- Cisco Community
- Technology and Support
- Security
- Network Security
- Basic Cisco ASA5525 routing fails
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2014 12:43 PM - edited 03-11-2019 08:41 PM
Good day,
I am starting this thread because we are experiencing a problem with a 'brandnew' cisco ASA 5525x firewall.
We never configured these firewalls before but since the setup is quite simple, we don't know what is going wrong.
This is getting quite urgent because we need this firewall in production fast.
The type is ASA5525-IPS-K9.
IPS license is not yet installed.
We have simplified our testing setup as in the image bellow (basically this is all we configured, standby firewall was switched off)).
We are firewalling from enterprise dekstops to production servers (no internet involved).
We have set all 'ACLs' open with any to any as much as possible, no blocked traffic is reported in debug mode of the logging.
We have also put all interfaces in the same 'zone' namely 100.
I am not sure if Enterprise IT people have replaced the w2008r2 router by a real router/firewall, but question remains.
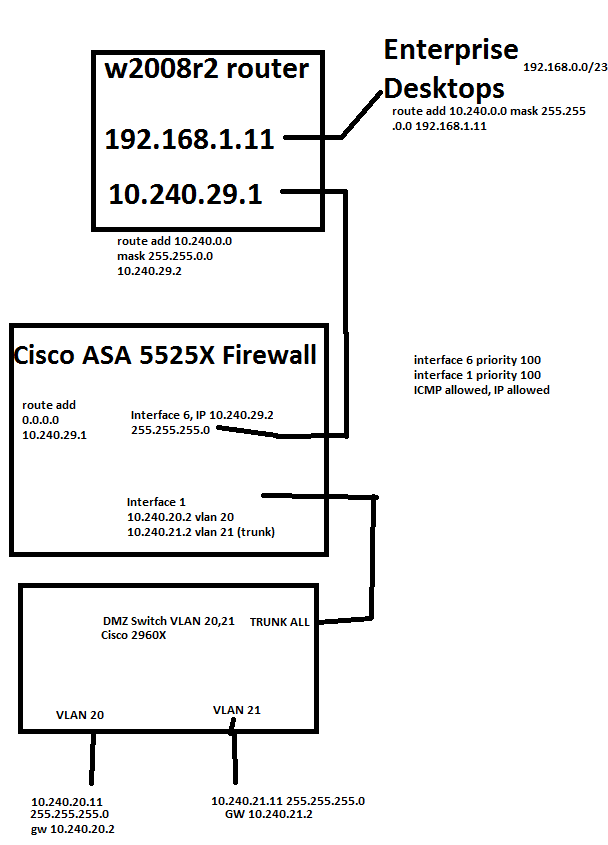
Ping request FAILS:
10.240.20.11 to 192.168.0.x
10.240.20.11 to 10.240.29.1 (I guess this is normal firewall behavior)
10.240.20.11 to 10.24.29.2
192.168.0.11 to 10.240.20.2 (I guess this is normal firewall behavior)
192.168.0.11 to 10.240.20.11
(same thing for 10.240.21.11)
Ping request OK:
192.168.0.11 to 10.240.29.1
192.168.0.11 to 10.240.29.2
10.240.20.11 to 10.240.21.11 (routed over the firewall)
We do not see any 'blocked' messages in the logging that is put to debug mode.
If we replace the 'w2008r2 router' by a single laptop with 1 connection and IP 10.240.29.1 GW 10.240.29.2 and connect in the same port, then we are able to ping from 10.240.29.1 to 10.240.20.11 and vice versa.
If we replace the Cisco firewall by a L3 Cisco 3750X with similar routing configuration, we can ping from 10.240.20.11 to the entire 192.168.0.0/23 network and vice versa.
These findings are making us very desperate in finding a solution because the findings do not make sense to me?
Can anyone please give some input on this?
If required I can upload the configuration file here.
Thank you very much in advance,
Best Regards,
Joris
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 04:10 AM
As Jouni has mentioned the packet capture will give us a 100% confirmation that the traffic is passing through the ASA.
Then, we started a ping from the laptop to the other, so started a ping from 10.240.29.1 to 10.240.10.11, this worked.
After this, the ping from 10.240.10.11 to 10.240.29.1 started succeeding, without any config change ???
OK, I don't see 10.240.10.11 in your diagram further up, though I do see that the ASA has an interface in this subnet. Are you experiencing this problem from all subnets attached to the ASA?
I am starting to wonder if the 2008r2 router is missing some routes maybe. Is this a Cisco router? Could you post the router configuration please?
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2014 11:27 PM
Hi,
I think we should start by looking at the ASAs configuration first
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 12:05 AM
This is the configuration file.
The real IPs we use (not in drawing above) are 10.240.10.11 (instead of 20.11)
Result of the command: "show running-config"
: Saved
:
ASA Version 8.6(1)2
!
hostname FRW
enable password * encrypted
passwd * encrypted
names
!
interface GigabitEthernet0/0
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1
channel-group 1 mode active
!
interface GigabitEthernet0/2
channel-group 1 mode active
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
description Link to c k voor vpn
nameif LinkTock
security-level 100
ip address 10.240.29.2 255.255.255.0
!
interface GigabitEthernet0/7
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.100.2 255.255.255.0
management-only
!
interface GigabitEthernet1/0
description Link to Core Switch
nameif LinkToCore
security-level 100
ip address 10.240.28.2 255.255.255.0
!
interface GigabitEthernet1/1
nameif LinkToDMZ
security-level 100
no ip address
!
interface GigabitEthernet1/1.10
description Vlan for DMZ SQL
vlan 10
nameif Vlan10DMZSQL
security-level 100
ip address 10.240.10.2 255.255.255.0 standby 10.240.10.4
!
interface GigabitEthernet1/1.11
description Link to Vlan 11 DMZ Backup
vlan 11
nameif Vlan11DMZBackup
security-level 100
ip address 10.240.11.2 255.255.255.0 standby 10.240.11.4
!
interface GigabitEthernet1/1.12
description Link to vlan 12 DMZ share
vlan 12
nameif Vlan12DMZShare
security-level 100
ip address 10.240.12.2 255.255.255.0 standby 10.240.12.4
!
interface GigabitEthernet1/1.13
description Link to Vlan 13 DMZ AVI
vlan 13
nameif Vlan13DMZAVI
security-level 100
ip address 10.240.13.2 255.255.255.0 standby 10.240.13.4
!
interface GigabitEthernet1/1.20
description Link to Vlan 20 DMZ ENG
vlan 20
nameif Vlan20DMZENG
security-level 100
ip address 10.240.20.2 255.255.255.0 standby 10.240.20.4
!
interface GigabitEthernet1/1.21
description Link to Vlan 21 DMZ External
vlan 21
nameif Vlan21DMZExternal
security-level 100
ip address 10.240.21.2 255.255.255.0 standby 10.240.21.4
!
interface GigabitEthernet1/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/4
description Link To Enterprise Core Swith 2
nameif LinkToEnterPriseCore2
security-level 0
ip address 10.240.202.2 255.255.255.0
!
interface GigabitEthernet1/5
description Link to Enterprise Core switch 1
nameif LinkToEnterpriseCore1
security-level 0
ip address 10.240.201.2 255.255.255.0
!
interface Port-channel1
description LAN/STATE Failover Interface
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list global_access extended permit ip any any log debugging
access-list global_access extended permit icmp any any log debugging
access-list Vlan20DMZENG_access_in extended permit icmp any any
access-list Vlan20DMZENG_access_in extended permit ip any any
access-list Vlan12DMZShare_access_out extended permit icmp any any
access-list Vlan12DMZShare_access_out extended permit ip any any
access-list LinkToEnterpriseCore1_access_out extended permit icmp any any
access-list LinkToEnterpriseCore1_access_out extended permit ip any any
access-list LinkToDMZ_access_out extended permit ip any any log debugging
access-list LinkToDMZ_access_out extended permit icmp any any log debugging
access-list Vlan11DMZBackup_access_out extended permit icmp any any
access-list Vlan11DMZBackup_access_out extended permit ip any any
access-list LinkToEnterpriseCore1_access_in extended permit icmp any any
access-list LinkToEnterpriseCore1_access_in extended permit ip any any
access-list Vlan20DMZENG_access_out extended permit icmp any any
access-list Vlan20DMZENG_access_out extended permit ip any any
access-list LinkToDMZ_access_in extended permit ip any any log debugging
access-list LinkToDMZ_access_in extended permit icmp any any log debugging
access-list Vlan10DMZSQL_access_out extended permit tcp any any log debugging
access-list Vlan10DMZSQL_access_out extended permit udp any any log debugging
access-list Vlan10DMZSQL_access_out extended permit icmp any any log debugging
access-list Vlan10DMZSQL_access_out extended permit ip any any log debugging
access-list Vlan10DMZSQL_access_out extended deny ip any any inactive
access-list Vlan10DMZSQL_access_out extended deny icmp any any inactive
access-list LinkToCore_access_in extended permit ip any any
access-list LinkToCore_access_in extended permit icmp any any
access-list LinkToEnterPriseCore2_access_out extended permit ip any any
access-list LinkToEnterPriseCore2_access_out extended permit icmp any any
access-list Vlan10DMZSQL_access_in extended permit icmp any any log debugging
access-list Vlan10DMZSQL_access_in extended permit udp any any log debugging
access-list Vlan10DMZSQL_access_in extended permit tcp any any log debugging
access-list Vlan10DMZSQL_access_in extended permit ip any any log debugging
access-list Vlan10DMZSQL_access_in extended deny ip any any inactive
access-list Vlan10DMZSQL_access_in extended deny icmp any any inactive
access-list LinkToEnterPriseCore2_access_in extended permit ip any any
access-list LinkToEnterPriseCore2_access_in extended permit icmp any any
access-list Vlan21DMZExternal_access_out extended permit icmp any any
access-list Vlan21DMZExternal_access_out extended permit ip any any
access-list Vlan12DMZShare_access_in extended permit icmp any any
access-list Vlan12DMZShare_access_in extended permit ip any any
access-list Vlan13DMZAVI_access_in extended permit icmp any any
access-list Vlan13DMZAVI_access_in extended permit ip any any
access-list LinkToCore_access_out extended permit ip any any
access-list LinkToCore_access_out extended permit icmp any any
access-list Vlan21DMZExternal_access_in extended permit icmp any any
access-list Vlan21DMZExternal_access_in extended permit ip any any
access-list Vlan11DMZBackup_access_in extended permit icmp any any
access-list Vlan11DMZBackup_access_in extended permit ip any any
access-list Vlan13DMZAVI_access_out extended permit icmp any any
access-list Vlan13DMZAVI_access_out extended permit ip any any
access-list LinkTock_access_out extended permit tcp any any log debugging
access-list LinkTock_access_out extended permit udp any any log debugging
access-list LinkTock_access_out extended permit icmp any any log debugging
access-list LinkTock_access_out extended permit ip any any log debugging
access-list LinkTock_access_in extended permit udp any any log debugging
access-list LinkTock_access_in extended permit tcp any any log debugging
access-list LinkTock_access_in extended permit icmp any any log debugging
access-list LinkTock_access_in extended permit ip any any log debugging
pager lines 24
logging enable
logging asdm informational
mtu LinkTock 1500
mtu management 1500
mtu LinkToCore 1500
mtu LinkToDMZ 1500
mtu Vlan10DMZSQL 1500
mtu Vlan11DMZBackup 1500
mtu Vlan12DMZShare 1500
mtu Vlan13DMZAVI 1500
mtu Vlan20DMZENG 1500
mtu Vlan21DMZExternal 1500
mtu LinkToEnterPriseCore2 1500
mtu LinkToEnterpriseCore1 1500
failover
failover lan unit primary
failover lan interface failover Port-channel1
failover link failover Port-channel1
failover interface ip failover 10.240.100.1 255.255.255.0 standby 10.240.100.2
no monitor-interface LinkTock
no monitor-interface management
monitor-interface Vlan10DMZSQL
monitor-interface Vlan11DMZBackup
monitor-interface Vlan12DMZShare
monitor-interface Vlan13DMZAVI
monitor-interface Vlan20DMZENG
monitor-interface Vlan21DMZExternal
no monitor-interface LinkToEnterPriseCore2
no monitor-interface LinkToEnterpriseCore1
icmp unreachable rate-limit 1 burst-size 1
icmp permit any LinkTock
icmp permit any management
icmp permit any LinkToCore
icmp permit any LinkToDMZ
icmp permit any Vlan10DMZSQL
icmp permit any Vlan11DMZBackup
icmp permit any Vlan12DMZShare
icmp permit any Vlan13DMZAVI
icmp permit any Vlan20DMZENG
icmp permit any Vlan21DMZExternal
icmp permit any LinkToEnterPriseCore2
icmp permit any LinkToEnterpriseCore1
no asdm history enable
arp timeout 14400
access-group LinkTock_access_in in interface LinkTock
access-group LinkTock_access_out out interface LinkTock
access-group LinkToCore_access_in in interface LinkToCore
access-group LinkToCore_access_out out interface LinkToCore
access-group LinkToDMZ_access_in in interface LinkToDMZ
access-group LinkToDMZ_access_out out interface LinkToDMZ
access-group Vlan10DMZSQL_access_in in interface Vlan10DMZSQL
access-group Vlan10DMZSQL_access_out out interface Vlan10DMZSQL
access-group Vlan11DMZBackup_access_in in interface Vlan11DMZBackup
access-group Vlan11DMZBackup_access_out out interface Vlan11DMZBackup
access-group Vlan12DMZShare_access_in in interface Vlan12DMZShare
access-group Vlan12DMZShare_access_out out interface Vlan12DMZShare
access-group Vlan13DMZAVI_access_in in interface Vlan13DMZAVI
access-group Vlan13DMZAVI_access_out out interface Vlan13DMZAVI
access-group Vlan20DMZENG_access_in in interface Vlan20DMZENG
access-group Vlan20DMZENG_access_out out interface Vlan20DMZENG
access-group Vlan21DMZExternal_access_in in interface Vlan21DMZExternal
access-group Vlan21DMZExternal_access_out out interface Vlan21DMZExternal
access-group LinkToEnterPriseCore2_access_in in interface LinkToEnterPriseCore2
access-group LinkToEnterPriseCore2_access_out out interface LinkToEnterPriseCore2
access-group LinkToEnterpriseCore1_access_in in interface LinkToEnterpriseCore1
access-group LinkToEnterpriseCore1_access_out out interface LinkToEnterpriseCore1
access-group global_access global
route LinkTock 0.0.0.0 0.0.0.0 10.240.29.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
no user-identity enable
user-identity default-domain LOCAL
http server enable
http 10.240.20.0 255.255.255.0 Vlan20DMZENG
http 10.240.32.0 255.255.255.0 LinkToCore
http 10.240.29.0 255.255.255.0 LinkTock
http 192.168.100.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt connection tcpmss 0
telnet 10.240.29.0 255.255.255.0 LinkTock
telnet 192.168.100.0 255.255.255.0 management
telnet 10.240.32.0 255.255.255.0 LinkToCore
telnet 10.240.20.0 255.255.255.0 Vlan20DMZENG
telnet timeout 5
ssh timeout 5
console timeout 0
no threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
!
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:*
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 12:49 AM
We have done a test by replacing the w2008r2 router by a 'normal' virtual machine with IP 10.240.29.1 and gateway 10.240.29.2.
This did not work (no pings possible, vmware uses a standard virtual switch on the ethernet port).
When we plugged in a laptop with the same settings, it worked.
When we plugged the laptop in a managed 2960x switch and connected that to the firewall, it worked.
If we used another laptop in that switch, with different MAC, same ip settings, it worked.
When we tried the orgininal laptop again using the switch, it failed!
2nd laptop via switch... worked.
Orginal laptop directly... worked.
Orginal laptop via switch... fails.
2nd laptop via switch... works.
reboot 1st laptop, keep in switch, keeps failing.
put in firewall, works again.
Put in switch, works again.
Has this to do with MAC address security somewhere?
Or with settings on the laptops?
Can this cause the problem? This is getting really strange.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:36 AM
Do you have port security configured on the switch? Would help to see the config of the switch that the PC is connected to when it fails.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:12 AM
Could you also post the switch configuration please.
First off, I am curious as to why you have outgoing ACLs configured on each interface? This is not needed, and are very seldom used. I would suggest removing them.
Could you please issue the following command and post back the results.
packet-tracer input Vlan20DMZENG tcp 10.240.20.11 12345 10.240.29.1 80
packet-tracer input LinkTock tcp 10.240.29.1 12345 10.240.20.11 80
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:14 AM
Also from the ASA are you able to ping 10.240.29.1?
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:32 AM
I can ping the 10.240.29.1 from the ASA (telnet).
I can even ping the 192.168.0.0/23 from the ASA.
Thank you for your anser I will try your suggestion immediately.
I have also done some updates on my latest post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:45 AM
Hi,
The configuration seems pretty basic as all the source networks behind this firewall are directly connected and only the default route is needed towards the router in front of the ASA.
Just incase I would suggest adding this as you seem to lack it
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect icmp
inspect icmp error
service-policy global_policy global
And as Marius said, "out" / outbound ACLs aren't really not needed they just add complexity. In your case you also have a Global ACL that I tend not to use at all.
The "packet-tracer" command should pretty much tell you if there is a problem on the ASA but on a quick look it seems you are permitting traffic in any possible direction. You have also enabled traffic from same "security-level" interfaces and you are not performing any NAT on any of the networks.
So I am not sure what the ASA would be doing if it was blocking some traffic.
You could for example capture ICMP traffic on the "external" interface of the firewall and see if any of the hosts traffic is getting through the firewall and if they receive a reply
For example
access-list ICMP-CAP permit icmp
access-list ICMP-CAP permit icmp 192.168.0.0 255.255.254.0
capture ICMP-CAP type raw-data access-list ICMP-CAP interface LinkTock buffer 10000000 circular-buffer
In the place of
You could then use the following command to check if anything is captured after using ICMP
show capture
You can show the actual contents of the capture with the command
show capture ICMP-CAP
You can copy the capture to your computer so you can view it with Wireshark for example with the command
copy /pcap capture:ICMP-CAP tftp://x.x.x.x/ICMP-CAP.pcap
You can remove the capture and the captured data with the command
no capture ICMP-CAP
You will have to remove the ACL separately
Hope this helps
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:44 AM
OK I ran your commands while the firewall was connected to the failing "w2008r2 router" virtual machine.
While running this script, a ping from 10.240.10.11 was running to 10.240.29.1, which kept failing.
User Access Verification
Password:
Type help or '?' for a list of available commands.
ftw01> enable 15
Password: *************
ftw01# packet-tracer input vlan10dmzsql tcp 10.240.10.11 12345 10.240.29.1 $
Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 10.240.29.0 255.255.255.0 LinkTock
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group Vlan10DMZSQL_access_in in interface Vlan10DMZSQL
access-list Vlan10DMZSQL_access_in extended permit tcp any any log debugging
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10036, packet dispatched to next module
Result:
input-interface: Vlan10DMZSQL
input-status: up
input-line-status: up
output-interface: LinkTock
output-status: up
output-line-status: up
Action: allow
ftw01# packet-tracer input LinkTock tcp 10.240.29.1 12345 10.24$
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 10.240.10.0 255.255.255.0 Vlan10DMZSQL
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group LinkTock_access_in in interface LinkTock
access-list LinkTock_access_in extended permit tcp any any log debug
ging
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10075, packet dispatched to next module
Result:
input-interface: LinkTock
input-status: up
input-line-status: up
output-interface: Vlan10DMZSQL
output-status: up
output-line-status: up
Action: allow
Type help or '?' for a list of available commands.
ftw01> enable 15
Password: *************
ftw01# packet-tracer input vlan10dmzsql tcp 10.240.10.11 12345 10.240.29.1 $Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 10.240.29.0 255.255.255.0 LinkTockPhase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group Vlan10DMZSQL_access_in in interface Vlan10DMZSQL
access-list Vlan10DMZSQL_access_in extended permit tcp any any log debugging
Additional Information:Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:Phase: 4
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:Phase: 6
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10036, packet dispatched to next moduleResult:
input-interface: Vlan10DMZSQL
input-status: up
input-line-status: up
output-interface: LinkTock
output-status: up
output-line-status: up
Action: allowftw01# packet-tracer input LinkTock tcp 10.240.29.1 12345 10.24$Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access listPhase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 10.240.10.0 255.255.255.0 Vlan10DMZSQLPhase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group LinkTock_access_in in interface LinkTock
access-list LinkTock_access_in extended permit tcp any any log debug
ging
Additional Information:Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:Phase: 5
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10075, packet dispatched to next moduleResult:
input-interface: LinkTock
input-status: up
input-line-status: up
output-interface: Vlan10DMZSQL
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 01:47 AM
From the output of the packet tracer. traffic is allowed through the ASA, atleast on port 80. But since you have permit IP any any everywhere we can safely assume ICMP is also permitted.
I would start looking closer at the switch or even the PC you are testing from that is failing for the problem.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 02:02 AM
We added the laptop (10.240.29.1 GW 10.240.29.2) to the switch, and were in a failing configuration (we could not ping from 10.240.10.11 to 10.240.29.1)
Then, we started a ping from the laptop to the other, so started a ping from 10.240.29.1 to 10.240.10.11, this worked.
After this, the ping from 10.240.10.11 to 10.240.29.1 started succeeding, without any config change ???
Does this sound like ARP problems?
Thanks for your input we are really using this.
The switch has no security-port settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 02:21 AM
I think this might have been an ARP issue. Has the IP you are testing from been associated with another PC recently?
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 02:27 AM
Hello,
"Has the IP you are testing from been associated with another PC recently?"
Actually we are constantly changing the 10.240.29.1 and 10.240.29.2 'hosts'.
In the initial setup, the .2 is on a 3750X and the .1 is on the w2008router, no problems.
In the 'new' setup, the .2 is on the firezall and the .1 is on the w2008router, problems.
If we set the .1 on a laptop it will work, but when we start changing the laptop and using a switch between, it starts failing again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2014 02:31 AM
try issuing a clear arp on the ASA
and clear ip arp (or you might have to go as far as issuing a clear arp-cache) on the switch and router
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




