to implement 2 firewalls with DMZ configuration.
Thank you.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2017 01:03 AM
Hi Community,
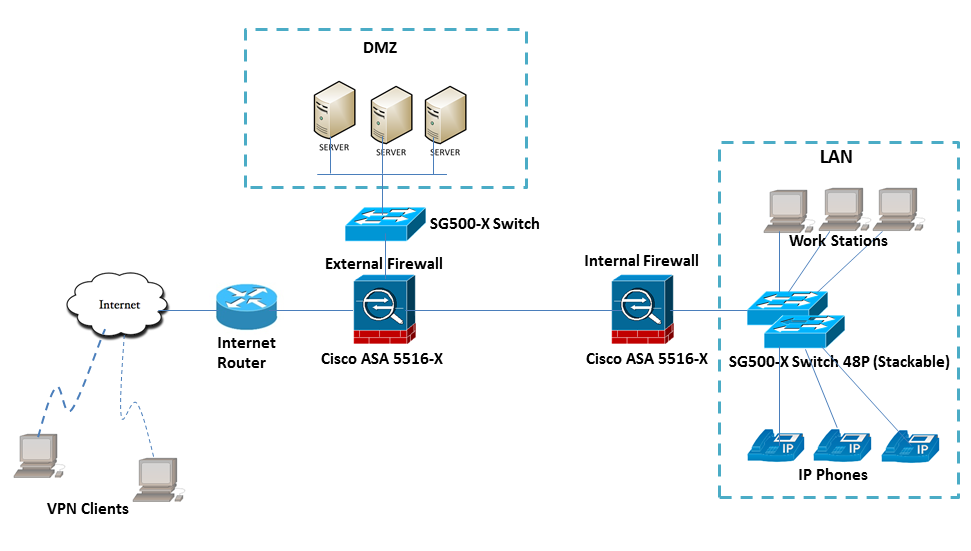
I would like to ask what is better design between the below diagrams with two back to back Cisco ASA firewall:
1. DMZ is on external firewall and External firewall (inside interface) is connected directly to Internal firewall (outside interface).
2. A DMZ is in between the External and Internal firewall with DMZ switch connected with each other.
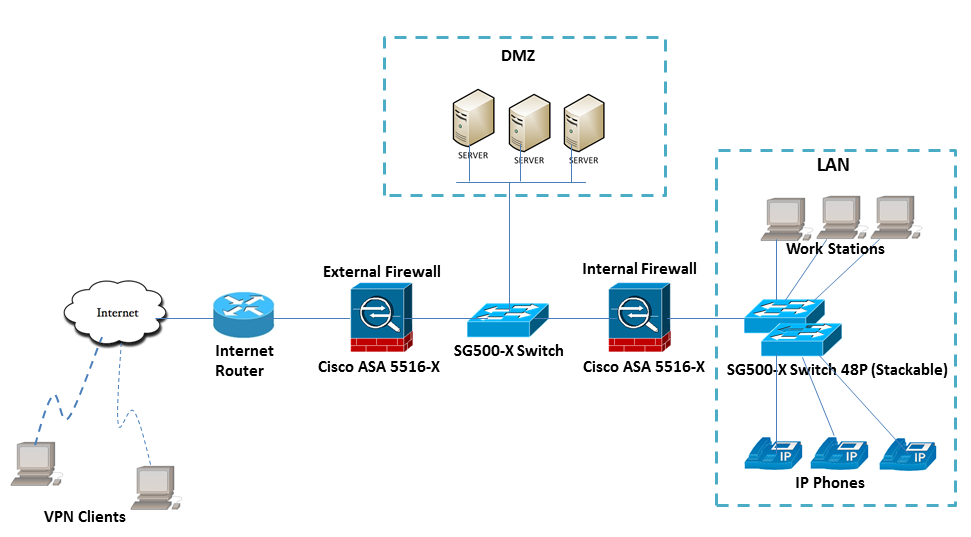
Need your recommendation please.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2017 06:10 AM
Both designs will work for sure. I am not sure why you have implemented 2 ASA when we could have achieved with just one ASA. DMZ anyways would be a different segment. And 2 ASA inline is adding to latency because each ASA has to process the traffic as per their configured policies.
If one of the design has to be there, I can just think of below criteria that we can check for the implementation:
- In design 1 , we are adding one more hop between the lan and dmz segment which is not the case in design 2. If the communication between lan and dmz is required/expected and we expect some good amount of traffic(like server backup etc), design 2 should be considered. This is to improve efficiency and take load off the external ASA.
Apart from that, I dont see anything else. This is assuming that both ASA are implemented in similar fashion.
Please let me know if you have any specific requirement/criteria in mind that can be explored.
-
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2017 12:58 AM
Hi AJ,
Thank you for your helpful comments.
We will consider the option 2 and we will add also are core switch (3850) in between the internal firewall and the SG500-X Stackable LAN switch.
Is there any guide on how we can configure the two ASA firewalls with the design we want to implement?
Thanks and regards.
Sy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2017 07:09 PM
Hi Sy,
Unfortunately, there isn't a design guide specifically for this requirement. This should be fairly simple to deploy. Let me know if there are any specific concerns regarding this design.
Regards,
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2017 10:00 PM
Hi AJ,
This is how we will interconnect the 2 firewalls on the network. Could you advise if this diagram will work fine?
I have followed the network connection on this guide:
http://www.cisco.com/c/en/us/td/docs/security/firepower/quick_start/5508X/ftd-fmc-5508x-qsg.html
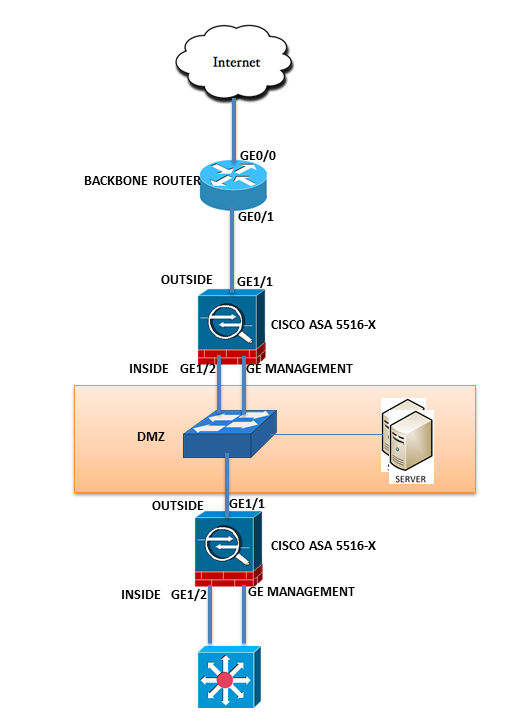
Thanks and regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2017 04:49 AM
I don't see any issues as such with the design. If you have a firepower/IPS module in the ASA 5515x, for outbound traffic (lan-to-internet and internet-to-lan), you can have one of the ASA inspect it and skip on second ASA since inspecting it twice would add to latency and does not make sense.
Other than that, I don't see any flaws with the design.
Let me know if you have any questions.
HTH
-AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-10-2019 10:24 PM
Hi Community,
I have the external firewall ASA 5506 configured from internet service provider to DMZ and I would like to add an internal firewall ASA 5506 to connect my local area network. do you have any guide I can follow?.
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
